Method and terminal for setting permission of application and controlling restricted region
A technology of limited area and authority, applied in electrical components, transmission systems, digital data authentication, etc., can solve the problems of easy operation by others, misoperation, malicious operation terminal high-value applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to facilitate the understanding of the present invention, specific examples will be given below for further description.
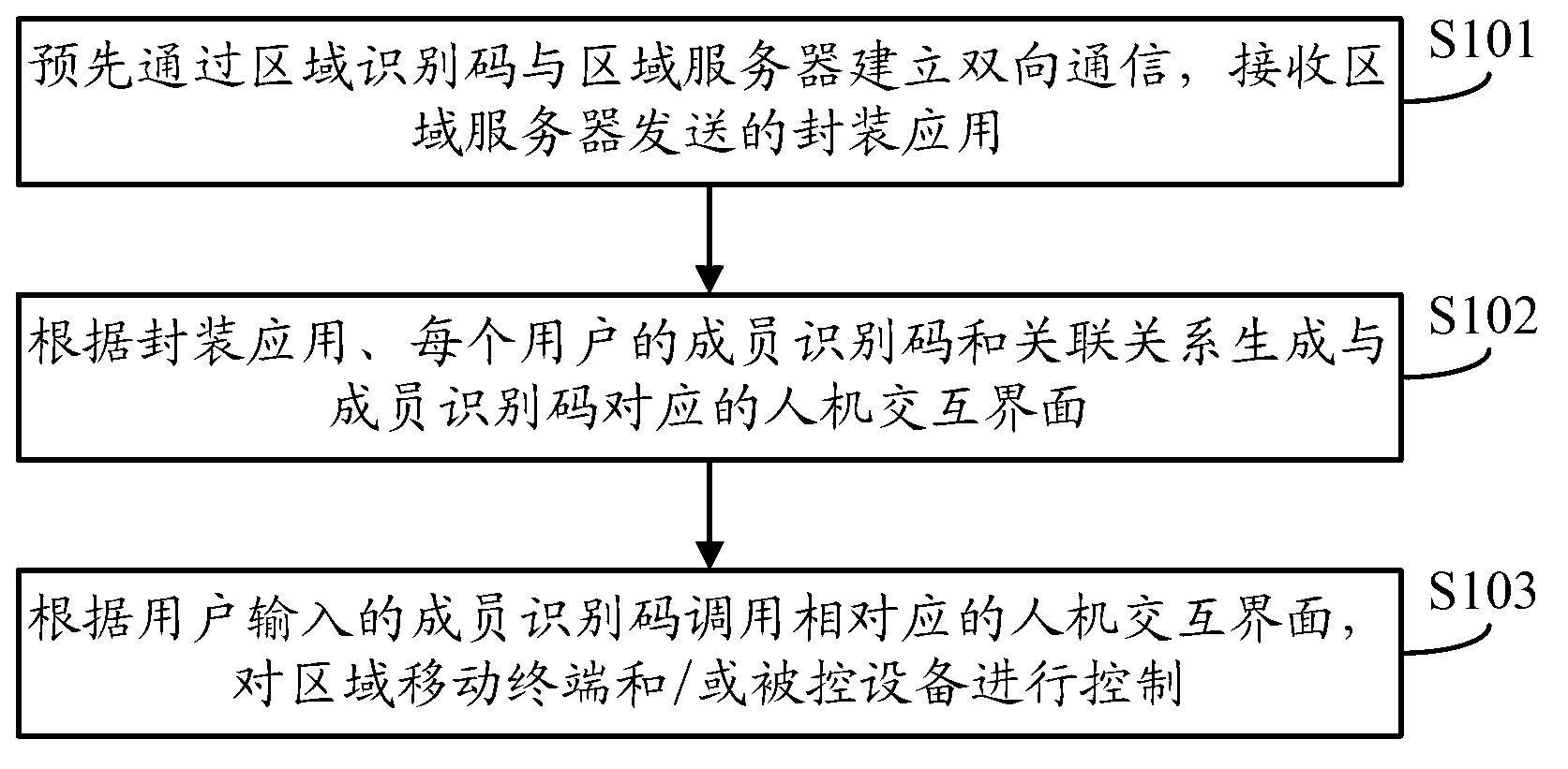
[0045] The first embodiment of the present invention provides a method for setting application permission and controlling a limited area, such as figure 1 As shown, the steps are as follows:
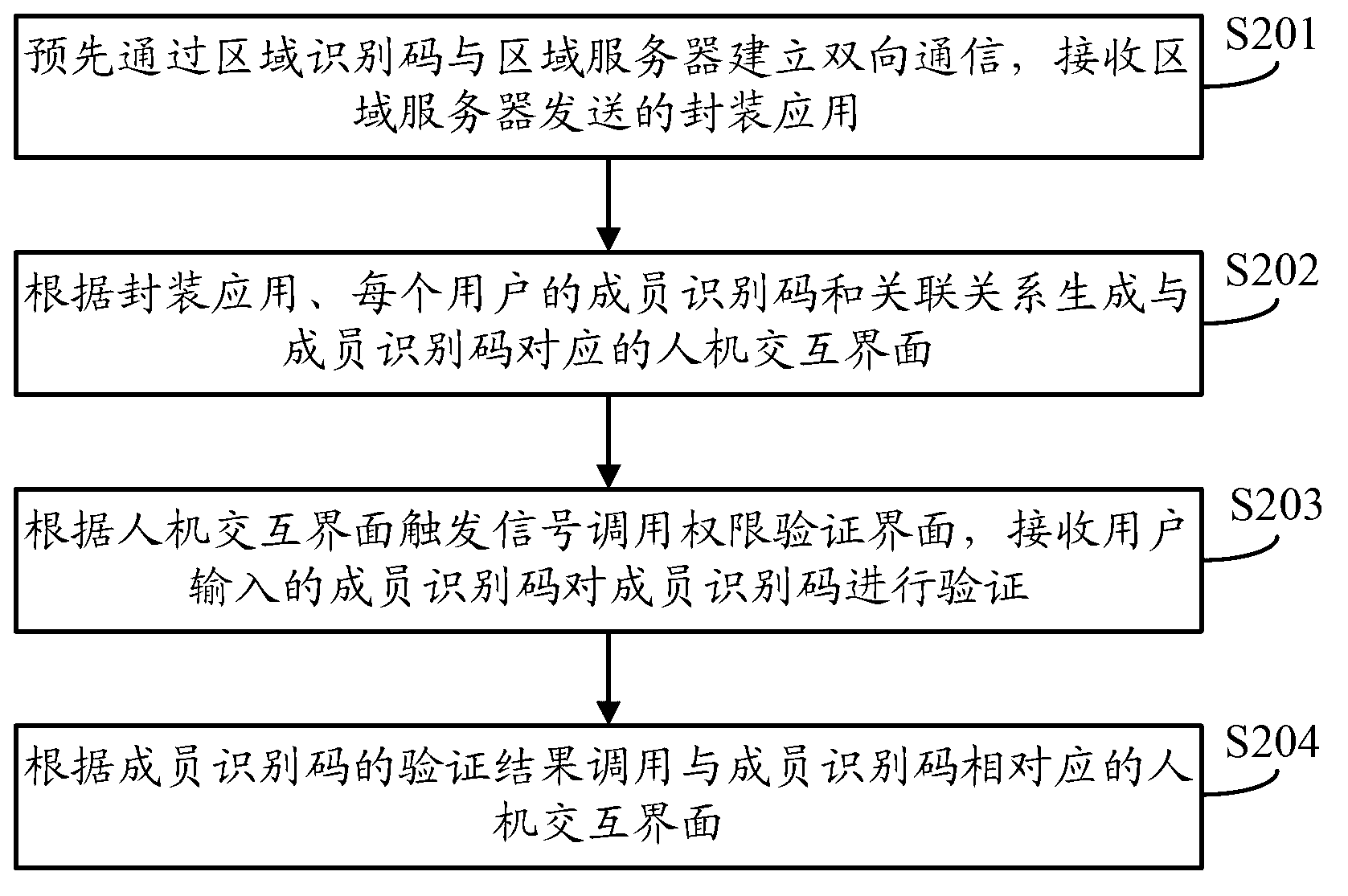
[0046] In step S101, two-way communication is established with the regional server through the regional identification code in advance, and the packaged application sent by the regional server is received.
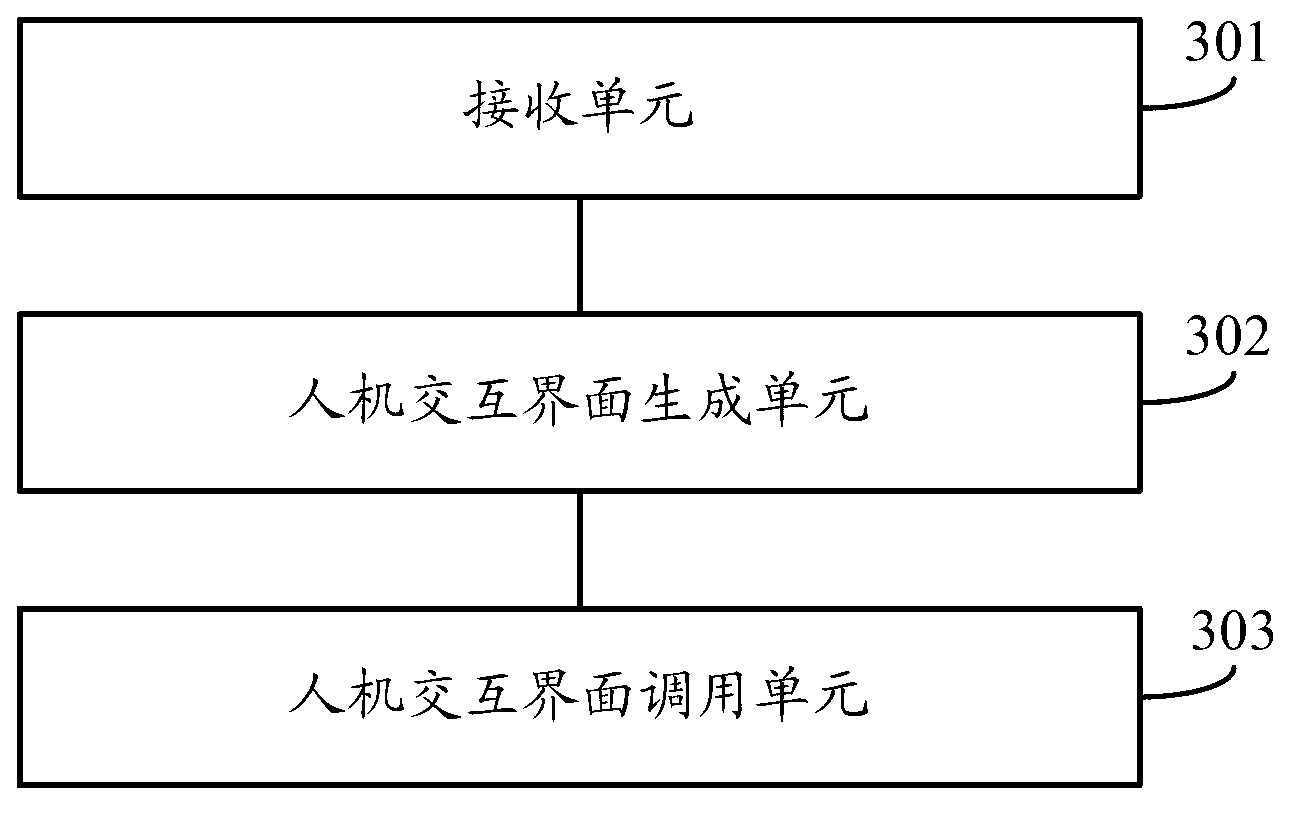
[0047]Step S102, generate a human-computer interaction interface corresponding to the member identification code according to the authority association relationship between the packaged application, the member identification code of each user in the multi-user, and the corresponding operation authority. The human-computer interaction interface includes at least one icon, the icon Used to identify regional mobile terminals, controlled devices and / ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com