Detection of suspect wireless access points
A wireless access point and access point technology, applied in wireless communication, electrical components, security devices, etc., can solve problems such as malicious attacks and man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
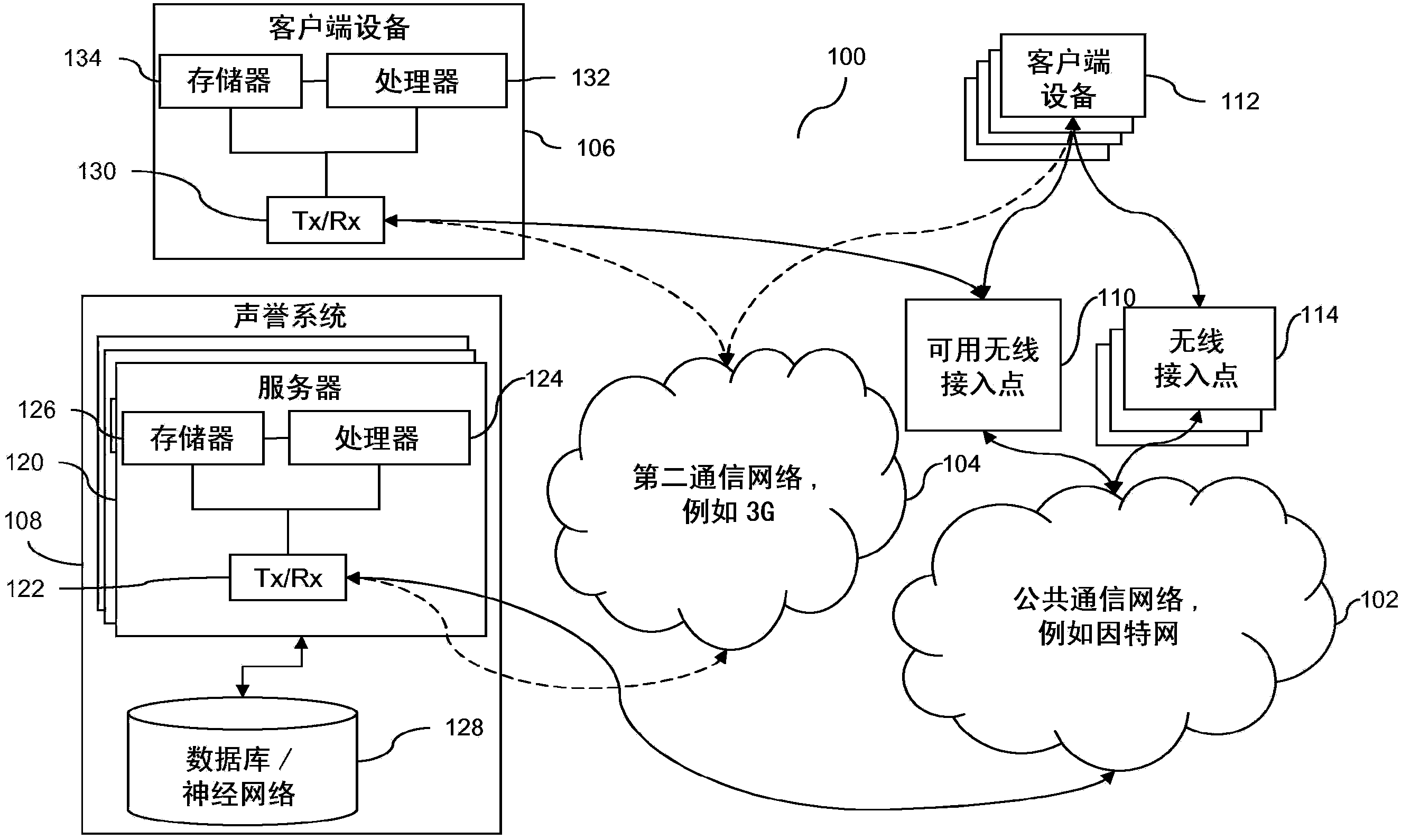
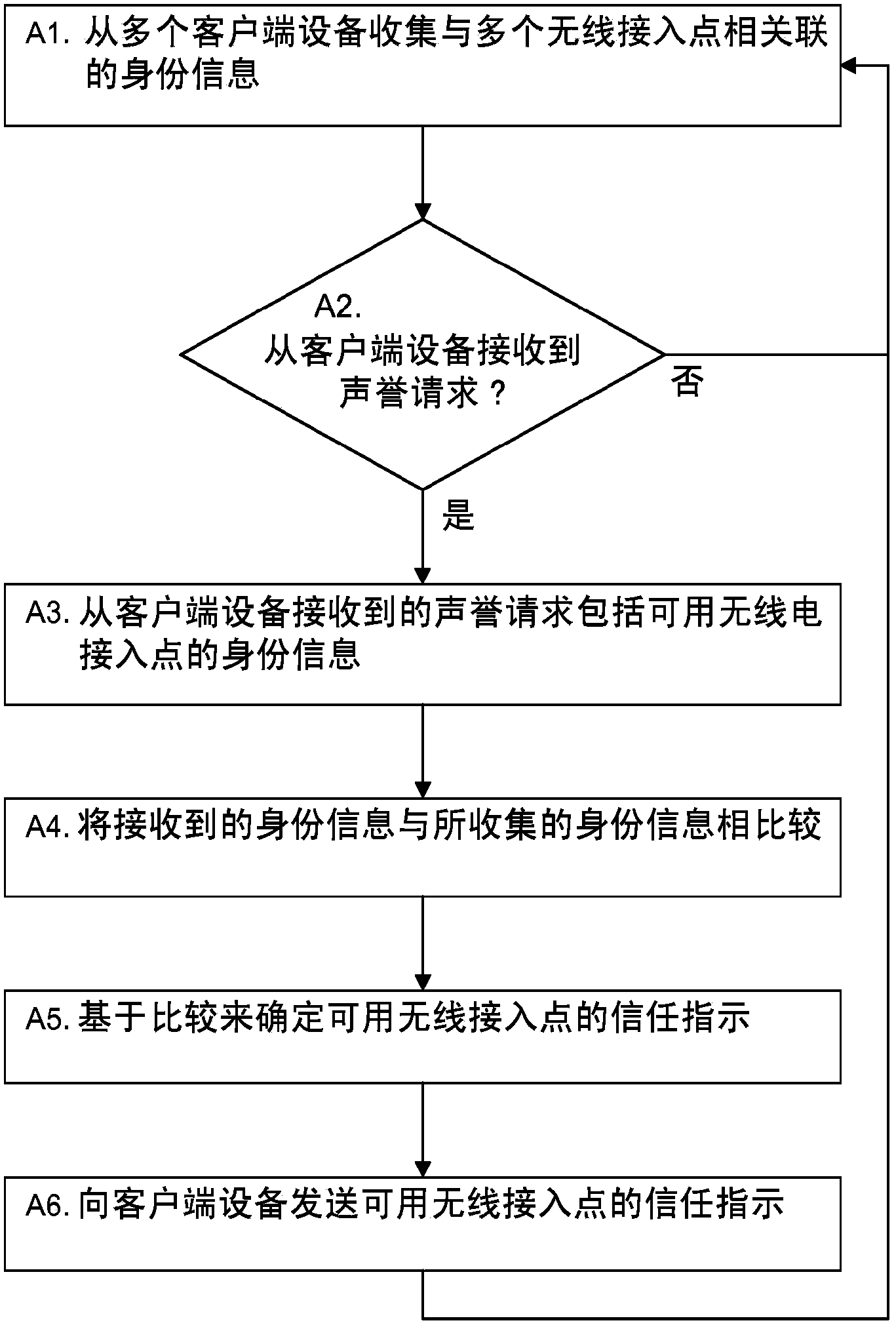
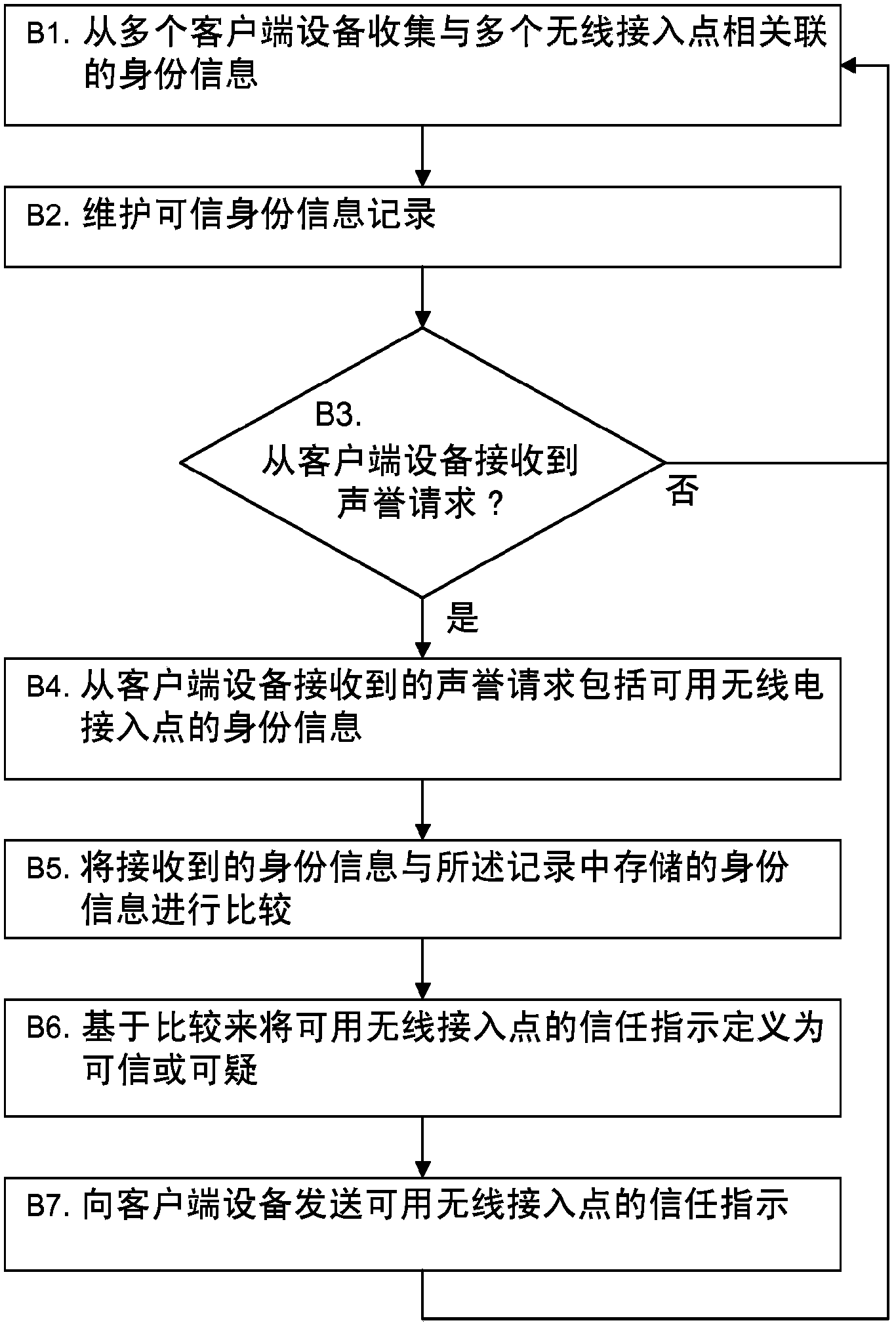
[0029] In order to at least partially overcome the above-mentioned problems and difficulties, it is proposed herein to identify wireless access points that provide access services to client devices by using external wireless access point characteristics available to client devices. Specifically, these problems and difficulties can be mitigated by accumulating or collecting wireless access point identity information or reputation information from multiple client devices in a reputation system, which can include one or more networked backends server. The system may respond to a client device's reputation request regarding available wireless access points by sending the client device trust or reputation indication information associated with the available wireless access points. A trust or reputation indication may include or represent data indicative of a trustworthiness or reputation status of a wireless access point, or information associated with a wireless access point.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com