Mobile terminal antitheft method and client
A technology of mobile terminals and anti-theft methods, applied in the field of Internet applications, can solve the problems of inability to prevent theft of mobile terminals, loss of user property, and inability to effectively curb theft crimes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
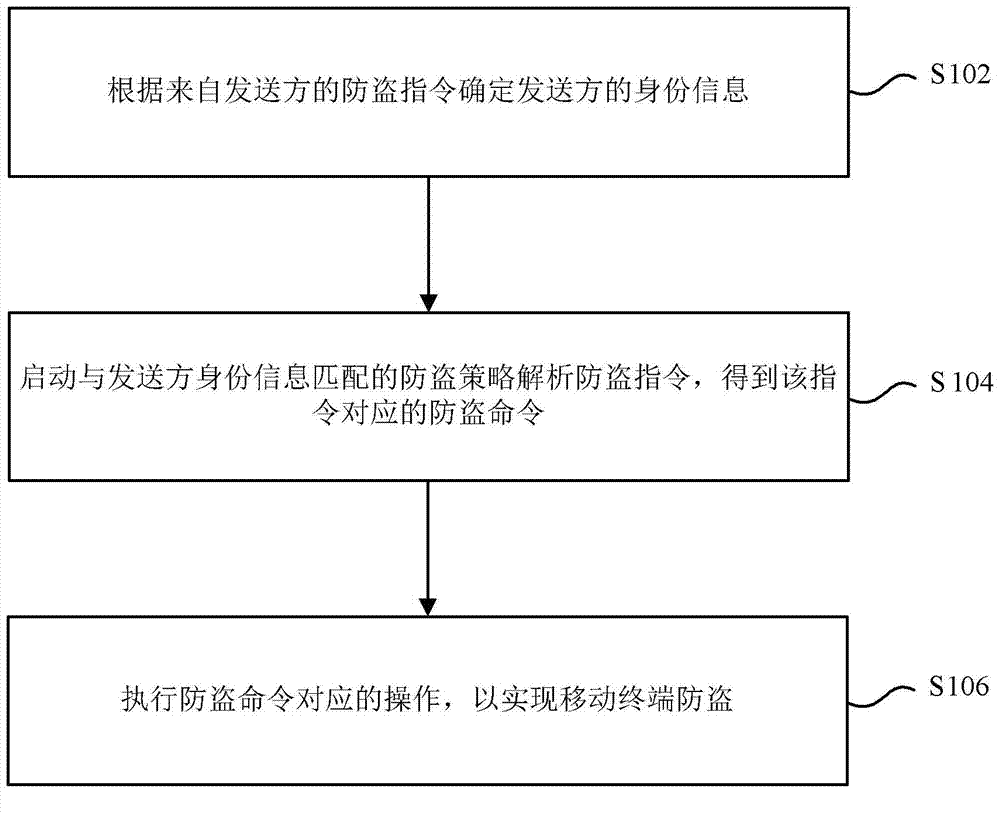
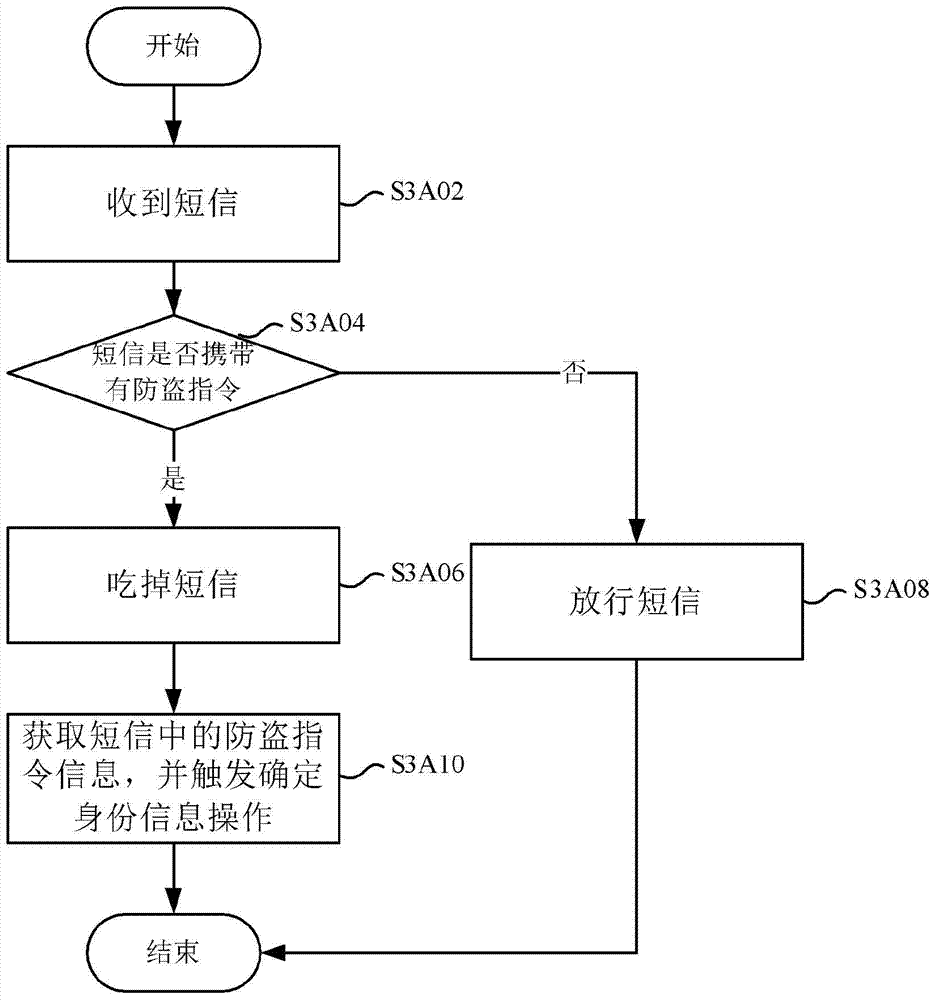
[0130] Figure 7 to Figure 9 It shows a processing flow chart of the mobile terminal anti-theft method according to a preferred embodiment of the present invention, which is used to support any of the above-mentioned mobile terminal anti-theft methods, and makes the above-mentioned mobile terminal anti-theft method clearer and easier to understand. It should be noted that, in order to explain this preferred embodiment more clearly and simply, in this preferred embodiment, the sender is set on the mobile phone of relatives and friends, and the mobile terminal is set on the stolen mobile phone.
[0131] Figure 7 It shows a processing flowchart of a mobile terminal anti-theft method using a short message anti-theft strategy according to a preferred embodiment of the present invention. Such as Figure 7 As shown, after the mobile phone is stolen, the preferred embodiment executes step S702 to send anti-theft text messages to the stolen mobile phone through the mobile phones of ...
Embodiment 2
[0191] Figure 13 to Figure 15 It shows a processing flow chart of the mobile terminal anti-theft method according to a preferred embodiment of the present invention, which is used to support any of the above-mentioned mobile terminal anti-theft methods, and makes the above-mentioned mobile terminal anti-theft method clearer and easier to understand.
[0192] Figure 13 It shows a processing flow chart of a mobile terminal anti-theft method using an account anti-theft policy according to a preferred embodiment of the present invention. see Figure 13 , the process includes at least step S1302 to step S1318.
[0193] Step S1302, log in to the activated account, and send an anti-theft instruction to the server through the activated account.
[0194] Step S1304, the server returns the processing result of the anti-theft command, prompting the activated account server to receive the anti-theft command. Wherein, the processing result returned by the server carries th...
Embodiment 3
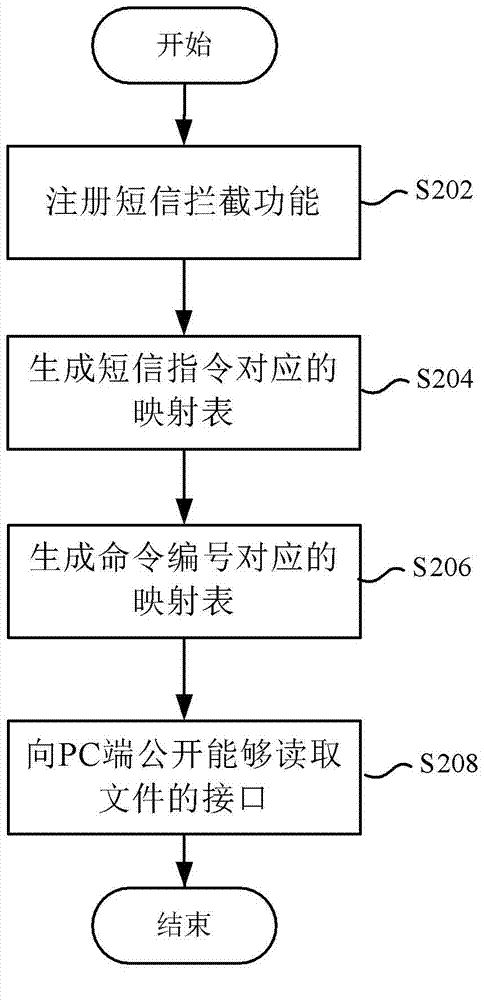
[0239] Figure 16 and Figure 17 It shows a processing flow chart of the mobile terminal anti-theft method according to a preferred embodiment of the present invention, which is used to support any of the above-mentioned mobile terminal anti-theft methods, and makes the above-mentioned mobile terminal anti-theft method clearer and easier to understand. It should be noted that, in order to explain this preferred embodiment more simply and clearly, the mobile terminal is set as a mobile phone in this preferred embodiment.
[0240] Figure 16 A processing flowchart of a method for activating the anti-theft function of a mobile phone at the PC terminal side according to an embodiment of the present invention is shown. see Figure 16 , the process includes at least step S1602 to step S1616.
[0241] Step S1602, judging whether the connection between the PC terminal and the mobile phone has been established. If yes, execute step S1604; if no, the process ends.
[02...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com