Usb key authentication method and system
An authentication method and authentication system technology, applied in the field of USBkey authentication method and system, can solve the problem of low security and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
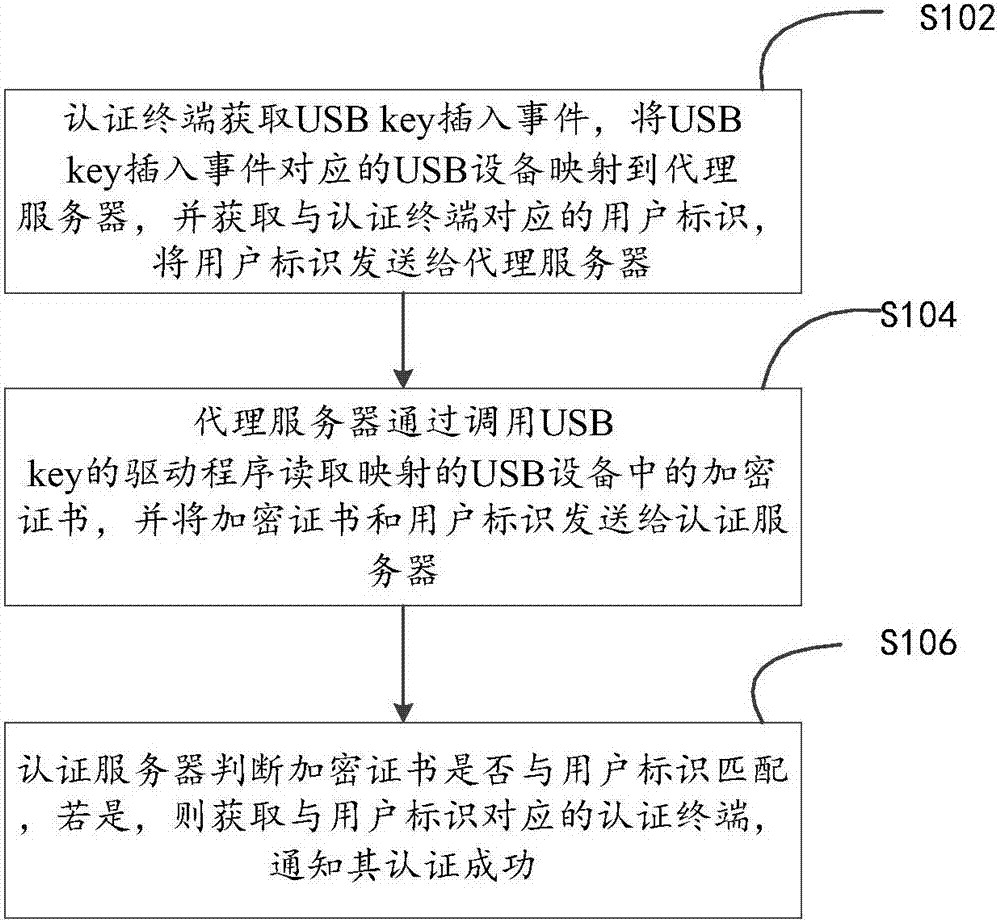
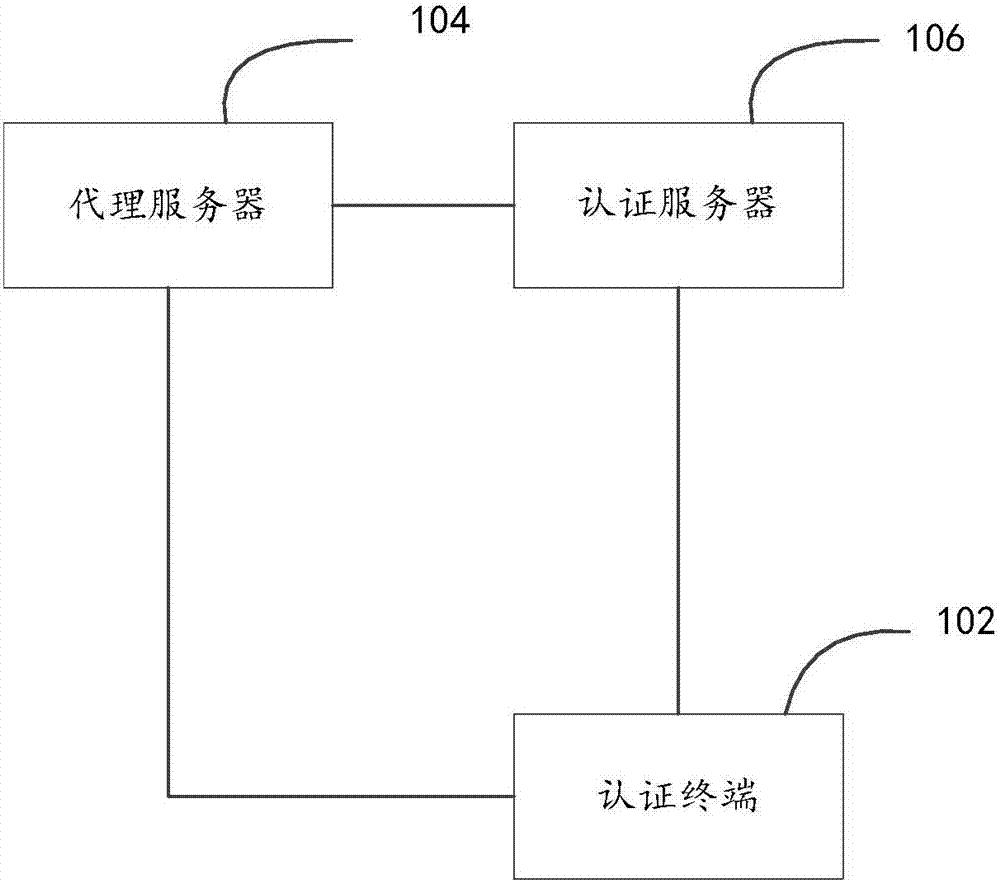
[0035] In one embodiment, such as figure 1 As shown, a USB key authentication method, the method completely depends on the computer program, and the computer program can run on the USB key authentication system based on von Leumann system. The USB key authentication system can be based on a computer system, including an authentication terminal, a proxy server, and an authentication server. Among them, compared with the traditional technology, there is no need to install a USB key driver on the authentication terminal.
[0036] The method includes the following steps:
[0037] Step S102, the authentication terminal obtains the inserted USB device, maps the inserted USB device to the proxy server, obtains the user ID corresponding to the authentication terminal, and sends the user ID to the proxy server.
[0038] When a USB device containing an encrypted certificate is inserted into the authentication terminal, a USB key insertion event can be triggered. The authentication ter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com