Communication data encryption and decryption method based on BBS, RSA and SHA-1 encryption algorithm
A technology of SHA-1 and encryption algorithm, which is applied to the public key of secure communication, user identity/authority verification, etc. It can solve the problems of deriving original data and differences in hash results, and achieve harm prevention and high security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with specific examples.
[0026] The communication data encryption and decryption method based on BSS, RSA, SHA-1 encryption algorithm described in the present embodiment, its specific situation is as follows:
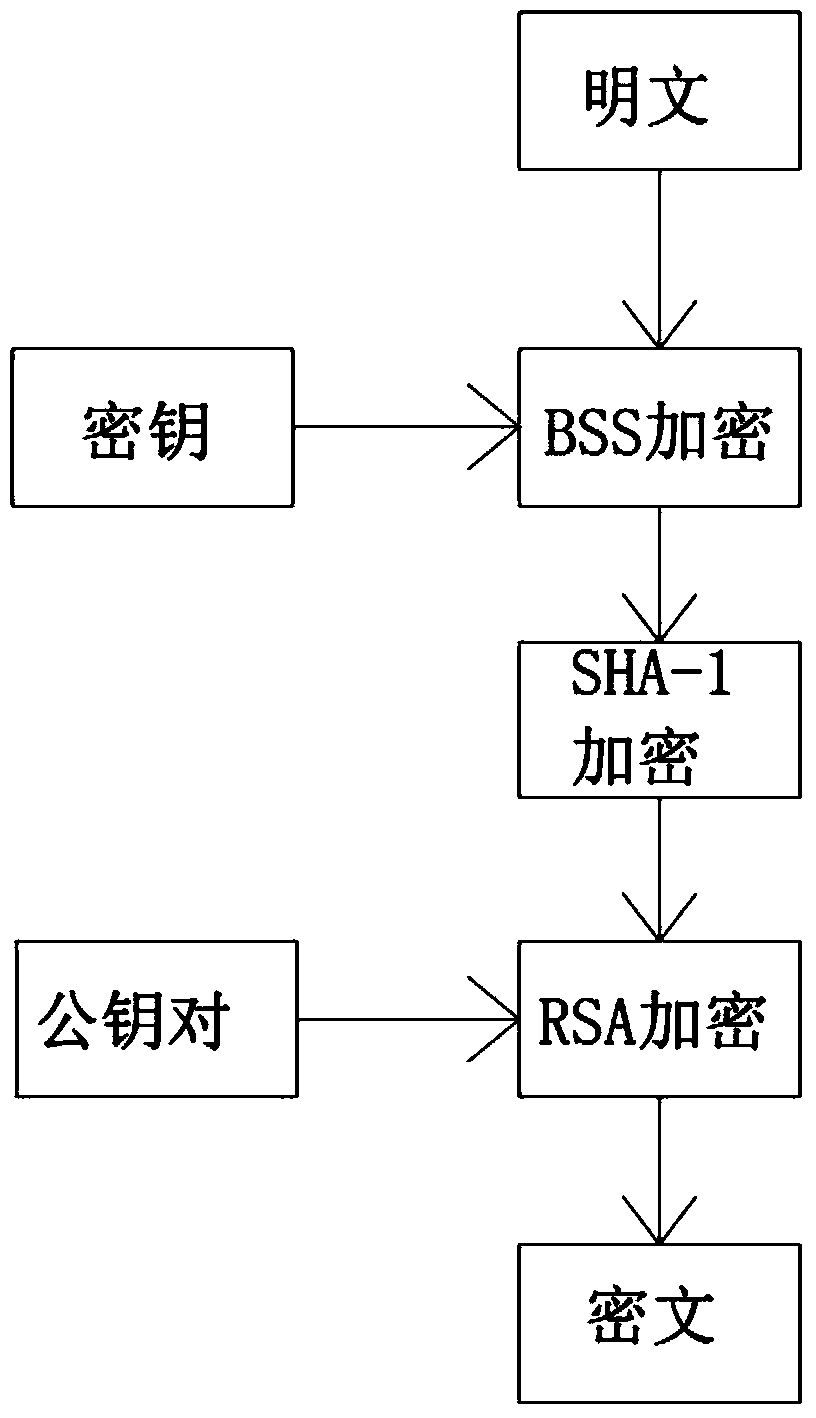
[0027] 1) Obtain the data to be encrypted and sent;
[0028] 2) Encrypt the data to be sent for the first time, that is, BSS encryption;
[0029] 3) Use the SHA-1 encryption algorithm to generate summary content for the data that has been encrypted for the first time;
[0030] 4) Use the RSA encryption public key provided by the receiving end to encrypt the SHA-1 encrypted data and digest;
[0031] 5) Send ciphertext;
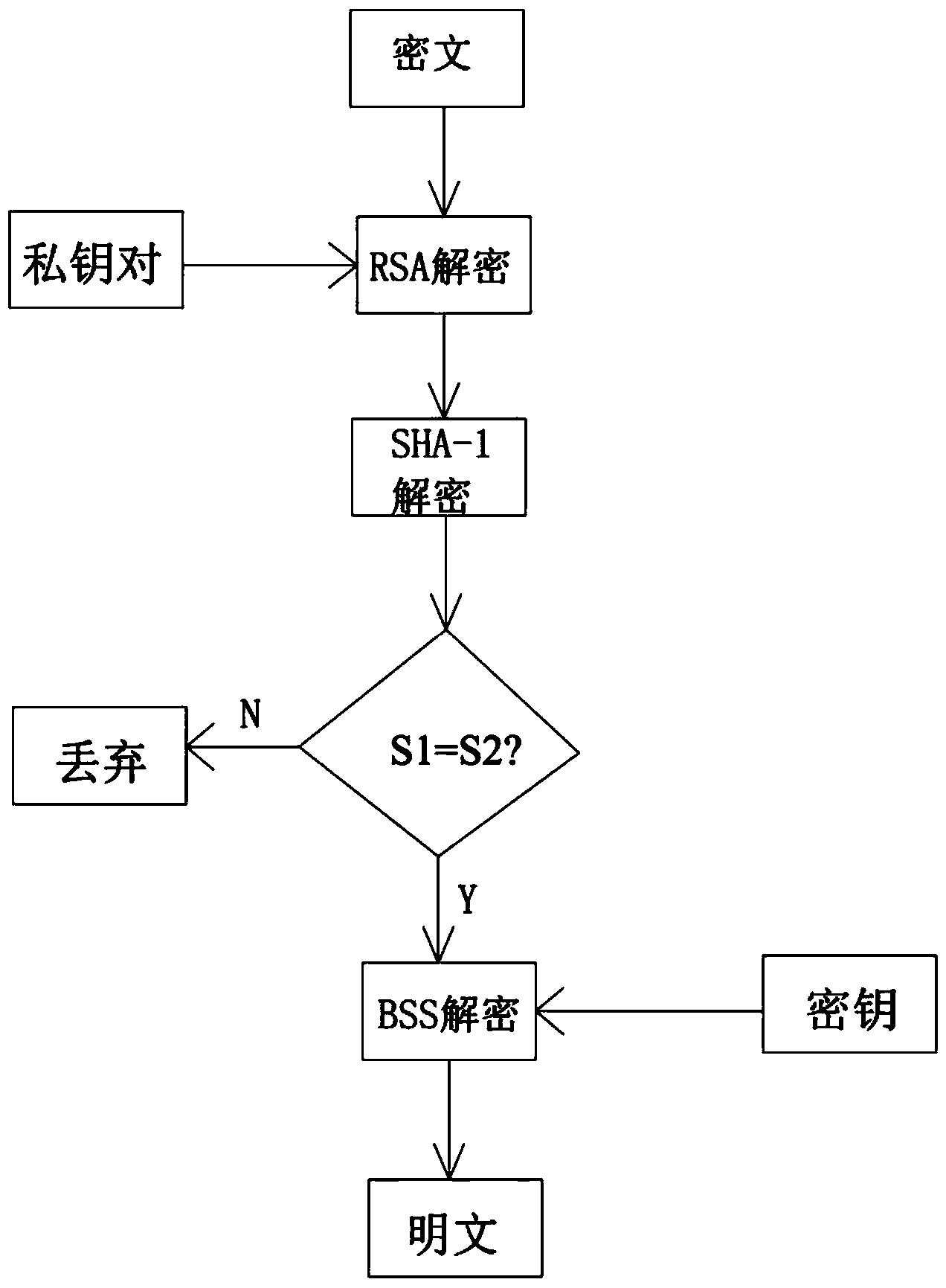
[0032] 6) The receiving end receives the ciphertext and uses its own private key to decrypt the ciphertext for the first time;
[0033] 7) Perform identity authentication on the received data;
[0034] 8) BSS decrypts the data that has completed identity authentication, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com