Systems and methods for accessing or managing protected storage
A storage space, asset manager technology, applied in the direction of coinless or similar appliances, lock applications, time registers, etc., can solve the trouble of updating or changing, expensive to operate, not yet tried access, management integration methods, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
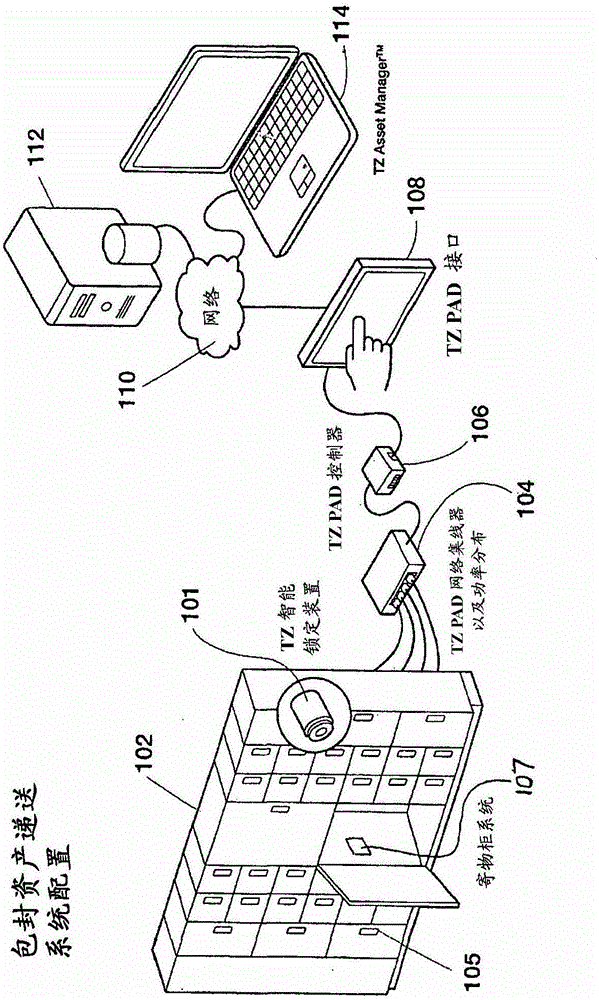
[0067] refer to figure 1 , illustrating an example of a system for packaged asset delivery. The system includes: locker system 102 , network hub 104 , interface controller 106 , data input device 108 , network 110 , memory storage device 112 , and asset manager 114 .
[0068] Locker system 102 is any type of storage device in which one or more storage spaces are secured by one or more locking devices. Each locker has a locking device (eg, an electronic lock) communicatively coupled to the hub 104 . The locking device is actuated by receiving an access code that opens / releases the locking device to allow the barrier protecting the storage space to open to allow access to the storage space. For simplicity, in figure 1Only one locking device 105 is identified in , but it will be understood that each locker has a locking device. It will also be understood that the locking device 105 may be coupled to the hub 104 by any type of connection, such as a wired connection, a wireless...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com