Management of group secrets by group members
A group key and key technology, applied in the field of group secret management, can solve the problem that the broadcaster does not use it
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The following description of an embodiment of the present invention is directed to the 1 elastic solution.
[0031] 1. Establishment of device key and device group key when adding a device to a device group
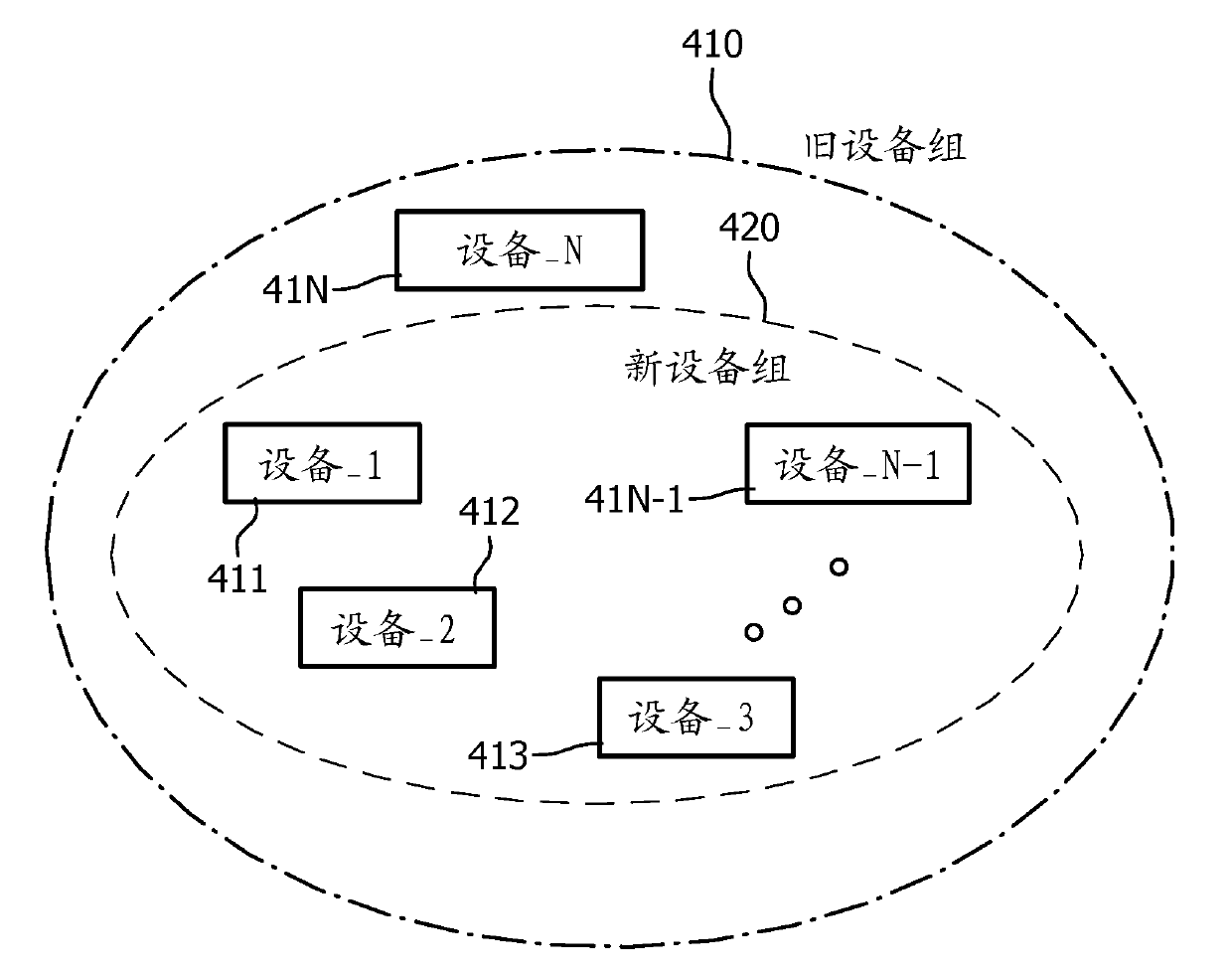
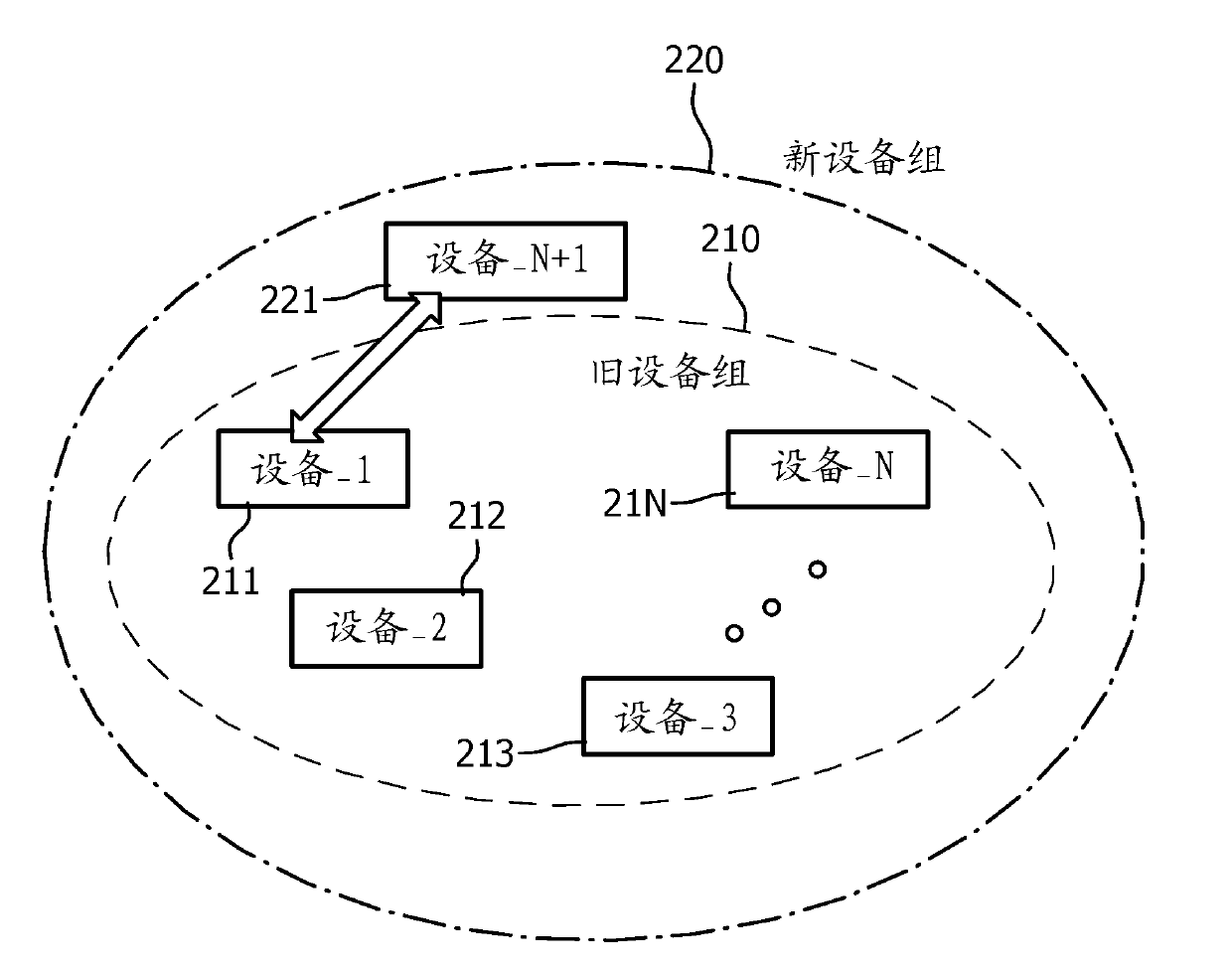
[0032] refer to figure 2 , the old device group 210 includes member devices: device_1 211 , device_2 212 , device_3 213 , . . . , device_N 21N. When a new device Device_N+1 221 joins the device group, a new device group 220 is formed. For clarity, the original group of N devices is labeled as old device group 210 and the expanded group is labeled as new device group 220 . It should be understood that each device in the group of devices includes at least a network interface for communicating with other devices and a processing unit with hardware and software components for performing encryption, decryption and deal with.
[0033] Such as figure 2As shown in , there are multiple devices Device_1 211, Device_2 212, Device_3 213, ..., Device_N 21N in the old d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com