Self-adapting-based network port fast scanning method
A network port and fast scanning technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of large number of scanned, consume a lot of time, failure of three-way handshake process, etc., to avoid repeated scanning, Effects of speeding up and reducing numbers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
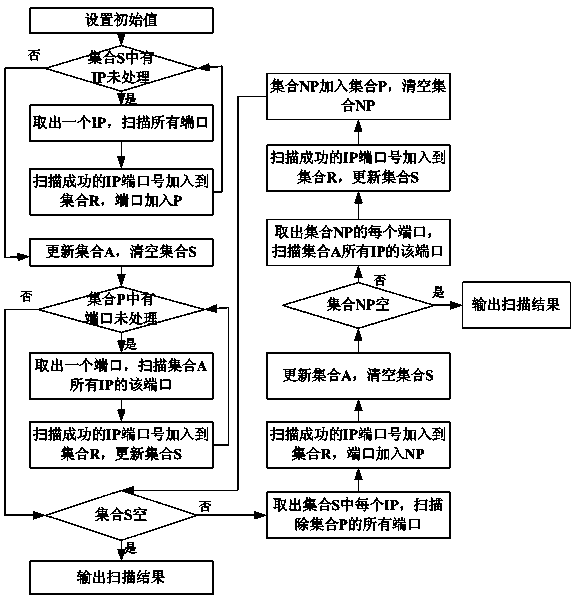
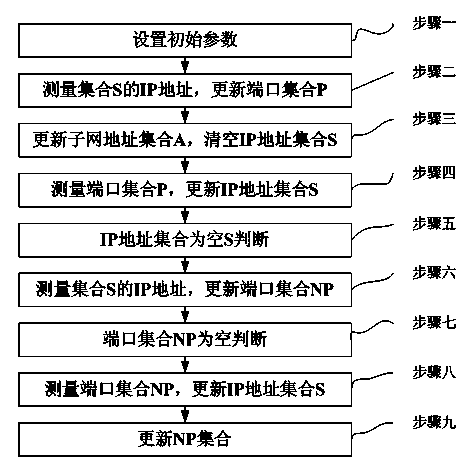
[0028] A kind of fast scanning method based on self-adaptive network port, it is characterized in that:
[0029] Step 1: Set an IP address set A of the scanned subnet. The initial value of set A is the IP address set of the scanned subnet set by the user. Set the IP address set S in advance. The initial value of set S is the IP address set by the user Set, set the scanning port set P in advance, the initial set of the set P is the set of scanning ports set by the user, set an IP port set R, the set R is initially empty, set the new port set NP, the new port set NP is initially empty, enter Step two;
[0030] Step 2: Take out each IP address in turn from the IP address set S, scan all the ports of the taken IP addresses, add the scanned IP addresses and port numbers to the IP port set R, and at the same time add the ports Add the number to the port set P, when all the IP addresses in the IP address set S are processed, go to step 3; otherwise, repeat step 2;
[0031] Step 3:...
Embodiment 2
[0039] The IP addresses and their open ports in all detected subnet IP address sets in this example are as follows:
[0040] 10.0.0.1 80
[0041] 10.0.0.2 80 1001
[0042] 10.0.0.3
[0043] 10.0.0.4
[0044] 10.0.0.5 1001 20450
[0045] 10.0.0.6
[0046] 10.0.0.7
[0047] A kind of fast scanning method based on self-adaptive network port, it is characterized in that:
[0048] Step 1 (1): Set an IP address set A of the scanned subnet. The initial value of set A is the set of IP addresses of the scanned subnet set by the user {10.0.0.1, 10.0.0.2, 10.0.0.3, 10.0.0.4 . For the scanning port set {80} set by the user, set an IP port set R, the set R is initially empty, set a new port set NP, the new port set NP is initially empty, and enter step 2 (2);
[0049] Step 2 (2): Take out each IP address 10.0.0.1 in turn from the IP address set S, scan all the ports of the taken out IP address 10.0.0.1, and add the scanned IP address and port number 80 Go to {10.0.0.1 80} in the I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com