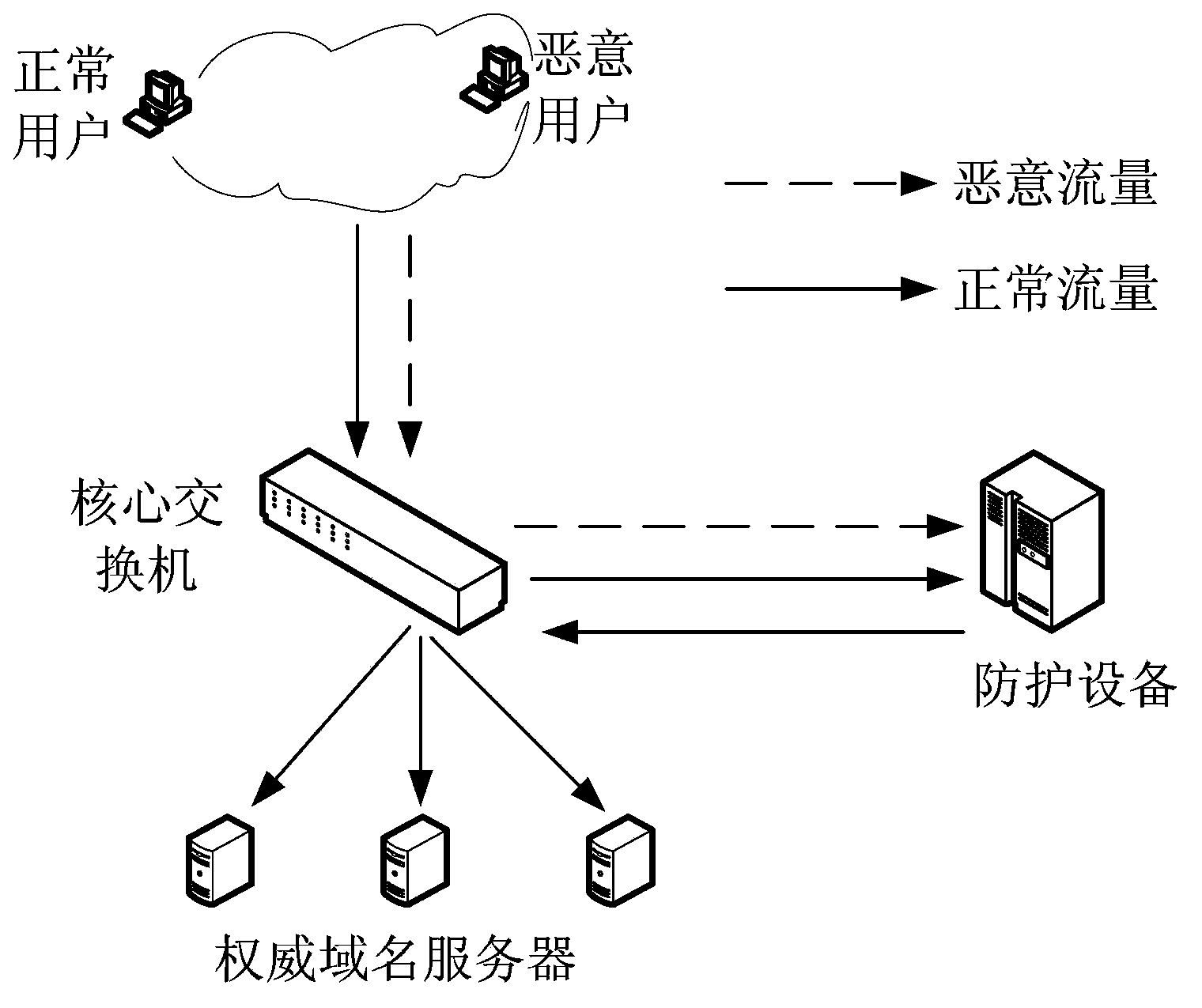
Method and system for detecting false attack sources
An attack source, fake technology, applied in the field of Internet security, it can solve the problems of unable to obtain domain name query results, unable to pass authentication, inconvenient program implementation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The solution of the present invention will be described in detail below in combination with the preferred embodiments thereof.
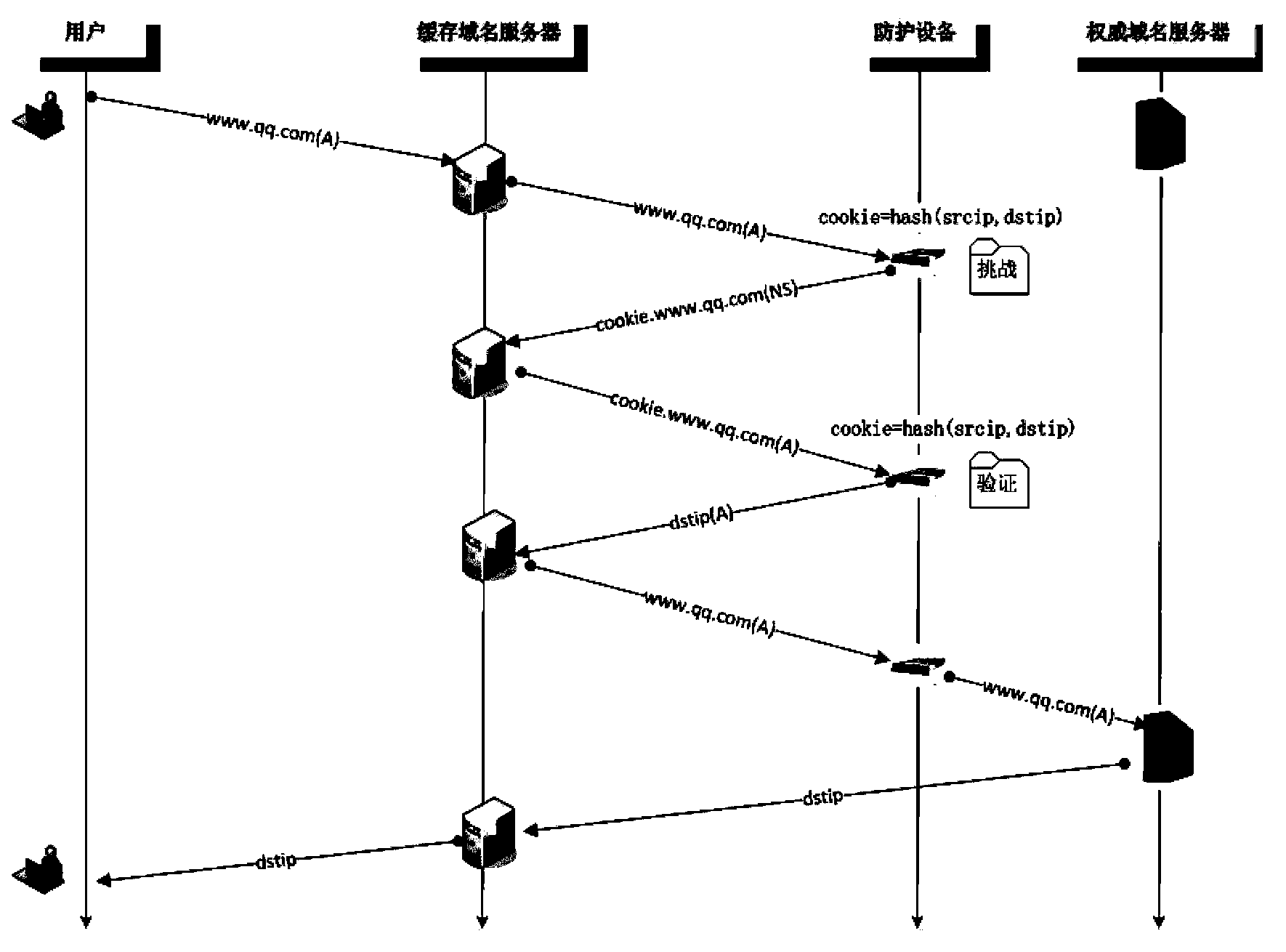
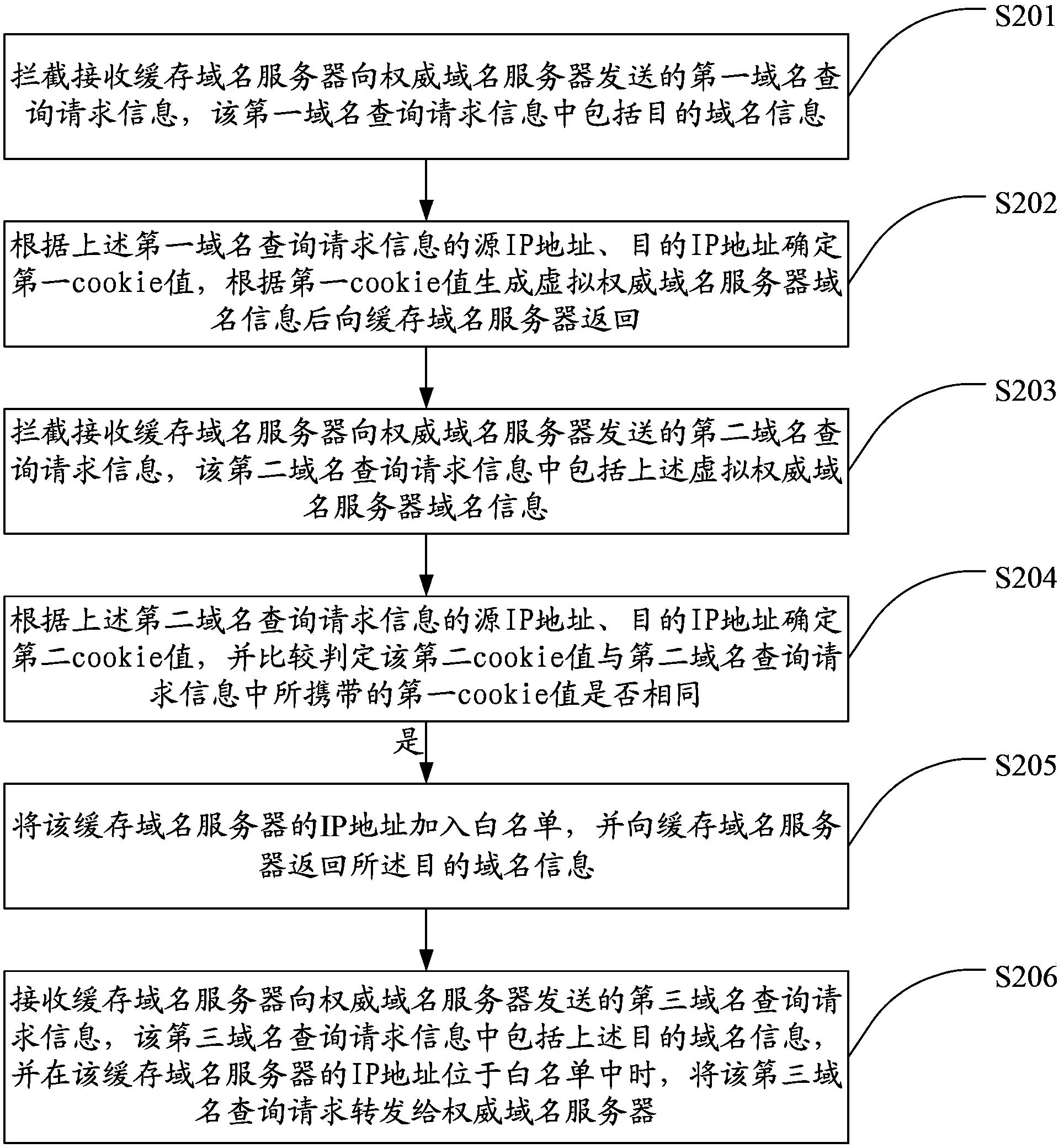
[0022] figure 2 A schematic flowchart of an embodiment of a method for detecting a false attack source of the present invention is shown in . In this embodiment, the further operation and processing process after determining that the two cookie values are the same is used as an example for illustration. Those skilled in the art can know that, in the case of only needing to identify and determine whether it is a false attack source , it is only necessary to determine the cookie value twice, therefore, the description in the following embodiment is not intended to limit the solution of the present invention.
[0023] Such as figure 2 As shown, the method in this embodiment includes steps:
[0024] Step S201: Intercept and receive the first domain name query request information sent to the protected authoritative domain name server, the fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com