Data access authorization protection method
A technology for data access and access rights, applied in the fields of digital data protection, electronic digital data processing, special data processing applications, etc., can solve problems such as confusion in the management of data access rights, and achieve the effect of all-round protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
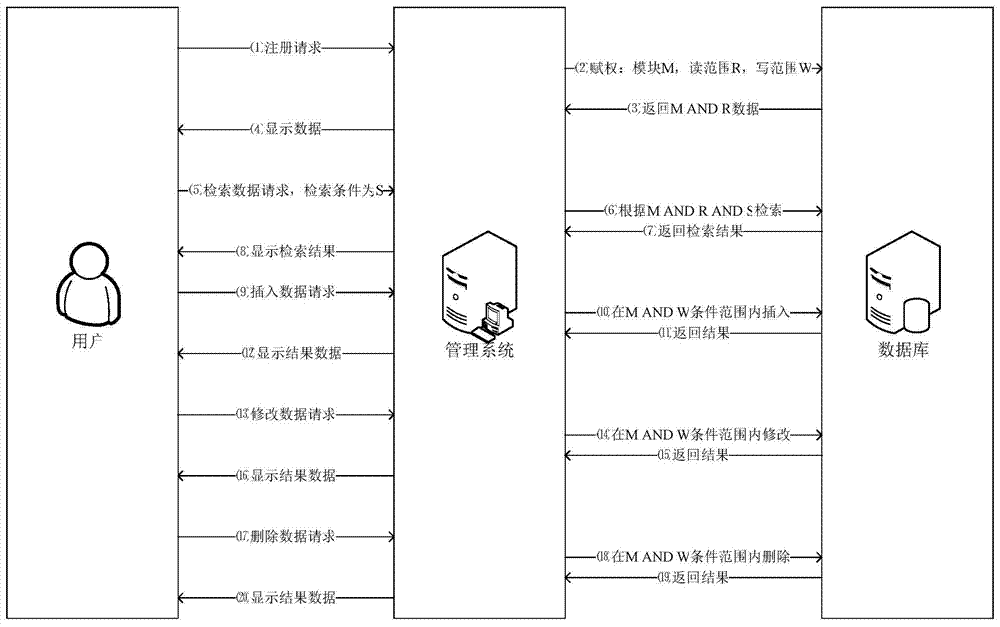
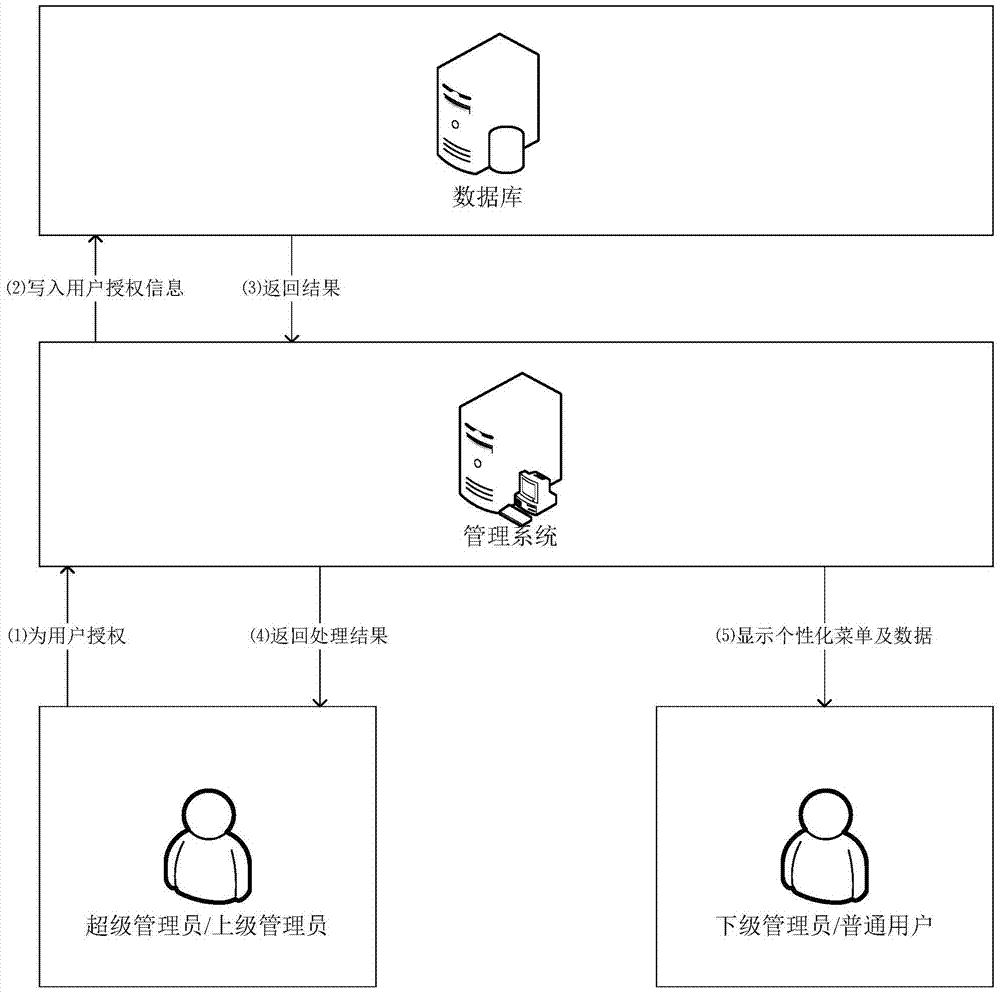
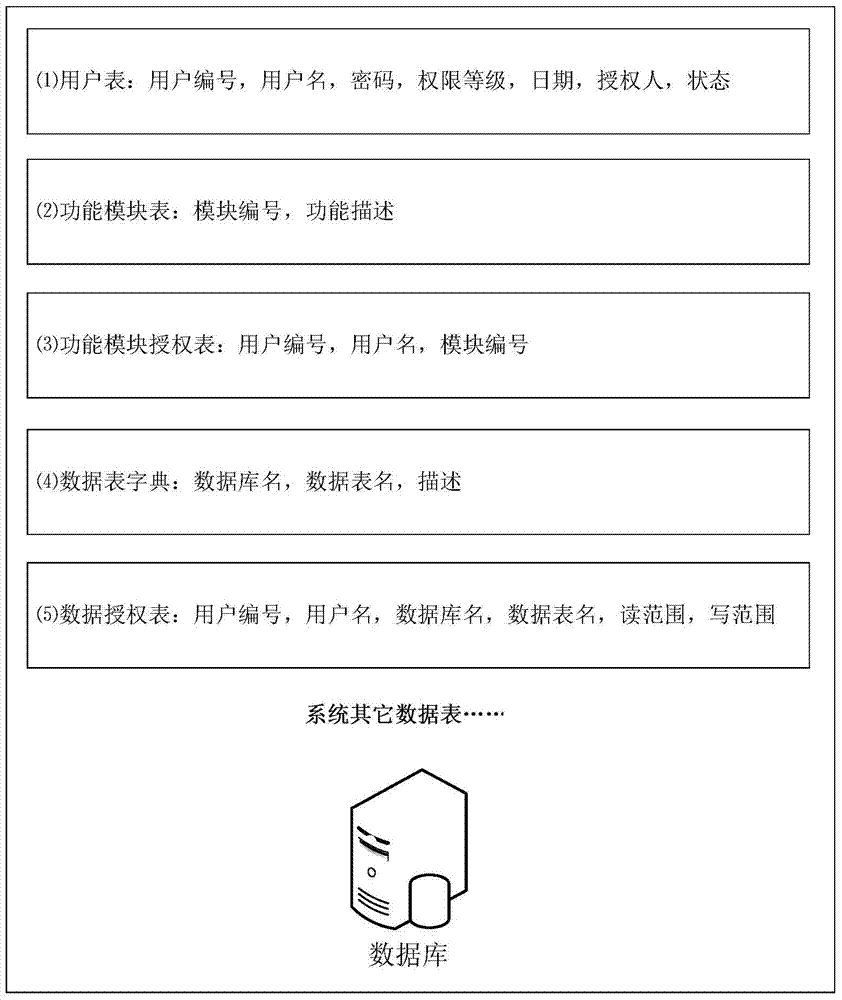
[0040] Such as figure 1 As shown, the present invention saves user registration information, data table dictionary, function module information, function module authorization information and data read and write range authorization information in the database; Read and write range access rights; the system displays the corresponding menu and data to the user according to the user’s default permissions; if the user’s corresponding data read and write range is empty, it means that the user has all permissions to the authorized function modules; otherwise, the user can only Authorized functional modules and data read and write operations; super administrators or upper-level administrators can modify the permissions of lower-level administrators or ordinary users at any time. Detailed flow process of the present invention is:
[0041] In the first step, the user sends a registration request to the background management system;
[0042] In the second step, the management system gr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com