Security and protection method for achieving security and protection function of mobile phone
A mobile phone and functional technology, applied in location-based services, telephone communications, electrical components, etc., can solve the problem of multi-time re-collection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
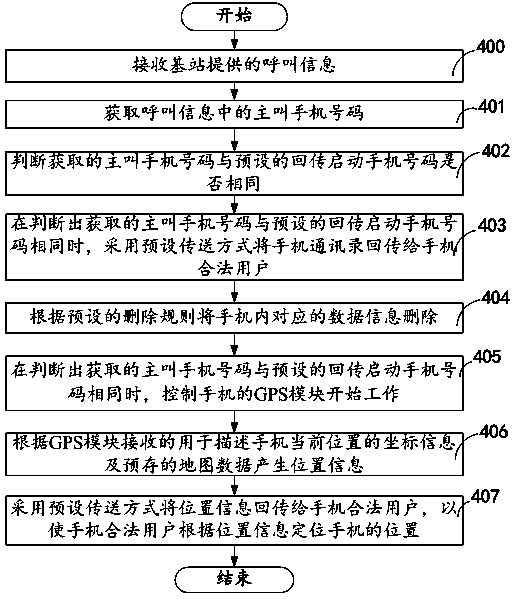
[0014] Please see also figure 1 , the present invention also provides a kind of security method that realizes mobile phone security function, comprises the following steps:
[0015] Step S400, receiving call information provided by the base station. For example, when a legitimate mobile phone user loses his mobile phone with security function and uses other mobile phones to dial the mobile phone with security function, the base station will provide the call information to the mobile phone with security function.
[0016] Step S401, obtaining the calling mobile phone number in the call information.
[0017] Step S402, judging whether the acquired mobile phone number of the calling party is the same as the preset mobile phone number for initiating callback. The preset callback activation mobile phone number is the mobile phone number preset by the legal user of the mobile phone in the lost mobile phone. The mobile phone number of the third party's mobile phone.
[0018] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com