Automatic detection method for Android malicious software
An automatic detection and malicious software technology, applied in the field of system security, can solve problems such as difficult automatic triggering of malicious behaviors, and achieve strong coverage and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] A method and system for automatically detecting Android malware will be described in detail below with reference to the accompanying drawings, but the present invention is not limited to the following embodiments.
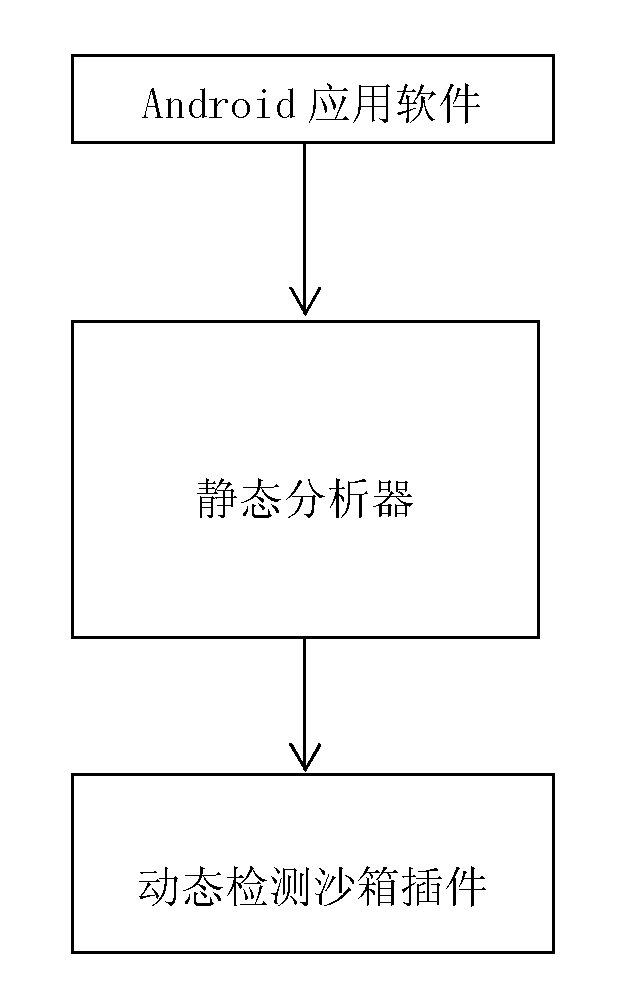
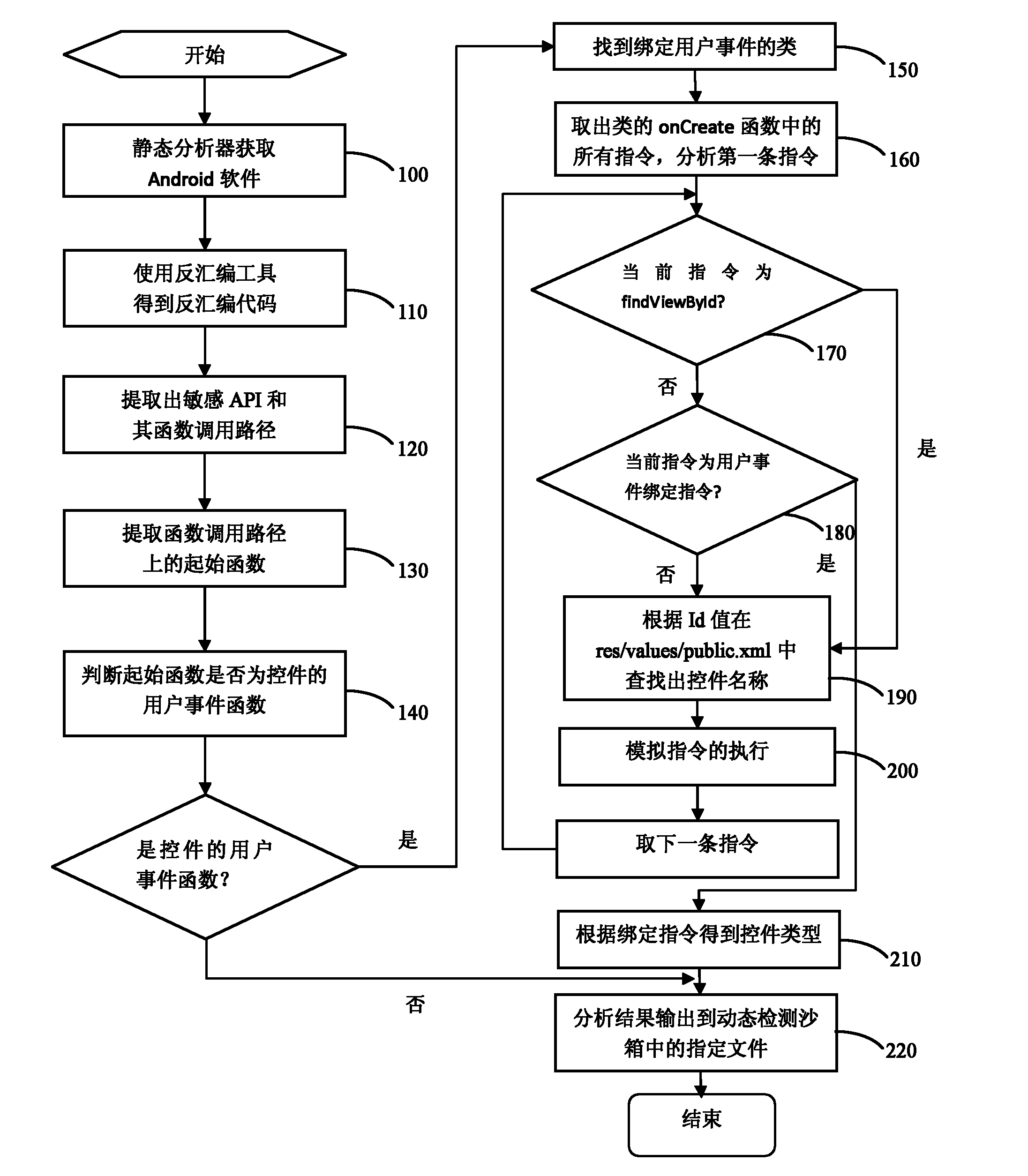
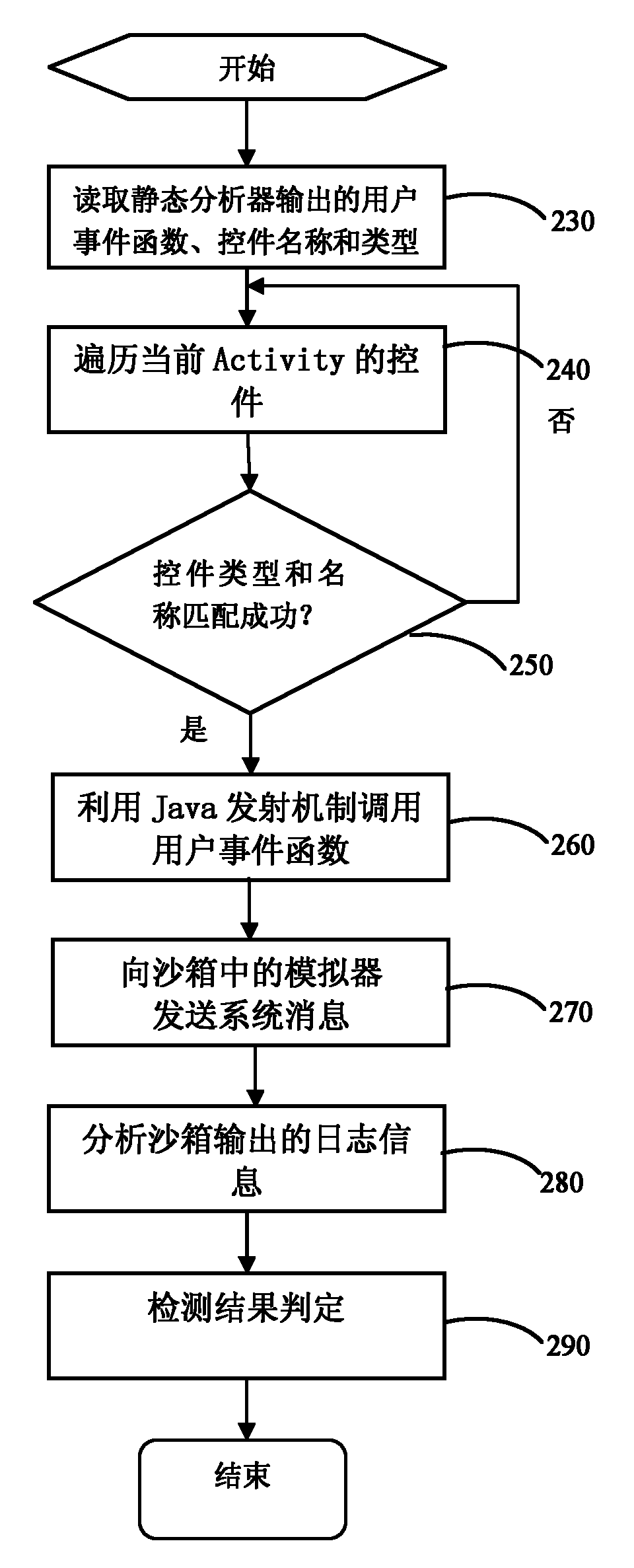
[0033] The overall structure of the present invention is as figure 1 As shown, the present invention mainly includes two parts structurally: a static analyzer and a dynamic detection sandbox plug-in. The static analyzer disassembles the Android application software to obtain the disassembled code, and then statically analyzes the sensitive API contained in the software to determine the way to trigger the sensitive API. For the sensitive API triggered by the user's operation on the control, the user event function should be further analyzed, and the control type and name associated with it should be statically analyzed according to the user event function, and the analysis results will be output to the specified dynamic detection sandbox in the file. The dy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com