Method and system for authenticating network conference
A network conference and authentication method technology, applied in the field of network conference certification, can solve the problem of personal information theft, achieve the effect of meeting member certification and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0010] Hereinafter, the present invention will be described in detail with reference to the drawings and examples. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
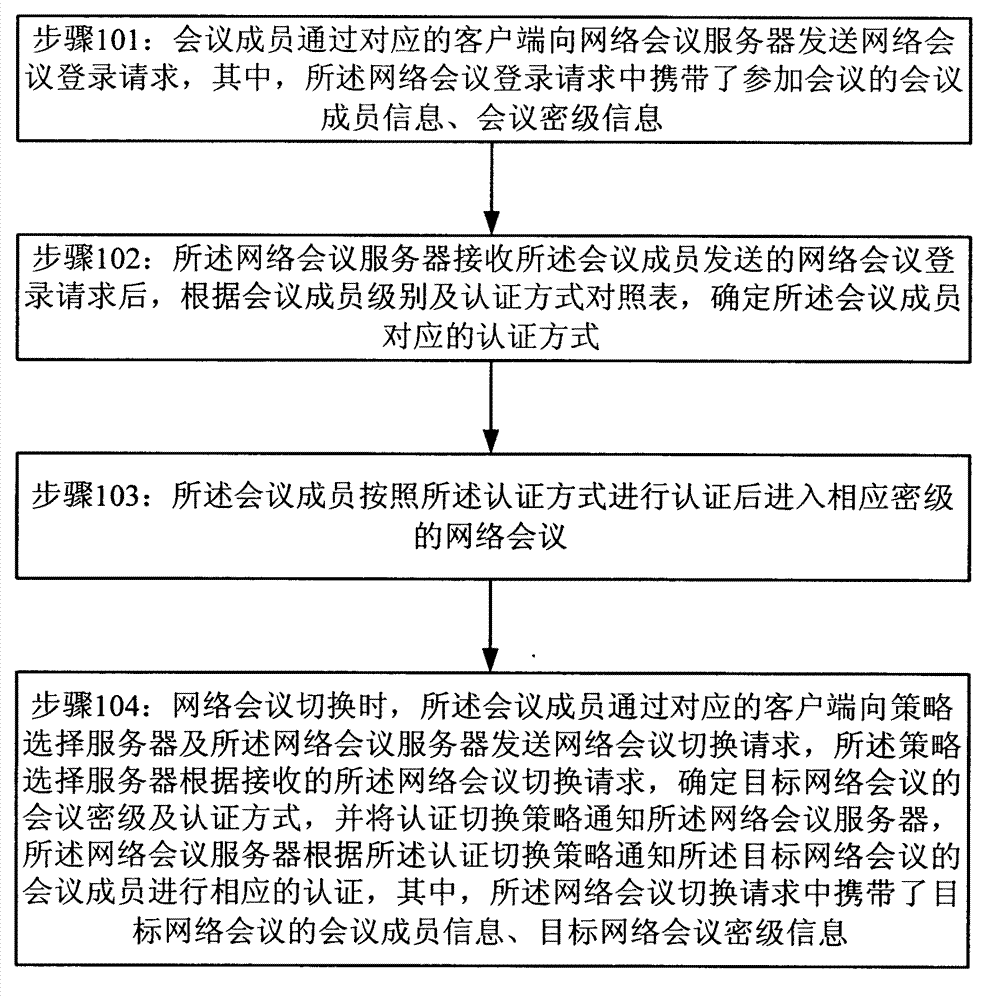
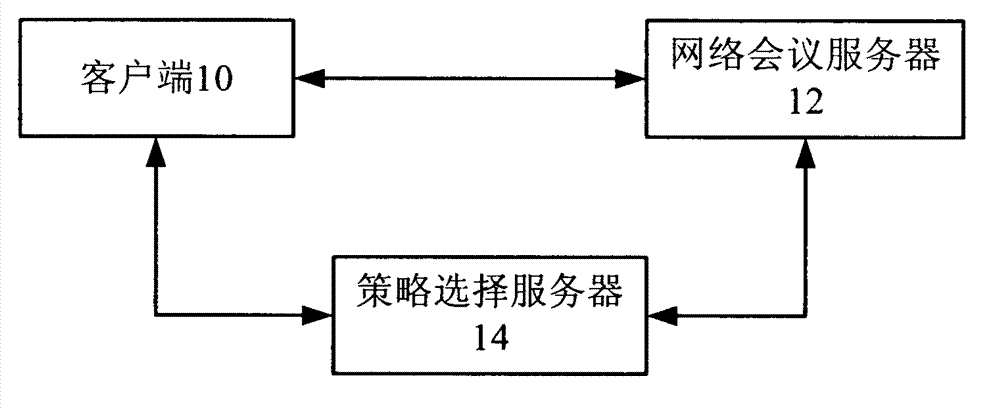
[0011] figure 1 Shown is a flow chart of a method for network conference authentication provided according to a preferred embodiment of the present invention. like figure 1 As shown, the network conference authentication method provided by the preferred embodiment of the present invention includes steps 101-104.
[0012] In step 101, the conference members send a web conference login request to the web conference server through the corresponding client, wherein the web conference login request carries the information of the conference members participating in the conference and the conference confidentiality information. Here, the conference member information includes, for example, conference mem...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap