Rootkit behavior identification method based on multidimensional across view
An identification method and view technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as inability to guarantee reliability and comprehensiveness, inability to identify rootkit behavior characteristics, inability to apply system dynamic data detection, etc., to increase reliability and comprehensiveness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to better illustrate the purpose and advantages of the present invention, the implementation of the method of the present invention will be further described in detail below in conjunction with examples.
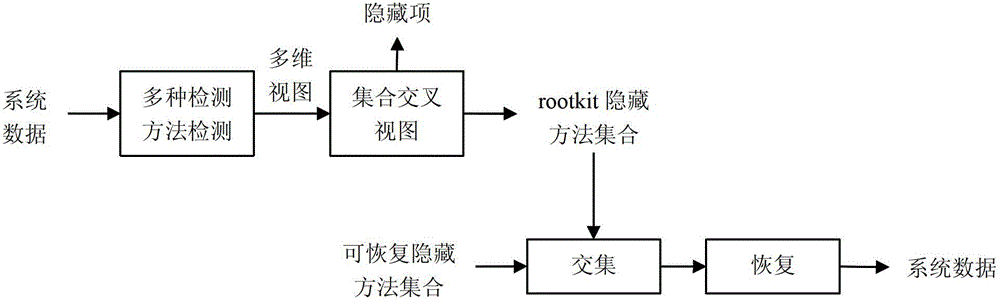
[0021] The embodiment of the present invention is described by taking the rootkit hidden process in the windows operating system as a detection item. Let A 1 It is a detection method based on hardware virtualization to obtain hidden processes through the cr3 register, and the obtained cross view is P 1 ; Let A 2 It is a detection method based on intercepting the SwapContext thread scheduling function to obtain hidden processes, and the obtained cross view is P 2 , and the corresponding avoidance method is H 2 ; Let A 3 It is a hidden process detection method based on HSC (intercepting system calls), and the obtained cross view is P 3 , and the corresponding avoidance method is H 3 ; Let A 4 is a hidden process detection method based on memory search, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com