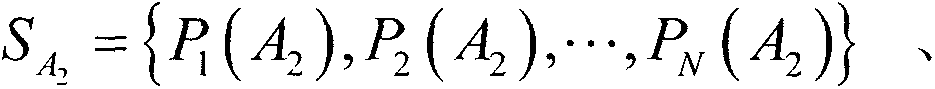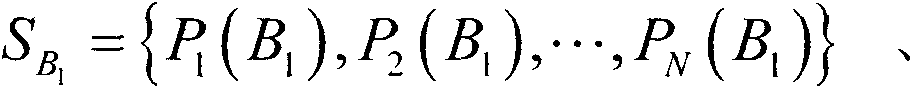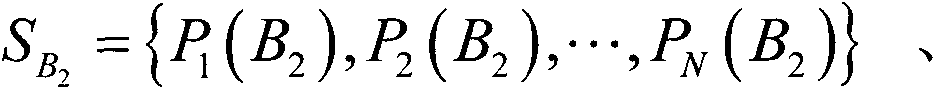Controlled bi-directional quantum secure direct communication protocol free of information leakage
A technology of secure direct communication and information leakage, which is applied in the field of quantum security communication and can solve problems such as information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
preparation example Construction
[0058] S1) Preparation of the initial state: Alice prepares 3N pieces in |Φ + >'s Bell state and divide it into N groups, so that each group has 3 in |Φ + > Bell state (i.e. with ). Moreover, she divided these particles into 6 particle sequences, namely S A 2 = { P 1 ( A 2 ) , P 2 ( A 2 ) , · · · , P N ( A 2 ) } , S B 1 = { P 1 ( ...
Embodiment
[0070] 1. Application example of controlled two-way QSDC protocol
[0071] An example is used to further explain the controlled two-way QSDC protocol of the present invention. Assuming that Alice has 2-bit secret information 11, and Bob has 2-bit secret information 10, take the first particle pair as an example to illustrate the dialogue process. Alice, Bob, and Charlie all use the Bell basis to measure (P 1 (A 1 ), P 1 (A 2 )), (P 1 (B 1 ), P 1 (B 2 )) and (P 1 (C 1 ), P 1 (C 2 )), then after entanglement exchange, (P 1 (A 1 ), P 1 (A 2 )), (P 1 (B 1 ), P 1 (B 2 )) and (P 1 (C 1 ), P 1 (C 2 )) will all start with The probability of collapses to or Without loss of generality, assume that after entanglement exchange (P 1 (A 1 ), P 1 (A 2 )), (P 1 (B 1 ), P 1 (B 2 )) and (P 1 (C 1 ), P 1 (C 2 )) collapses to Alice then Apply unitary operation σ z to encode its own 2-bit secret message, such that it turns...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com