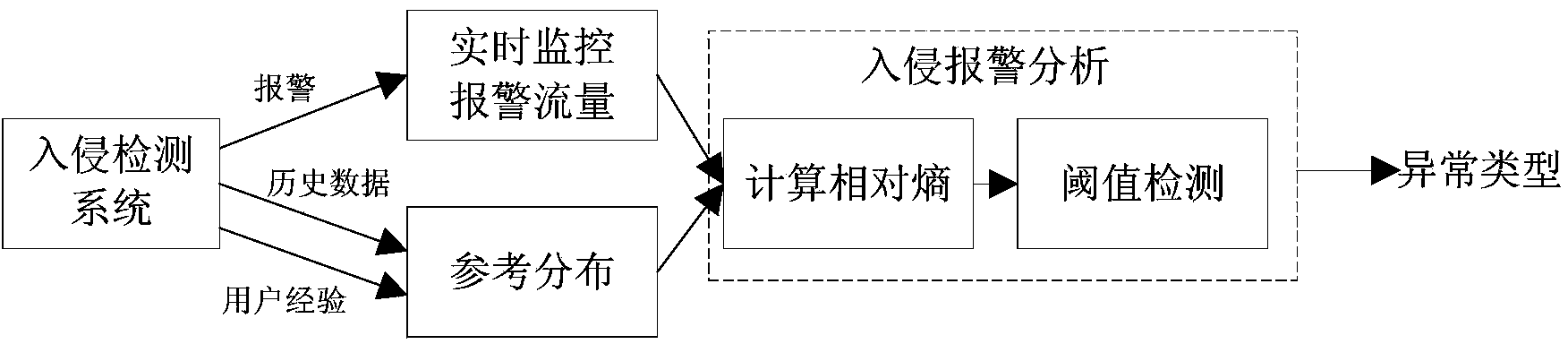
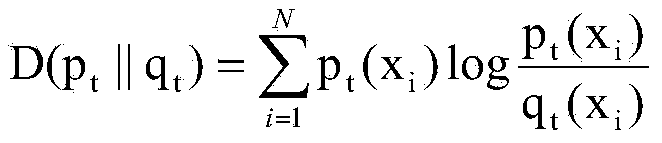Intrusion alarm analyzing method based on relative entropy
A technology of alarm analysis and relative entropy, applied in the field of information security, can solve problems that are not suitable for engineering applications and cannot be effectively distinguished
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solutions of the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. The following examples are implemented on the premise of the technical solutions of the present invention, and detailed implementation methods and processes are given, but the protection scope of the present invention is not limited to the following examples.
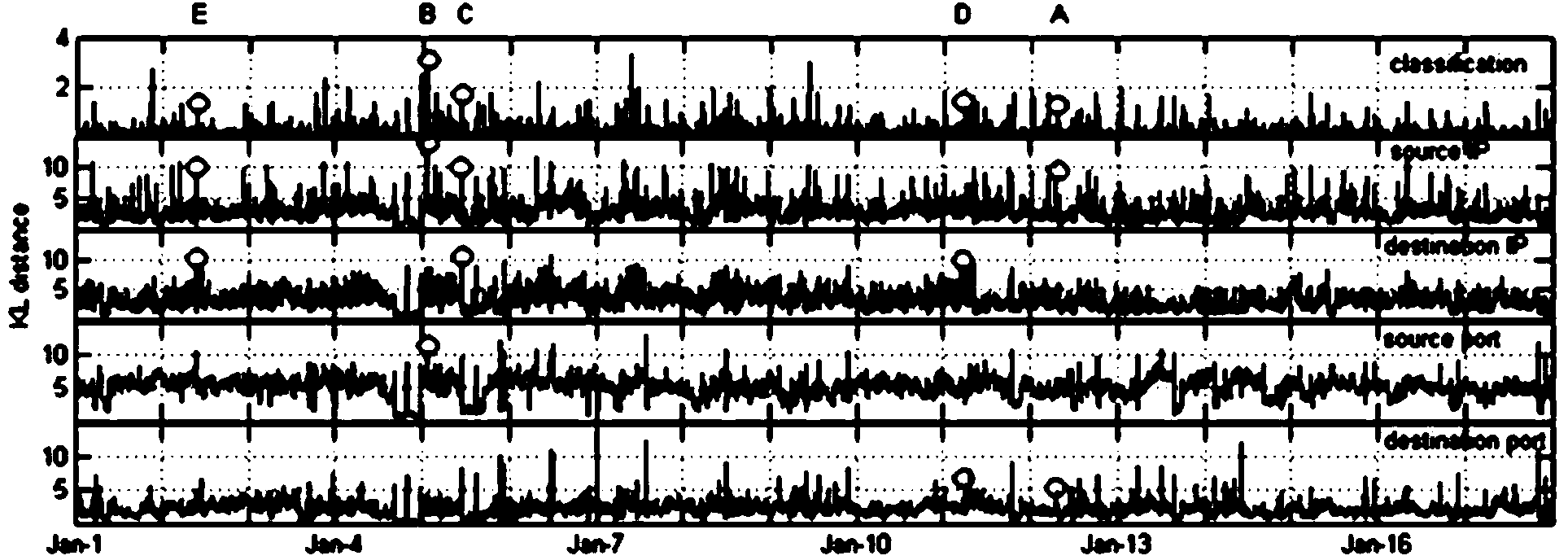
[0039] In order to better understand the method proposed in this embodiment, select the 17-day intrusion detection system IDS alarm that uses the actual network, find network abnormalities based on the distribution of alarm characteristics, and then further analyze the cause of the abnormality for each abnormality. The alarm data set is generated by Snort (version 2.8.3.2) deployed between the internal network and the external network. The data set includes a total of 920,4735 alarms generated by 33,2154 active IP addresses (including intranet and extranet) in 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com