Application program protection method and equipment
An application and device protection technology, applied in the field of software protection, can solve problems such as unfavorable application copyright protection, and achieve the effect of being beneficial to copyright protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
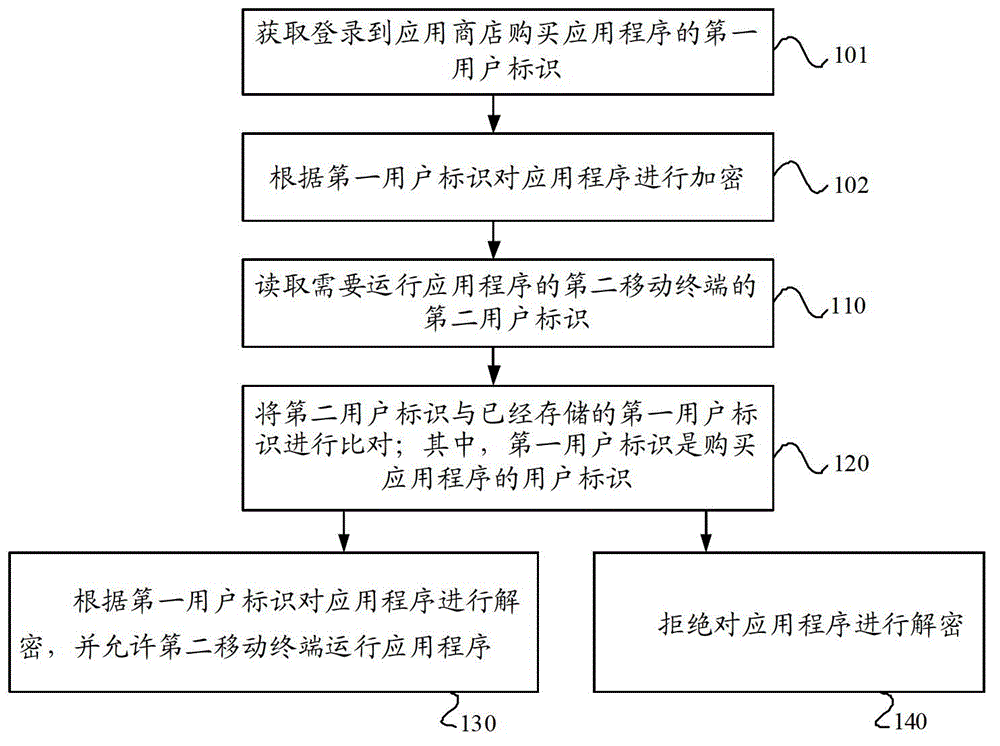
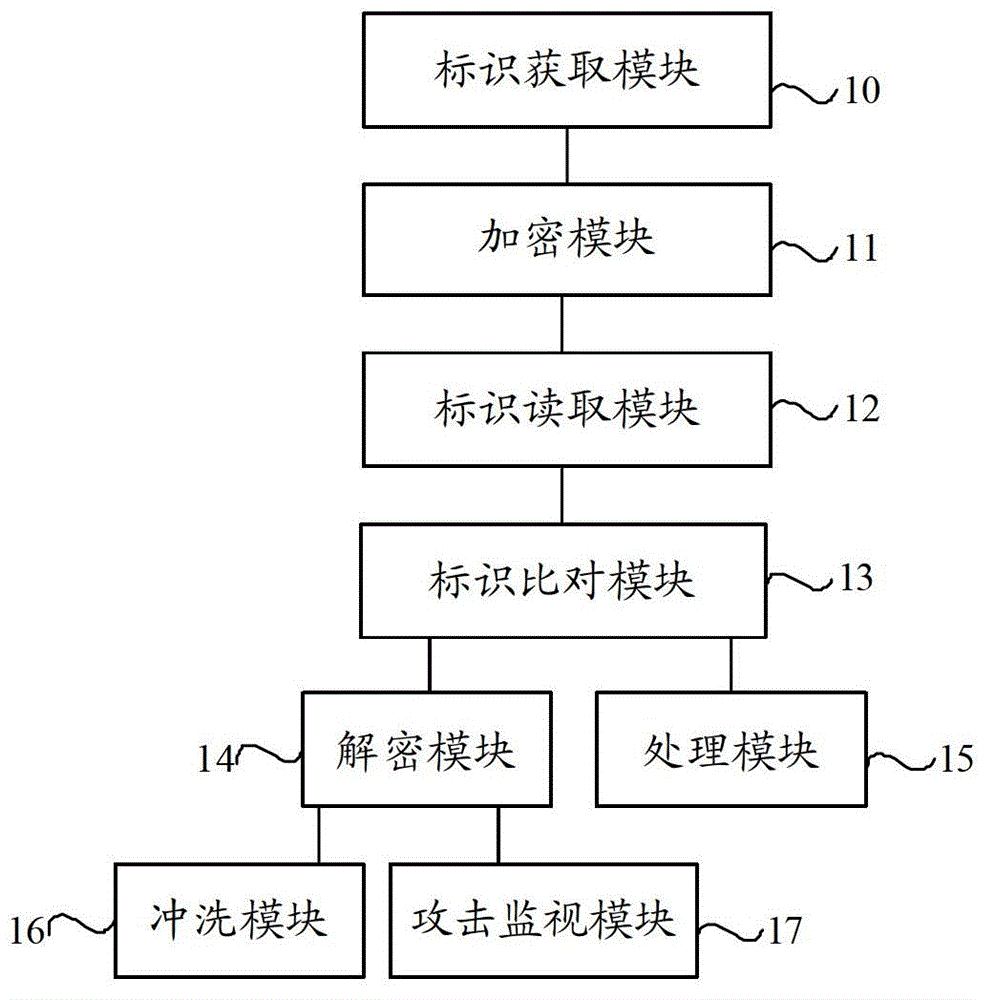
[0018] In the prior art, the encryption of the application is usually done on the developer side, and the encryption methods are different, which increases the workload of the developer; at the same time, the application encrypted by the existing technology can be transferred and installed after it is successfully cracked once. Using it in other terminals seriously infringes the developer's copyright rights and interests, and is not conducive to the unified charging management of the application by the application store. figure 1 It is a schematic flow chart of an application protection method provided by an embodiment of the present invention, such as figure 1 As shown, this embodiment provides an application protection method, including:
[0019] Step 110: Read the second user identifier of the second mobile terminal that needs to run the application.
[0020] Specifically, after a certain second mobile terminal obtains the application, when it needs to run the application, first ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com