Intelligent network alarm system and implementation method thereof
An alarm system and intelligent networking technology, applied to alarms, anti-theft alarms, instruments, etc., can solve the problems of single alarm mode and cannot really identify whether it is illegal intrusion, so as to reduce electrical wiring, save installation space, and protect safety Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
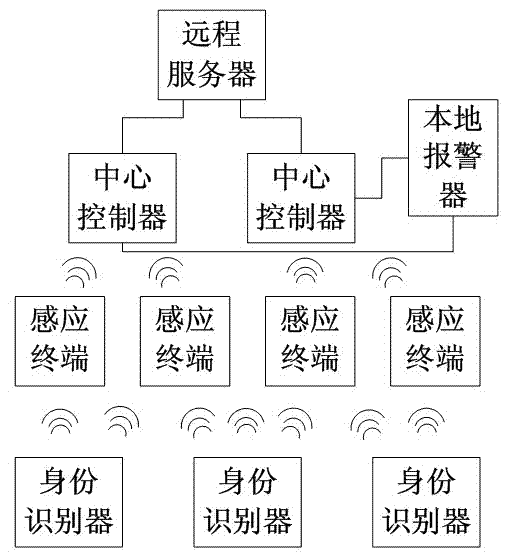
[0049] Such as figure 1 The present invention shown includes five parts: remote server, central controller, sensing terminal, local alarm, and identification device. Among them, the remote server is used for control and management, and can be connected to multiple central controllers. In this embodiment, the central control There are two sensors, each central controller has two induction terminals wirelessly connected, there are three identification devices and can verify each central controller, and the local alarm is connected to both central controllers, and it is set in the armed area In the nearby security room, the local alarm can also be built into the central controller according to the actual situation, or set up next to the armed area, or in a police station near the armed area.
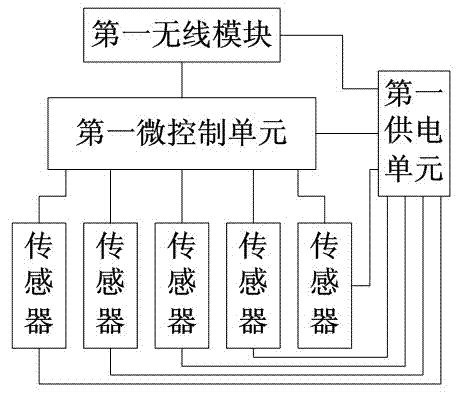
[0050] Such as figure 2 As shown in the sensing terminal, a sensing terminal is usually installed in the center of an arming area, which is convenient for all-round detection of the armin...
Embodiment 2
[0074] Such as Figure 6 Shown is the implementation method of the intelligent networked alarm system. In order to better explain its principle, this embodiment simulates the real scene. The preset environment is as follows: the defense area is the indoor living room, which has the main entrance of the room, windows and bedroom doors. ID recognizer 1, the nanny carries ID recognizer 2, guests and intruders have no ID recognizer, ID recognizer 1 has built-in ID 1 with full-area authorization, ID recognizer 2 has built-in ID 2, and the non-authorized area of ID 2 is the bedroom Near the door, other parts are authorized areas; the sensing terminal is placed on the top of the living room, with no shelter around, the central controller is placed in a hidden place indoors and built-in local alarm 1, local alarm 2 is placed in the security room, and the remote server is placed in the security room. The remote management room, the central controller, two local alarms and the remote ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com