Method for IPSec (Internet protocol security) tunnel to rapidly process messages
A message and tunnel technology, which is applied in the field of network communication, can solve the problems that encrypted messages cannot be processed in session mode, and the processing speed of messages is slow
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
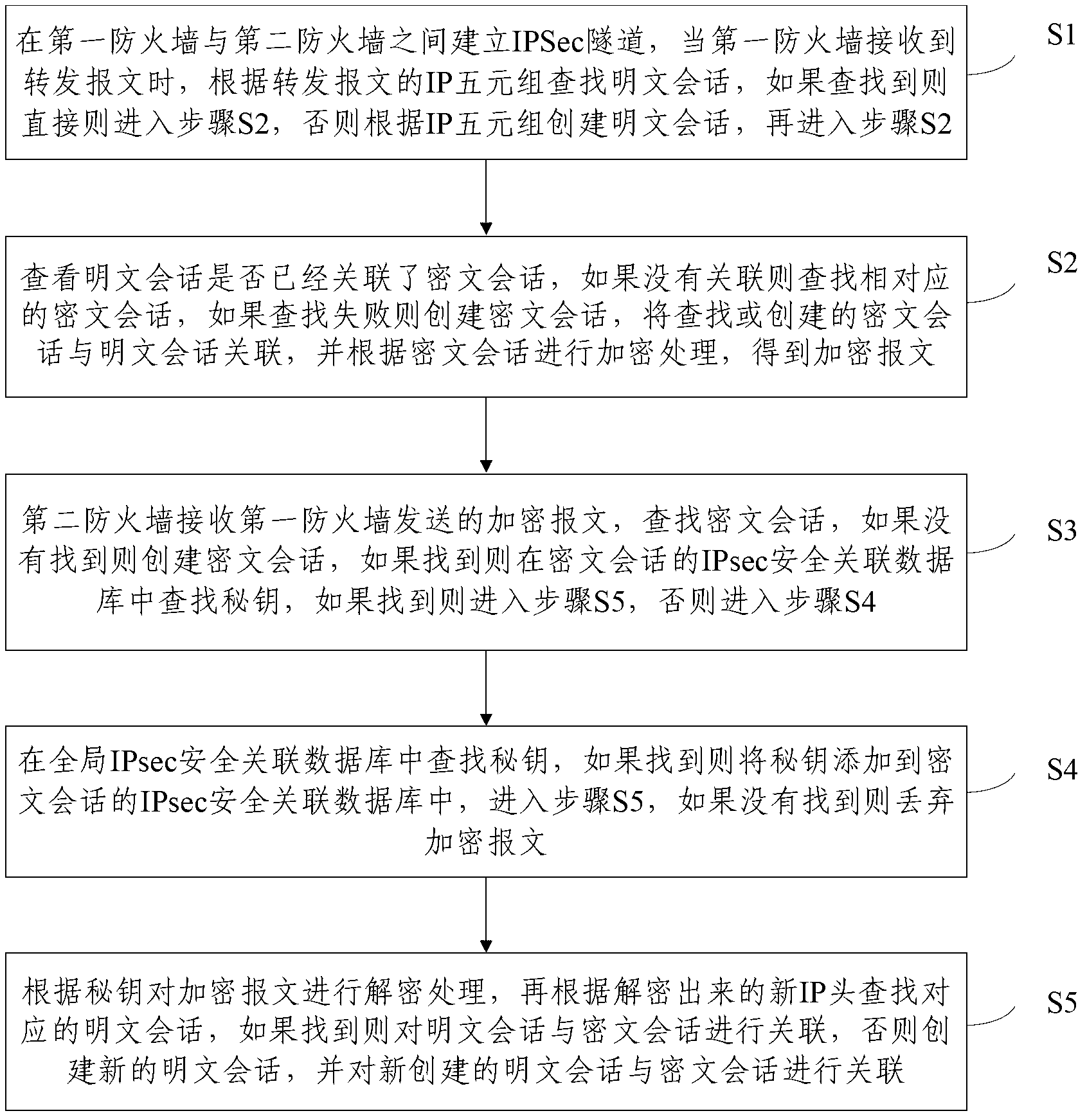
[0024] An embodiment of the present invention provides a method for quickly processing packets through an IPSec tunnel, and the steps are as follows: figure 2 As shown, it specifically includes the following steps:
[0025] Step S1: Establish an IPSec tunnel between the first firewall and the second firewall. When the first firewall receives the forwarded message, it searches for the plaintext session according to the IP quintuple of the forwarded message. If found, it directly proceeds to step S2 , otherwise create a plaintext session according to the IP quintuple, and then go to step S2.
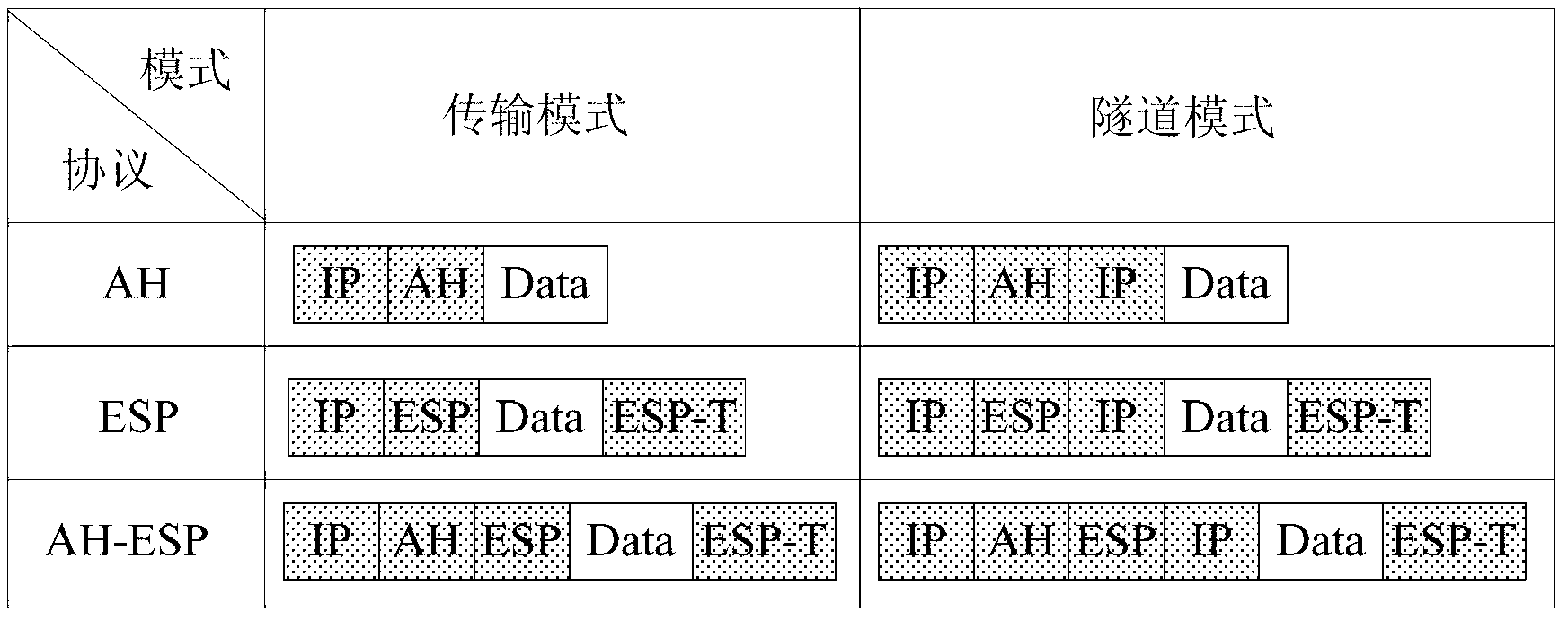
[0026] The encrypted message is an ESP message or an AH message, and the IP qui...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap