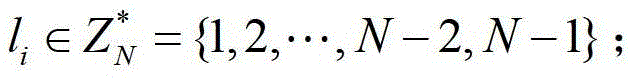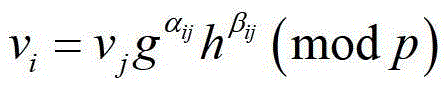Discrete logarithm-based directed transitive signature method
A discrete logarithm and edge signature technology, applied in the field of information security, can solve problems such as low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The discrete logarithm-based directed transfer signature method proposed by the present invention will be described in detail below in conjunction with the accompanying drawings:
[0049] First, a simple flow of the MR02 scheme is given.
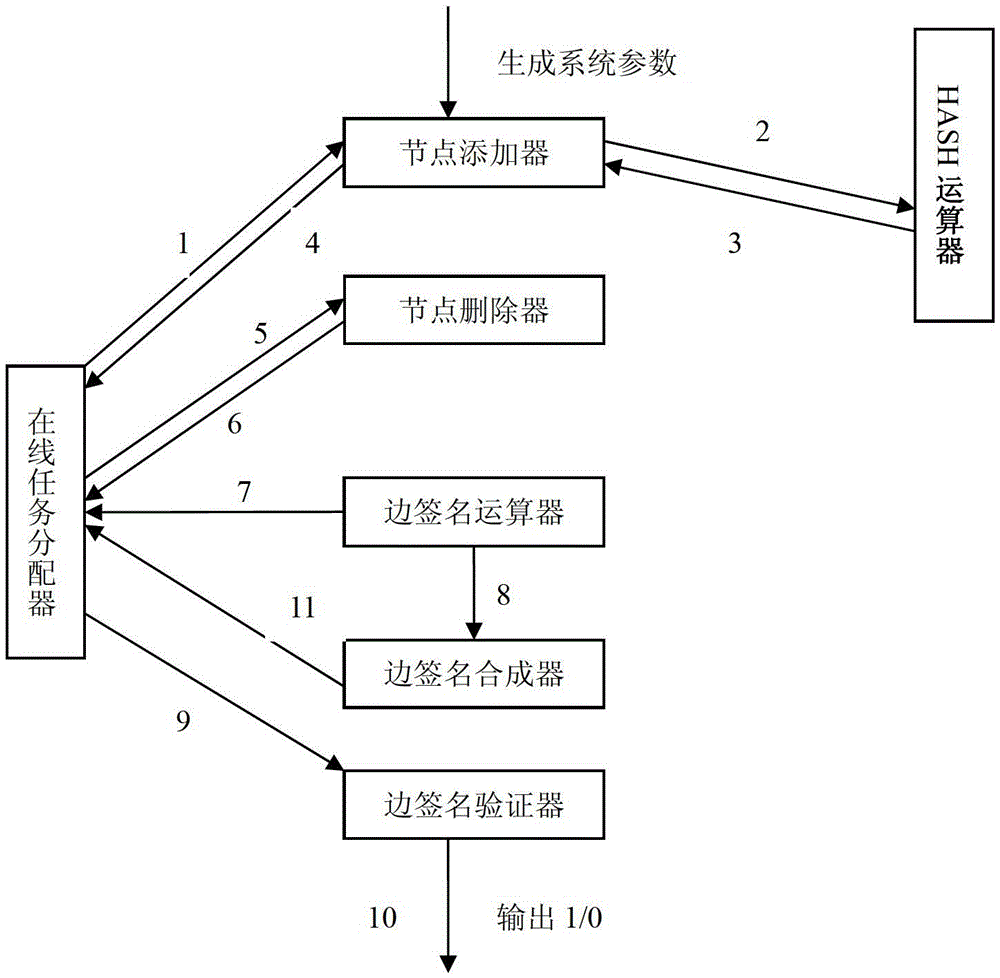
[0050] Such as figure 1 As shown, the directed transitive signature scheme based on discrete logarithm includes system setting, establishment of new nodes, edge signature, edge signature verification, and composite edge signature.
[0051] 1. System settings:
[0052] The signer chooses a standard digital signature scheme for signing nodes, and a pair of public / private key pairs, and publishes the public key. To sign an edge, choose two large prime numbers p and q, satisfying q∣(p-1); choose two generators g, It is computationally infeasible for others to seek h with respect to the discrete logarithm of base g, where Represents the set {1,2,...,p-2,p-1}, where p is a large prime number.
[0053] 2. Create a new node:
[0054] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com