Encrypted communication method, system and related equipment
A technology of encrypted communication and encryption algorithm, which is applied in the field of communication, can solve problems such as the security of air interface signals, and achieve the effect of making up for security defects and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
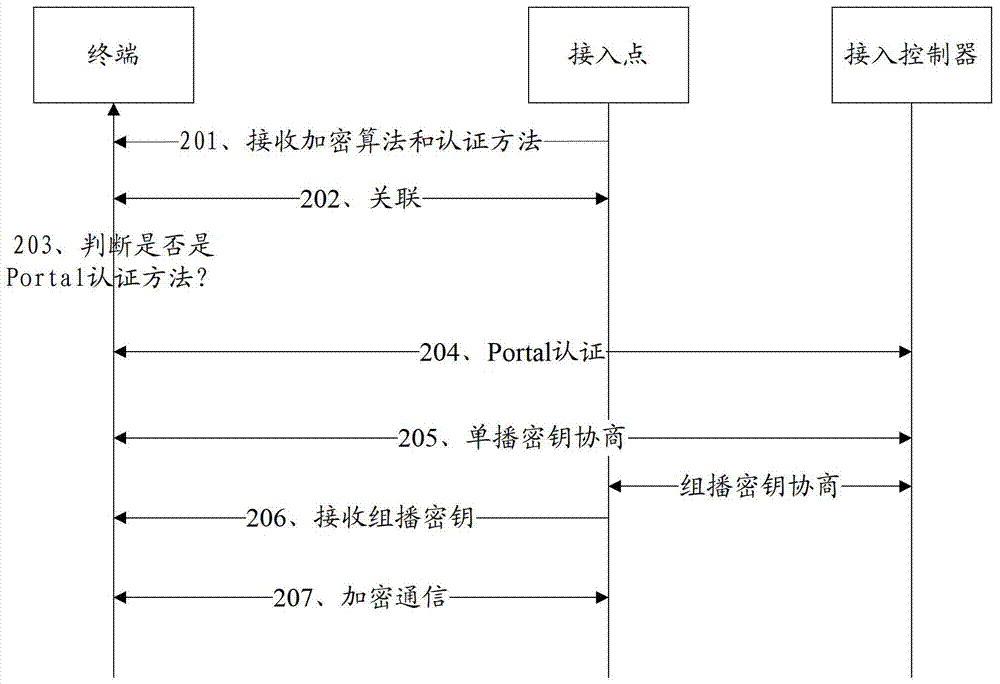
[0074] The invention provides an encrypted communication method, such as figure 2 As shown, the network architecture involved in the method includes a terminal (client), AP (Access Point, access point) and AC (Access Controller, access controller), and the method includes:
[0075] 201. The terminal receives the encryption algorithm and authentication method of the terminal sent by the access point AP.
[0076] The encryption algorithm may include: AES (Advanced Encryption Standard, Advanced Encryption Standard) algorithm or TKIP (Temporal Key Integrity Protocol, Temporal Key Integrity Protocol) algorithm, of course, may also include other suitable algorithms, which are not specifically limited here .
[0077] Wherein, the authentication method may include: WPA (Wi-Fi Protected Access, Wi-Fi network security access) or WPA2 or Portal authentication method, of course, may also include other authentication methods, which are not specifically limited here.
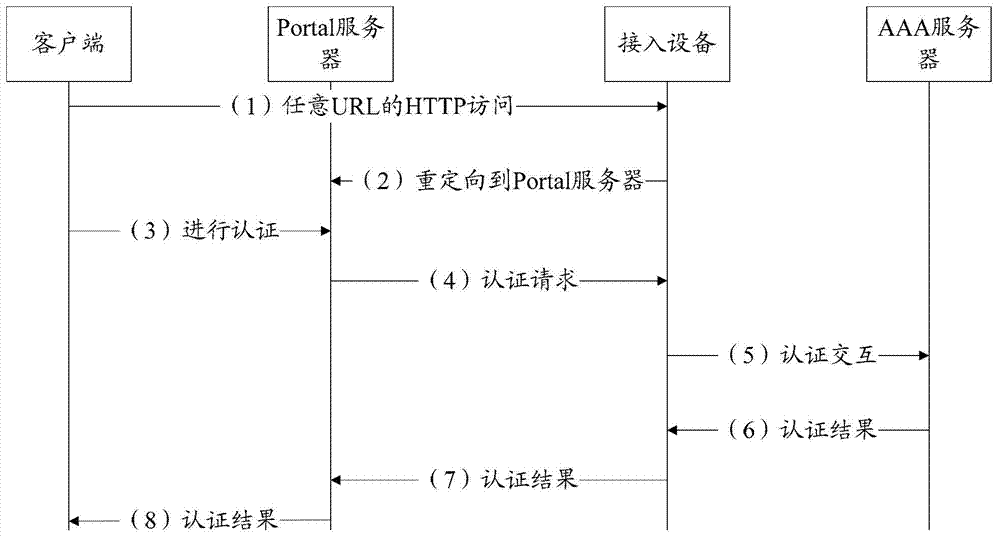
[0078] 202. The te...
Embodiment 2
[0110] The present invention also provides an encrypted communication method, such as Figure 4 As shown, the method includes:
[0111] 401. The AC obtains the encryption algorithm and the authentication method of the terminal during the association process between the AP and the terminal; the terminal obtains the encryption algorithm and the authentication method from the AP.
[0112] For the specific process of associating between the AP and the terminal, reference may be made to the description in Embodiment 1, which will not be repeated here.
[0113] 402. If the above-mentioned method is a Portal authentication method, the above-mentioned AC provides Portal authentication for the above-mentioned terminal, and saves the account number and password used by the above-mentioned terminal in the above-mentioned Portal authentication process;
[0114] The specific content of the Portal authentication method may be the prior art, and will not be repeated here.
[0115] 403. The...
Embodiment 3
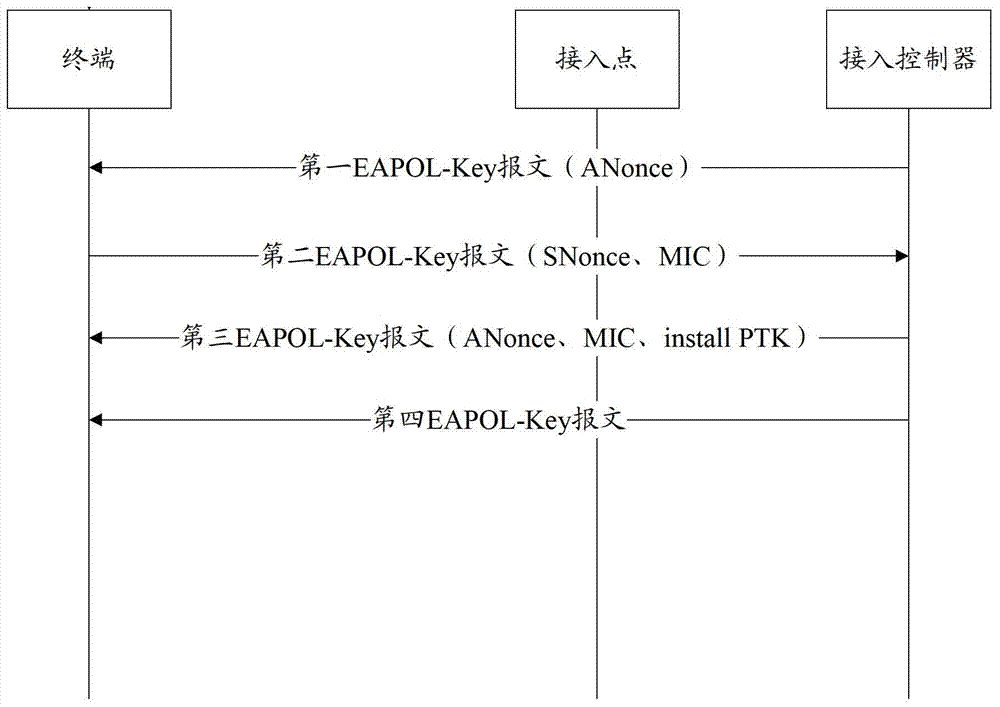
[0123] The present invention also provides an encrypted communication method, such as Figure 5 As shown, the above methods include:
[0124] 501. The AP sends the encryption algorithm and authentication method of the terminal to the above-mentioned terminal.
[0125] Specifically, the AP sends the encryption algorithm and the authentication method to the terminal by carrying the encryption algorithm and the above-mentioned authentication method in the beacon frame or the Probe Response message sent to the terminal. For details, please refer to the describe.
[0126] 502. The above-mentioned AP associates with the terminal, so that the access controller AC acquires the above-mentioned encryption algorithm and the above-mentioned authentication method during the above-mentioned association process;
[0127] For the specific process of associating between the AP and the terminal, reference may be made to the description in Embodiment 1, which will not be repeated here.
[012...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com