Bearer binding method and bearer binding system
A binding and functional technology, applied in connection management, nan, network traffic/resource management, etc., can solve signaling storms, unrealistic problems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
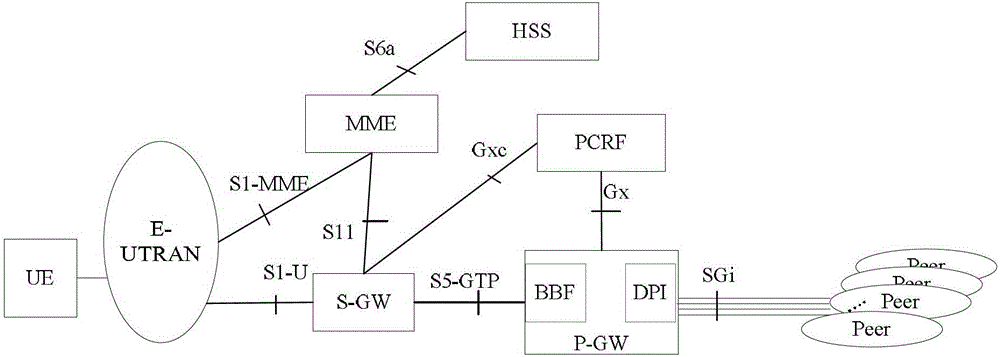
[0129] figure 2 It is a flow chart of application-based bearer binding according to preferred embodiment 1 of the present invention, as shown in figure 2 As shown, the process is based on mode 1) in the background technology, that is, both the application detection DPI function and the bearer binding function are integrated in the P-GW. The process mainly includes the following steps:
[0130] Step S201: the terminal UE initiates a certain application or several applications with the communication peer. The type of application studied here is non-derivable, the quintuple is changeable, or when the operator configures certain applications to be detected, such as terminal browsing web pages. The P-GW serving as an application detection function has detected the one or more applications. The P-GW performs application detection according to the ADC rules installed or activated before the PCRF.
[0131] Step S202: The P-GW reports the type of the detected application (App ID,...
Embodiment 2
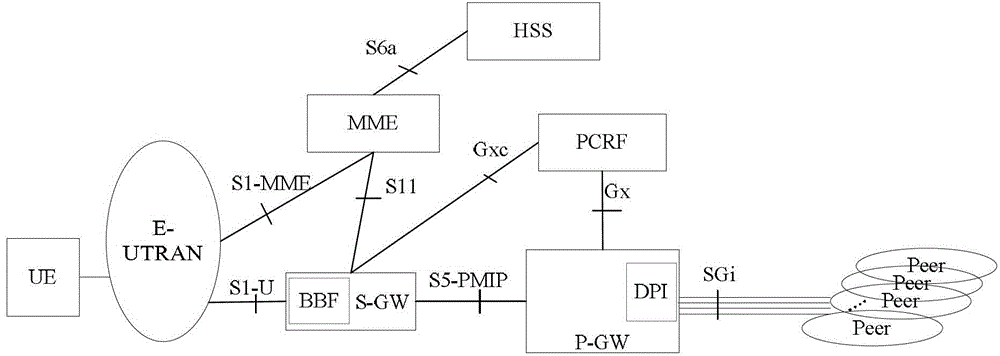
[0143] image 3 It is a flow chart of application-based bearer binding according to preferred embodiment 2 of the present invention, such as image 3 As shown, the flow chart is based on mode 3) in the background technology, that is, the application detection DPI function is independently deployed on the TDF, and the P-GW serves as the bearer binding function. The process mainly includes the following steps:
[0144] Step S301: the terminal UE initiates a certain application or several applications with the communication peer. The type of application studied here is non-derivable, the quintuple is changeable, or when the operator configures certain applications to be detected, such as terminal browsing web pages. The TDF as an application detection function detects the one or more applications.
[0145] Step S302: The TDF reports the type of the detected application (App ID, application type identifier) to the PCRF through the Sd session.
[0146] Step S303: According to...
Embodiment 3
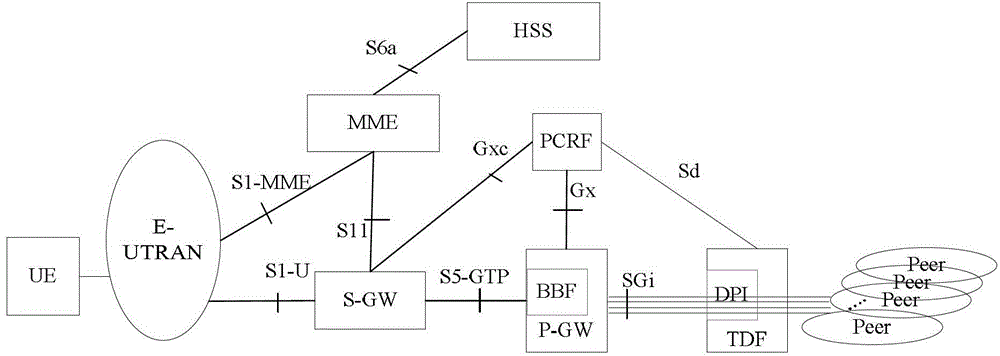
[0161] Figure 4 It is a flow chart of application-based bearer binding according to preferred embodiment 3 of the present invention, as shown in Figure 4 As shown, the flowchart is based on mode 4) in the background technology, that is, the application detection DPI function is independently deployed on the TDF, and the S-GW serves as the bearer binding function. The process mainly includes the following steps:
[0162] Step S401-Step S402: It is exactly the same as Step S301-Step S302, and will not be repeated here.
[0163] Step S403: basically the same as step S303. The difference is that the PCRF also needs to formulate the QoS information sent to the S-GW.
[0164] Step S404: Because the S-GW performs the bearer binding function, the PCRF sends the data packet label and QoS information to the S-GW through the Gxc interface; optionally, the PCRF sends the data label to the P-GW through the Gx session.
[0165] The data packet label sent to P-GW is no longer used for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com