Patents
Literature
39results about How to "Don't worry about leaking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security cloud storage system based on increment synchronization
InactiveCN104023085AImprove user experiencePrevent leakageTransmissionTransmission protocolFile synchronization
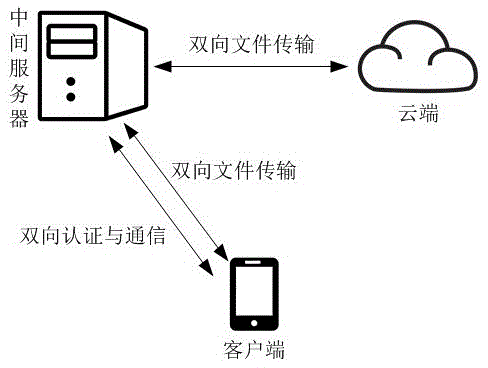
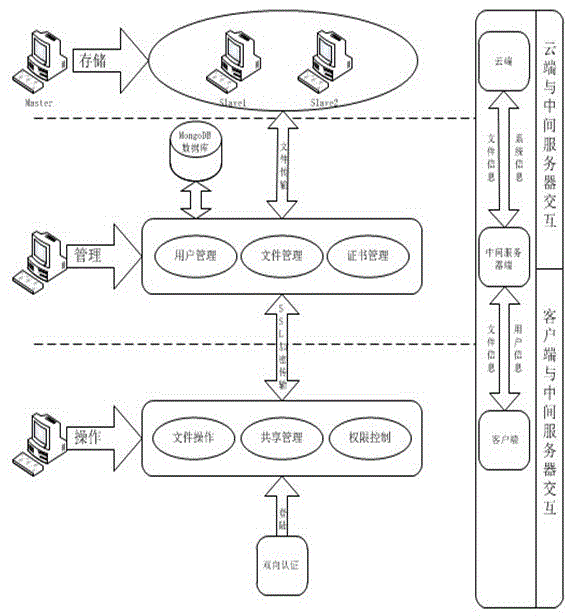
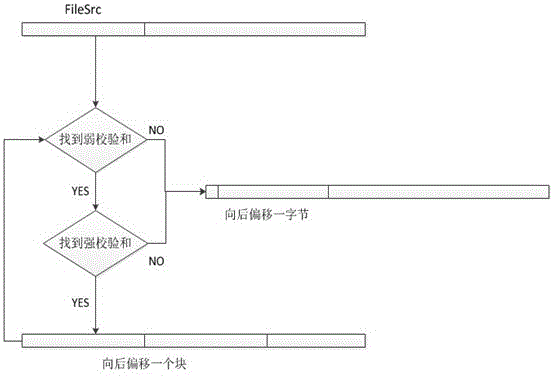
The invention discloses a security cloud storage system based on increment synchronization. A three-tier architecture of client-intermediate server-private cloud terminal is adopted, and data security is guaranteed by multiple security protection technology. After being blocked and encrypted, a user file is transmitted to a cloud terminal through an SSL (security socket layer) security transmission protocol; after finishing the work of user management and key management, the intermediate server terminal adopts a mutual authentication mechanism and an access control mechanism to realize the safe data share so as to completely prevent original data from leaking from the server terminal; the binding of the file and a mobile device is realized at a client, the specific file can be only opened on a specific device, and even though the file is leaked by an insider, a leaking device can be traced; moreover, the unique increment synchronization technology is realized, and the file can be synchronized by only synchronizing modified file blocks, so that the flow consumption in the file transmission process is reduced, the transmission efficiency is improved, the system usability is enhanced, and user experience is promoted.
Owner:WUHAN UNIV
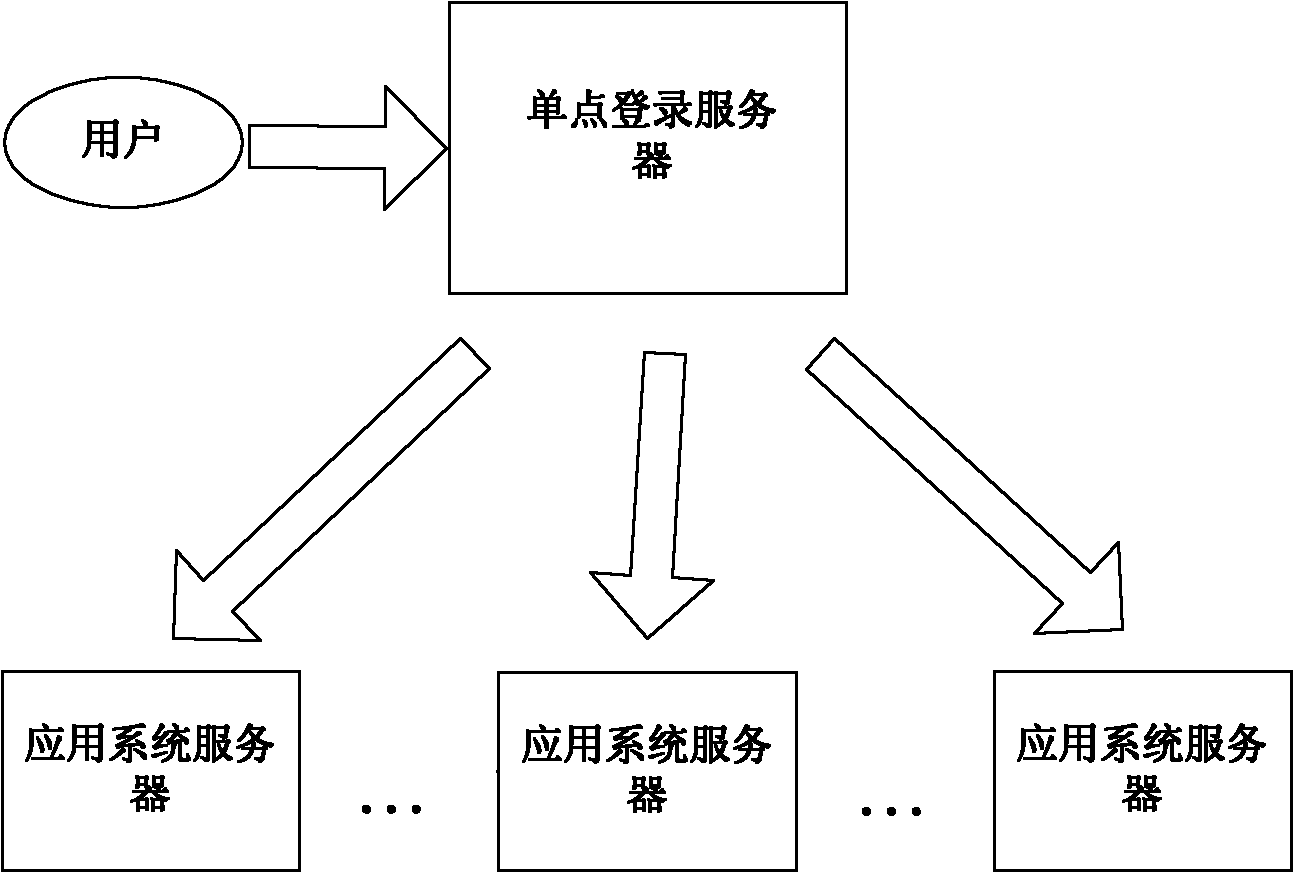
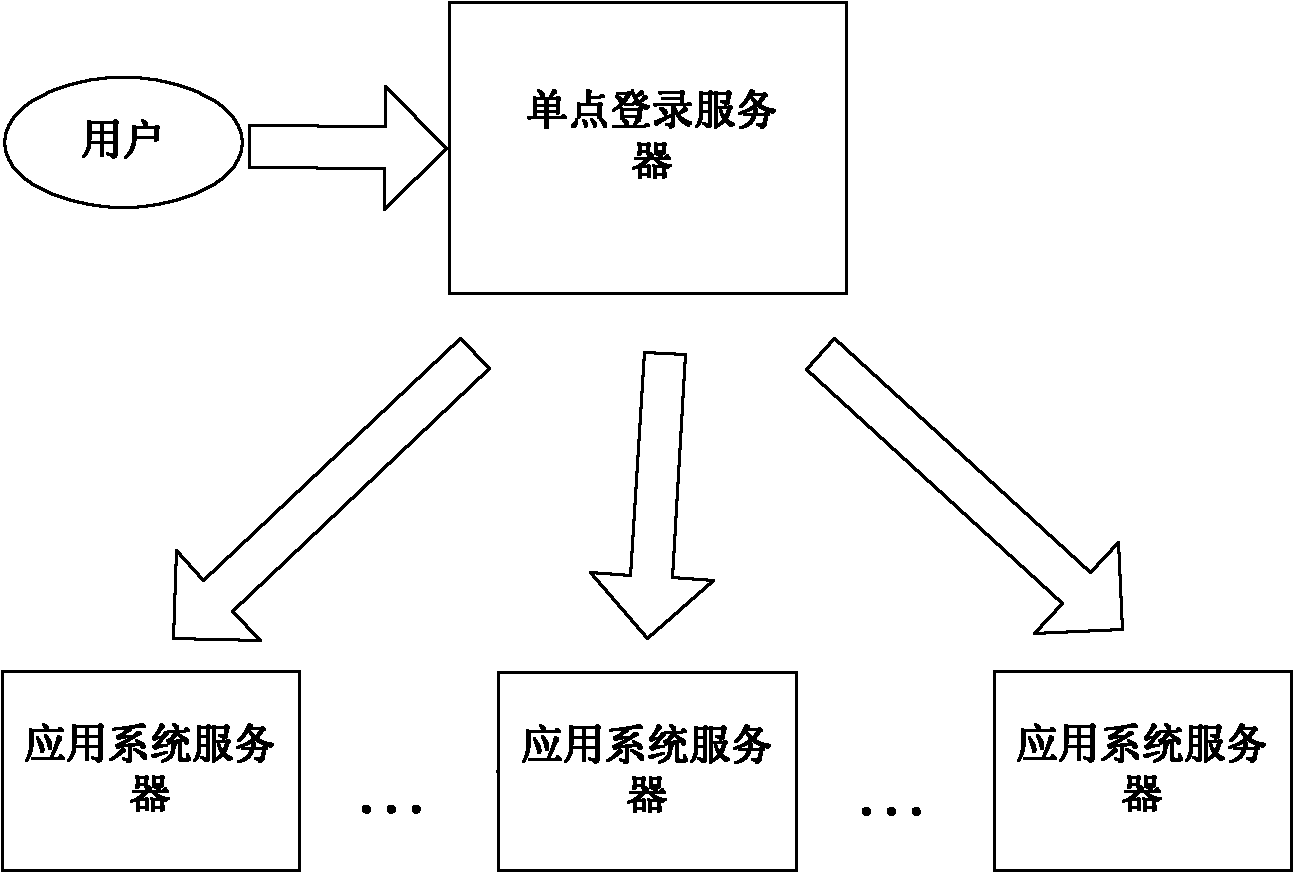
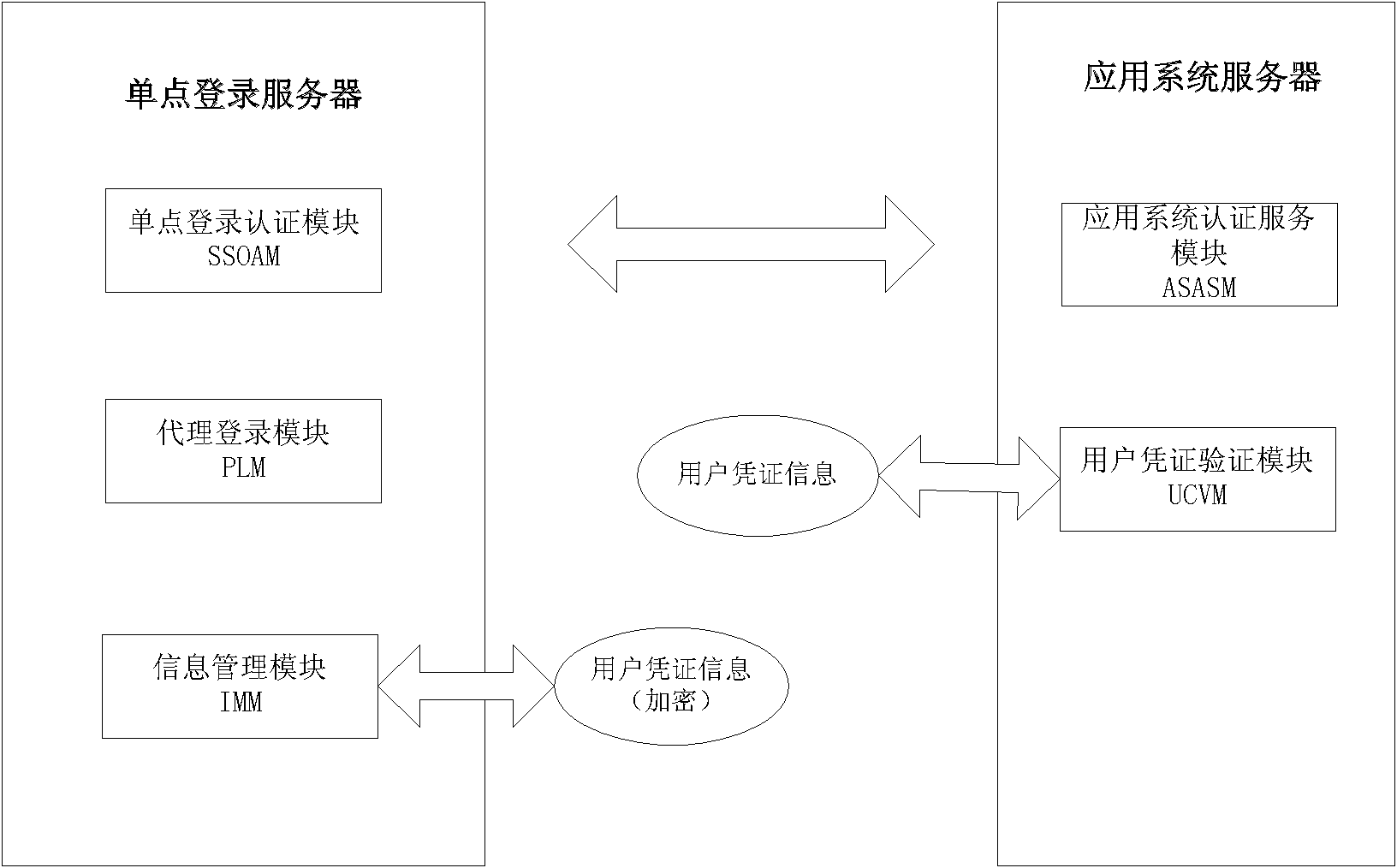
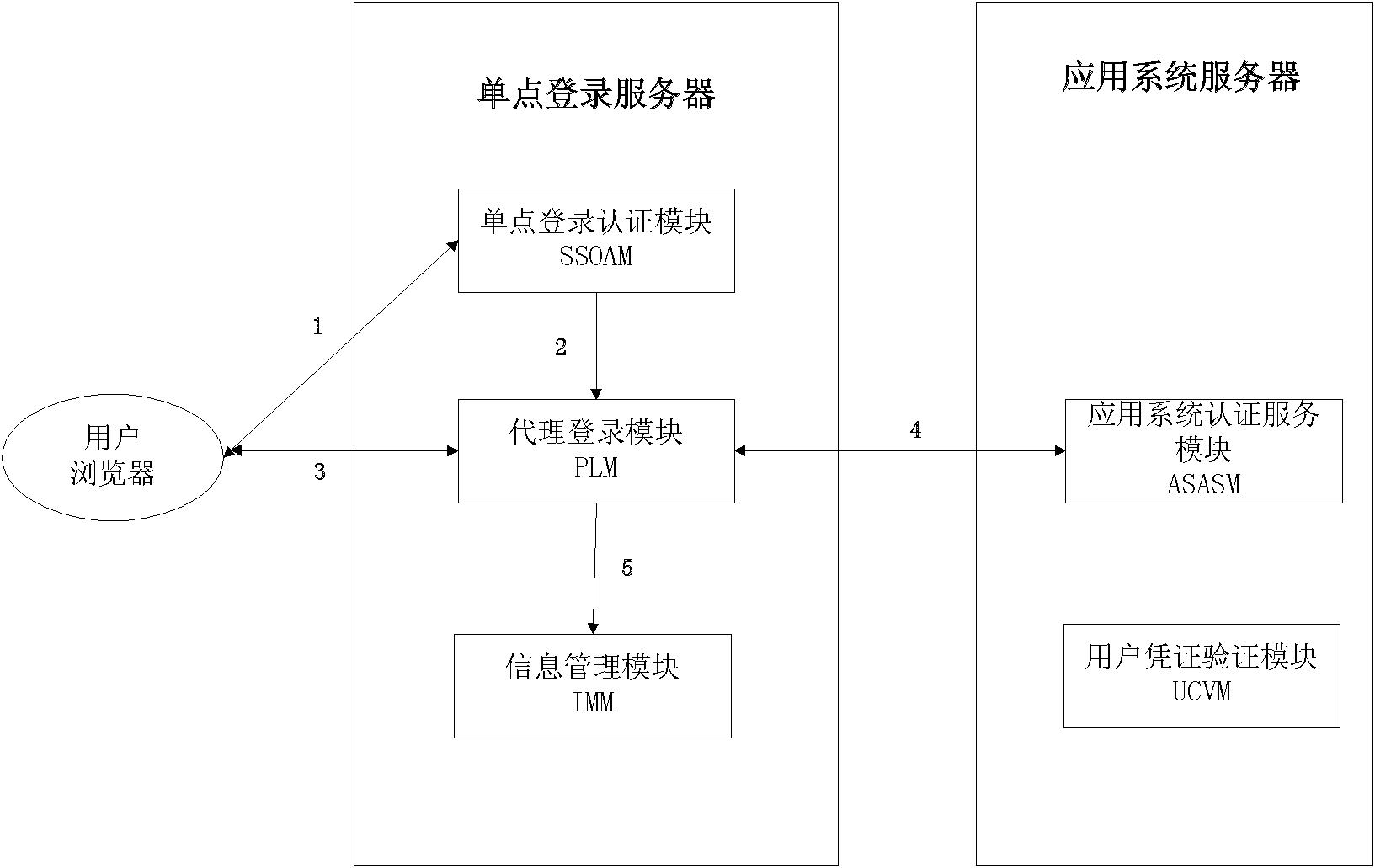
Agent-based single sign on (SSO) method and system
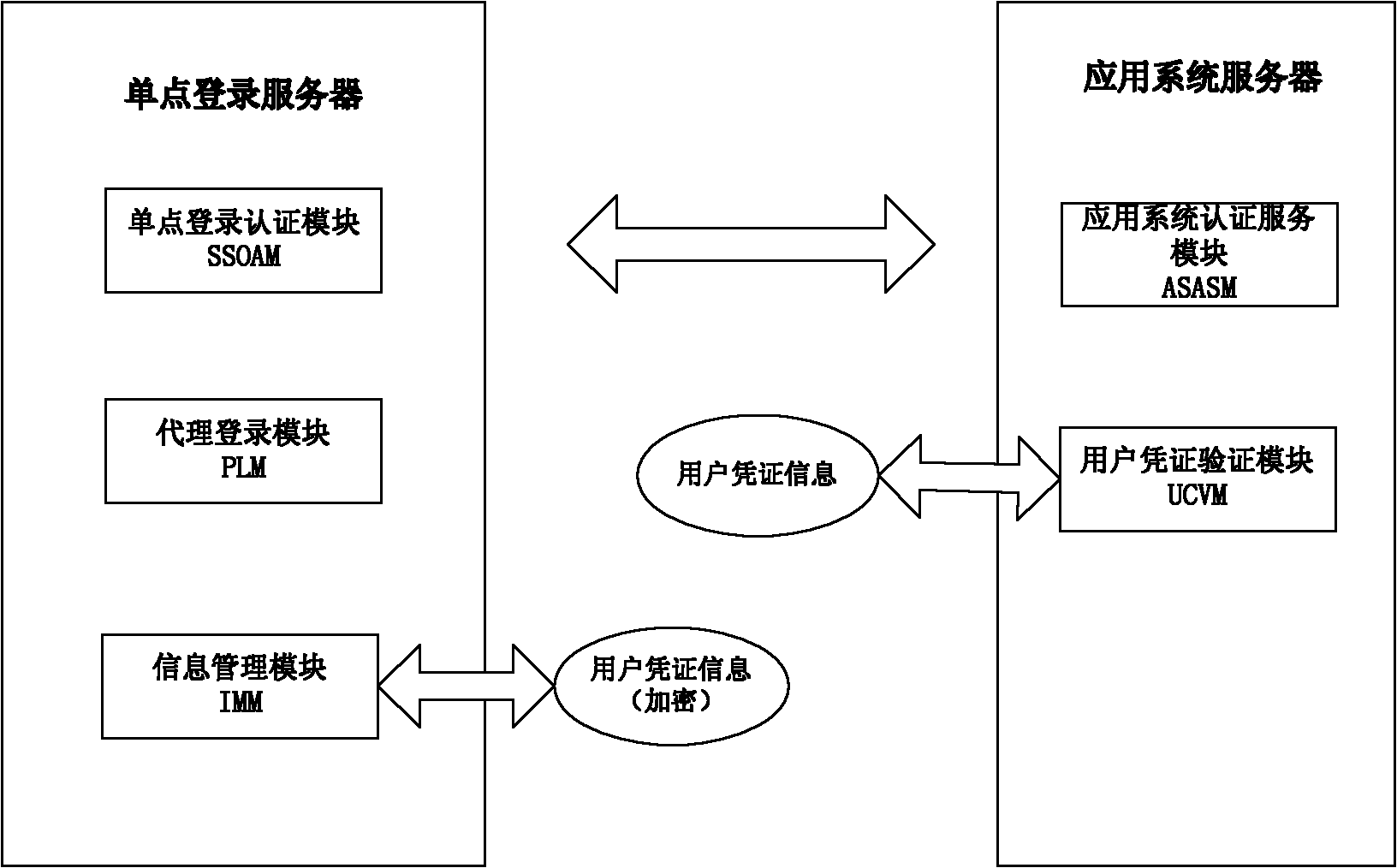
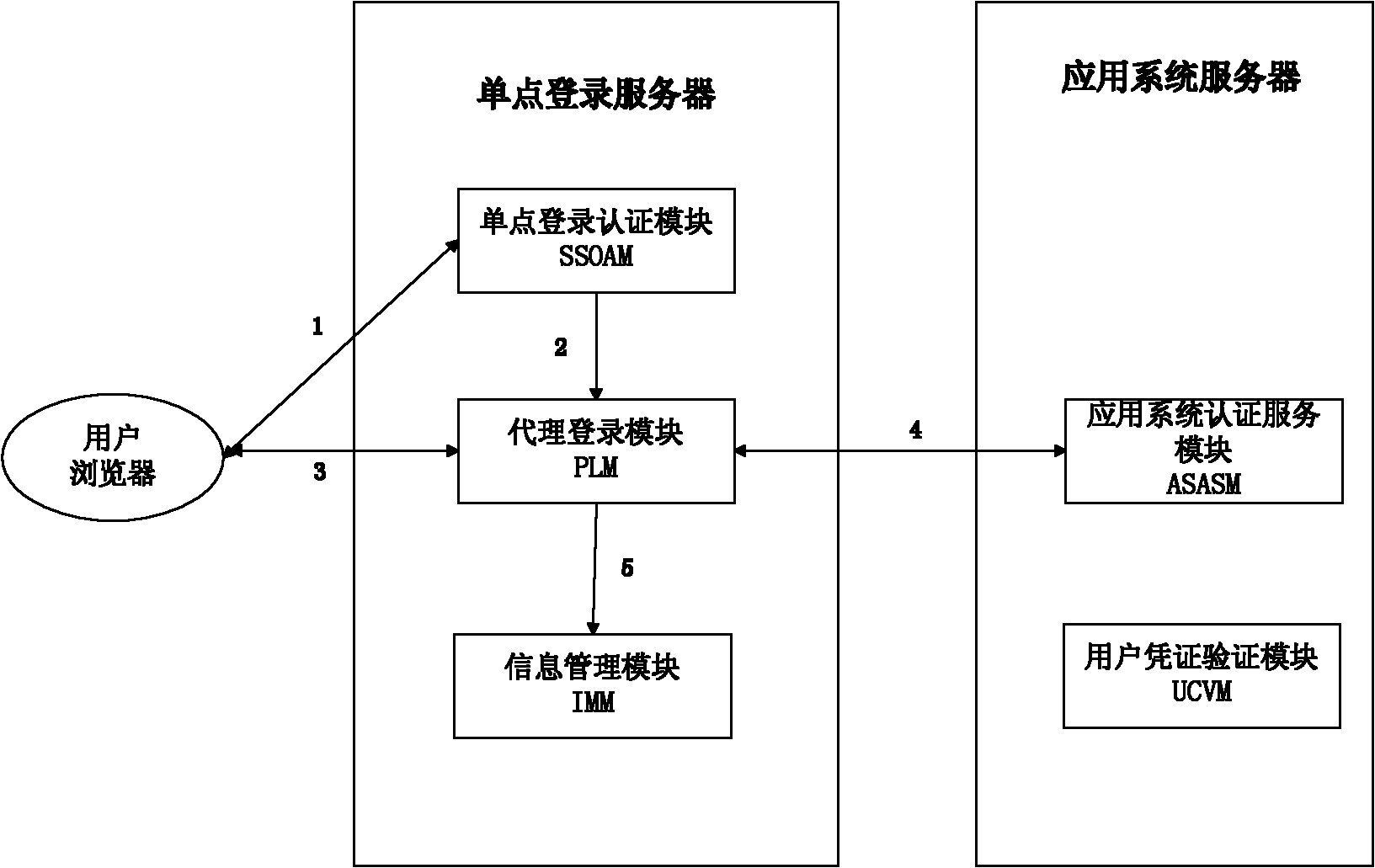
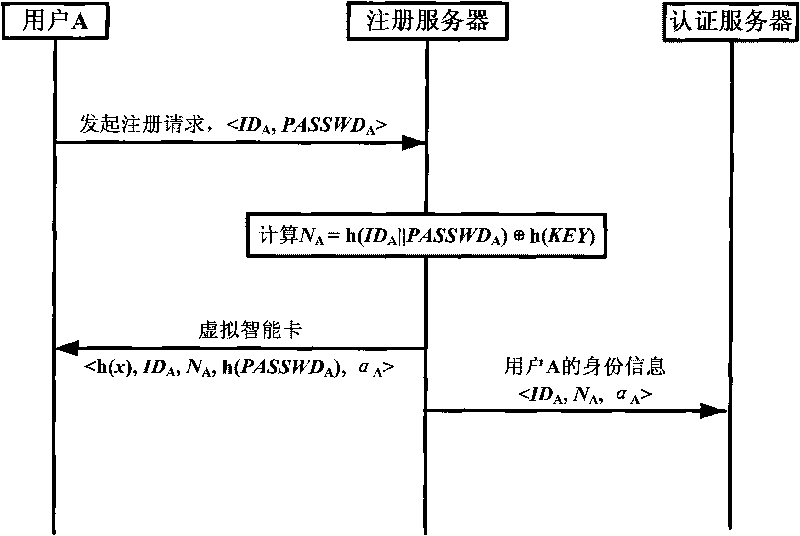
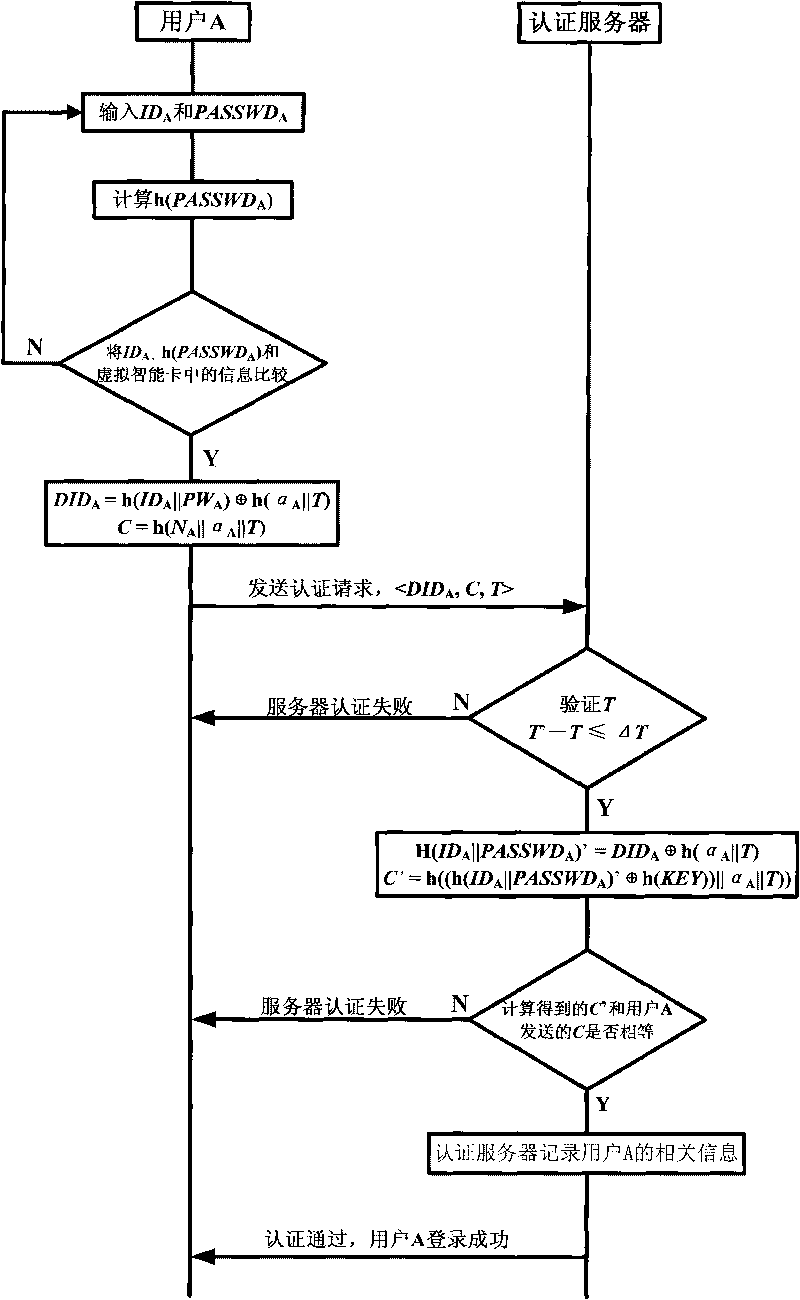
InactiveCN102111410AThe configuration cost is reasonableProtect personal privacyUser identity/authority verificationApplication serverCiphertext
The invention discloses an agent-based single sign on (SSO) method and system, belonging to the technical field of computer information. In the method, a user (U) registers and acquires a user certificate (C) in an application server (S); the U logs in an SSO server (L) and sends a certificate setting request; the L stores user identifications, application server identifications and ciphertext (C') in an associated manner; the U logs in the L and requests to access the S; the L is interacted with the S to acquire a token issued by the S and a signature (sig) of the S for the token; the L usesa self-private key to sign the token to acquire sig' and then searches the C' associated with the U identifications and the S identifications as well as sends the C', the token and the sig' to the U;the U uses a private key in the user C to decrypt c' so as to acquire C, and sends SSO server identifications, the C, the token and the sig' to the S; and the S verifies the token and the sig', if the token and the sig' pass the verification, the user C is continued to be verified; and if the user C passes the verification, the U is permitted to log in. The invention also discloses an SSO system corresponding to the SSO method.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Method for authenticating user identity through P2P service request
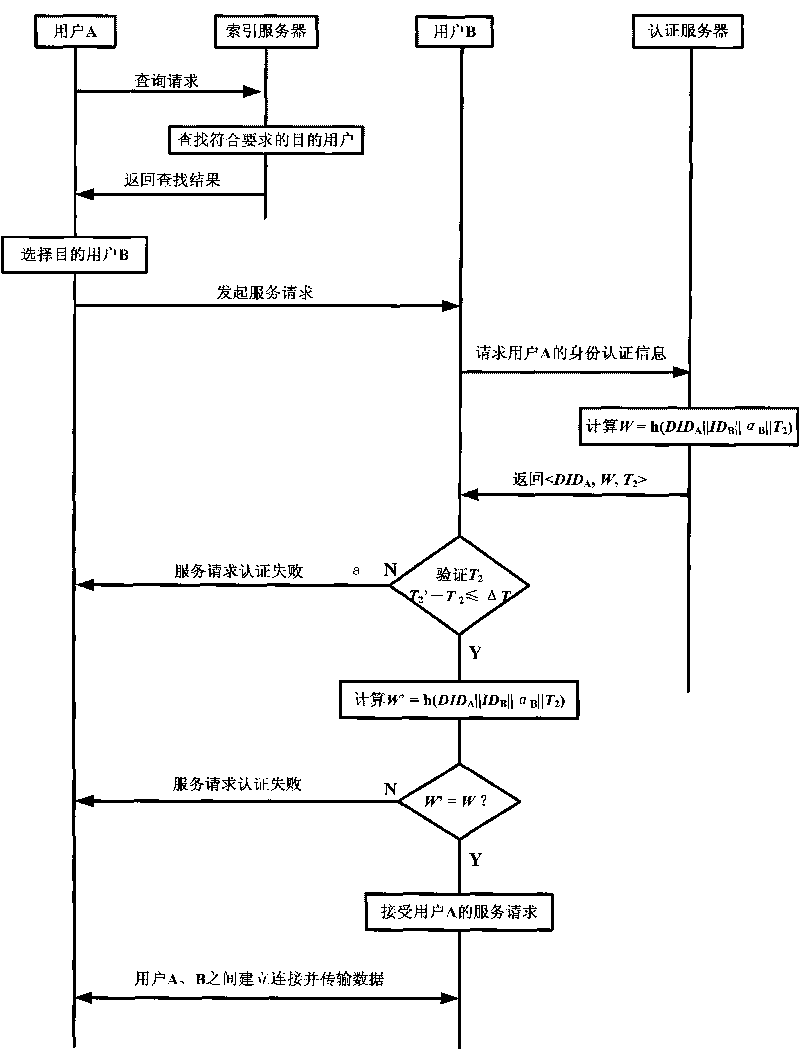
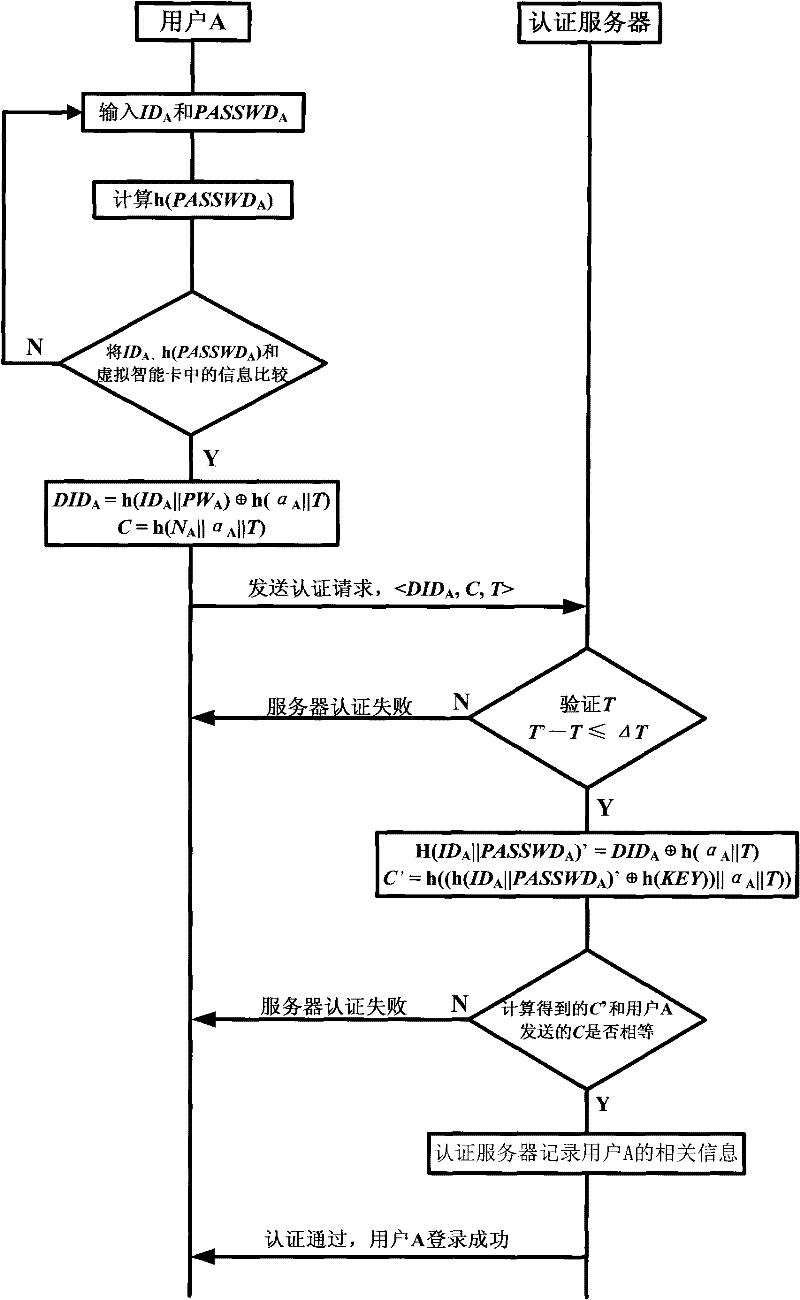
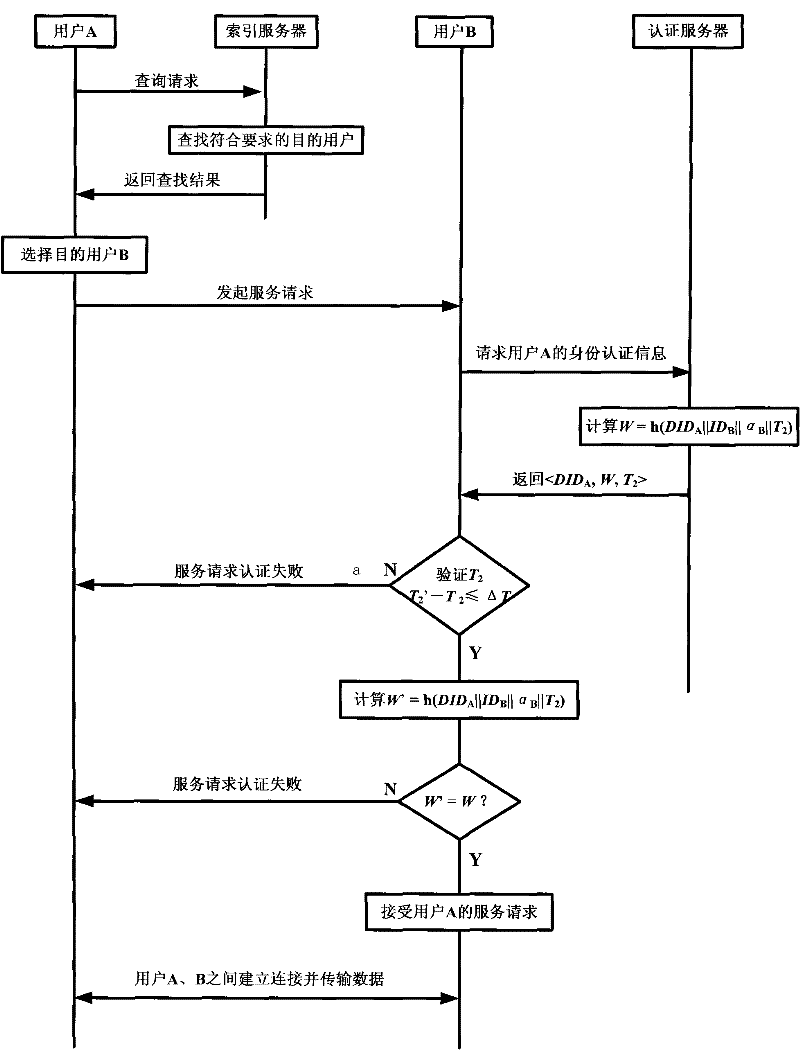
InactiveCN101697540ASituations that prevent loginDon't worry about leakingTransmissionPasswordUser input
The invention relates to a method for authenticating user identity through P2P service request. The prior P2P network authentication mode has certain limitations. The method for authenticating user identity comprises steps of: user registration, namely, a user obtains a legal account number after submitting a registration request to a server, and the user can log in a P2P network to acquire services by using the account number; login authentication, namely, the user inputs a user name and a password on a host computer provided with client software to log in an authentication server and perform identity authentication, and the login authentication comprises local login and server authentication; and service request authentication, namely, the user receiving a resource service request from the P2P network queries the authentication server to authenticate the identity of the user sending the request. The method adopts dual authentication in the process of the user identity authentication, so the safety factor is higher, and the same account number can be prevented from being logged in by a plurality of users at the same time; besides, the authentication server has no need of saving the password of the user, so the account number and the password of the user cannot be given away.
Owner:ZHEJIANG UNIV
Method, system, apparatus and storage medium for isolating user identity information
ActiveCN109005186ADon't worry about leakingAvoid the possibility of passive disclosureKey distribution for secure communicationUser identity/authority verificationUser privacyBlockchain
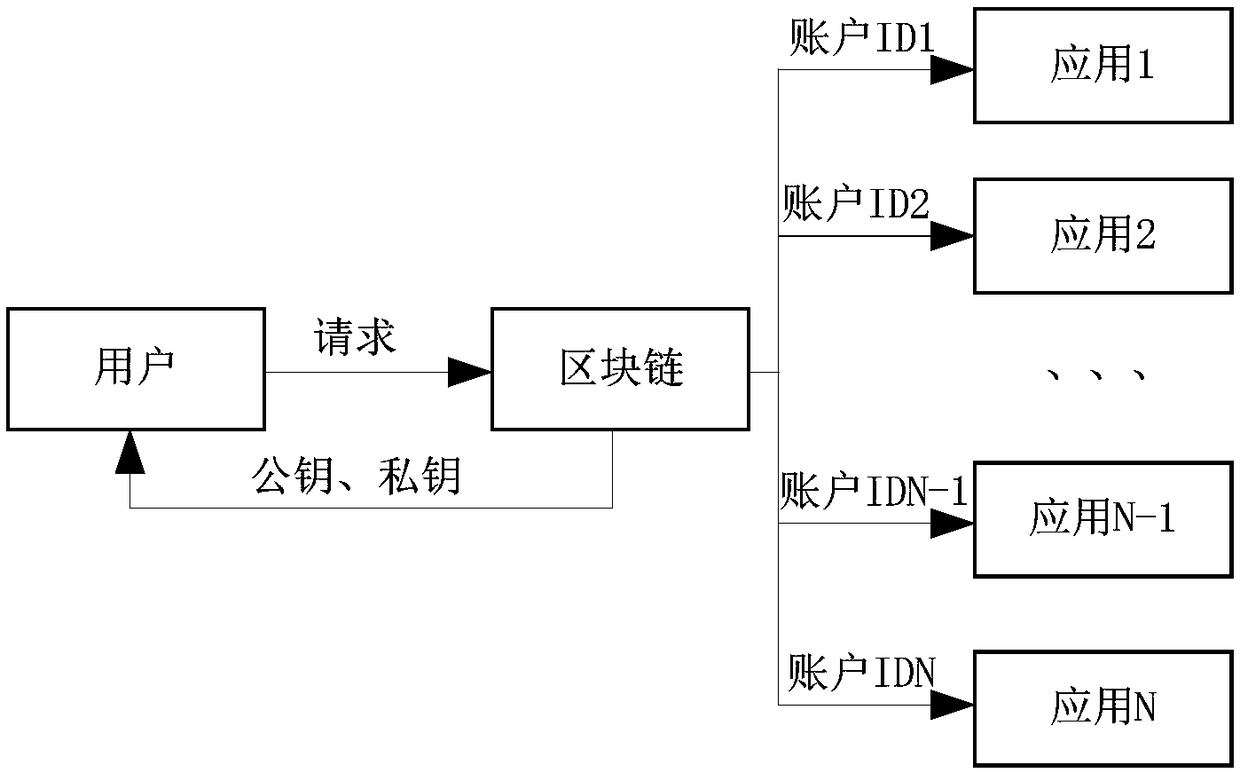
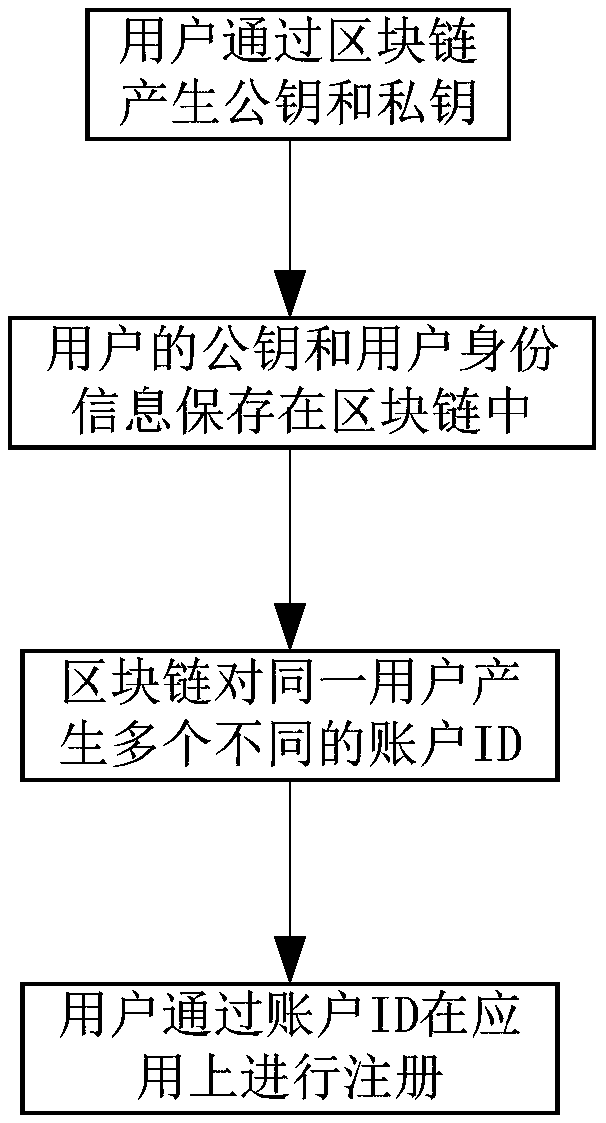
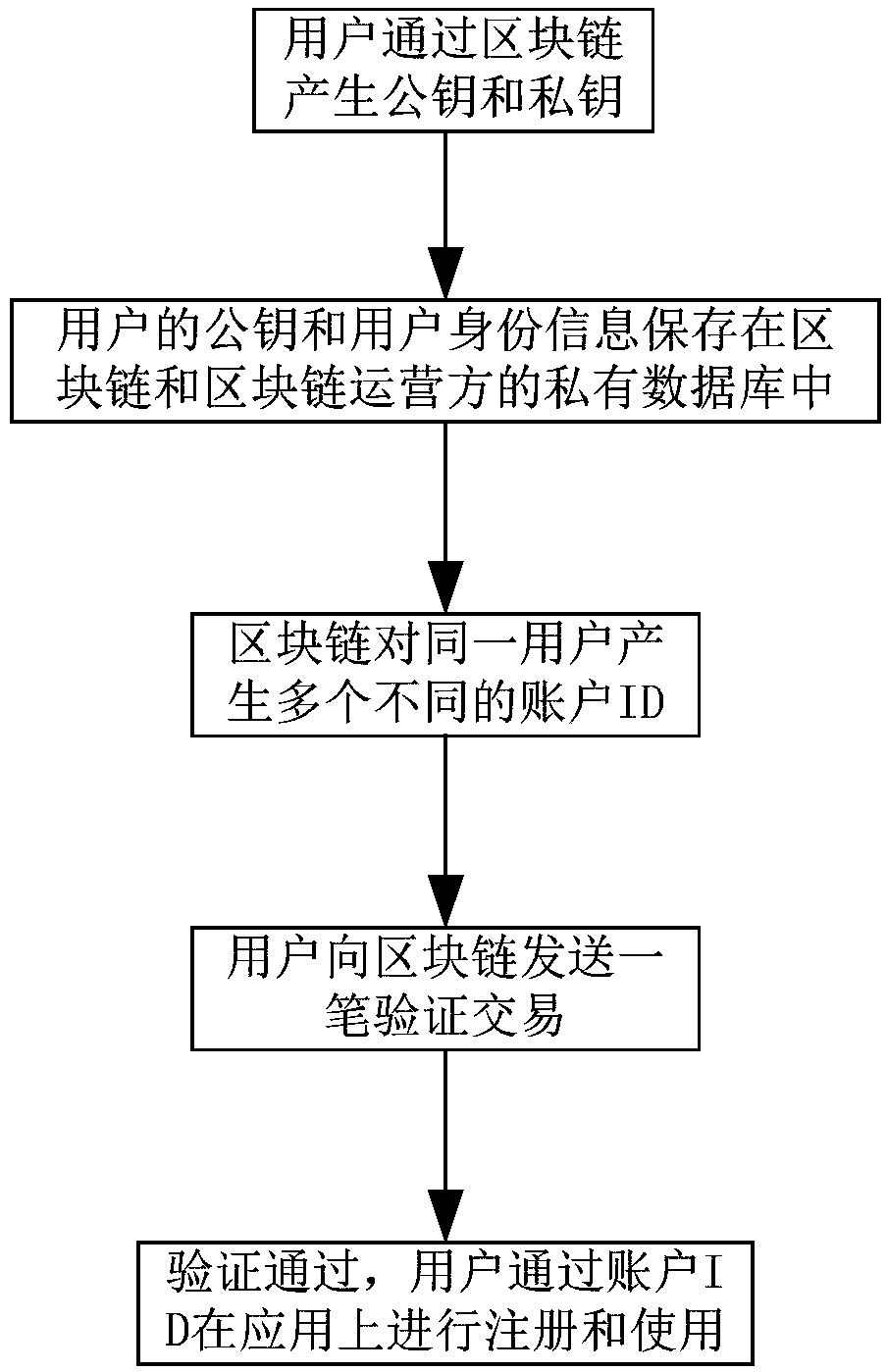
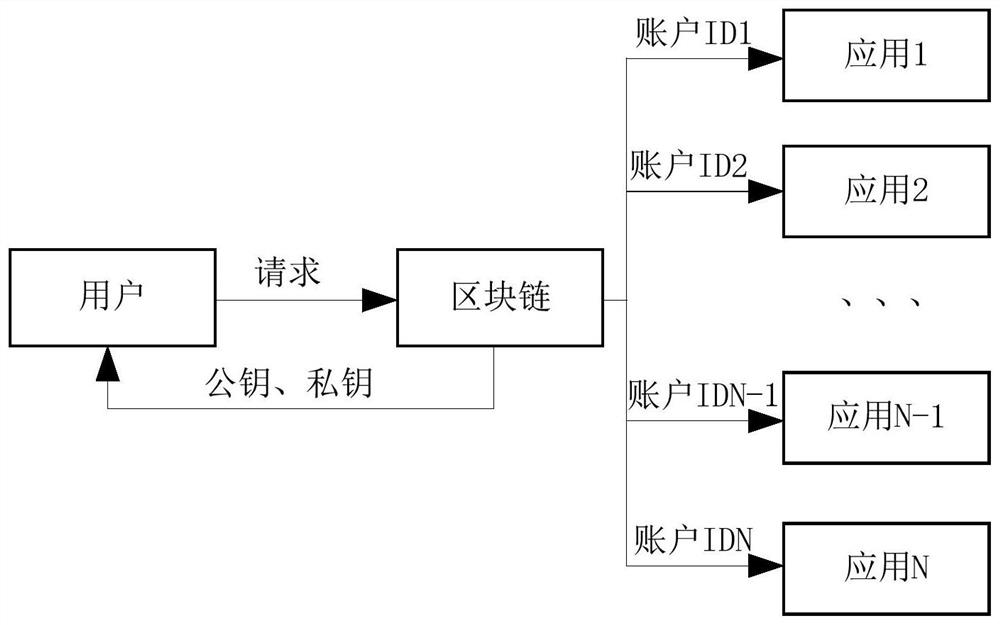
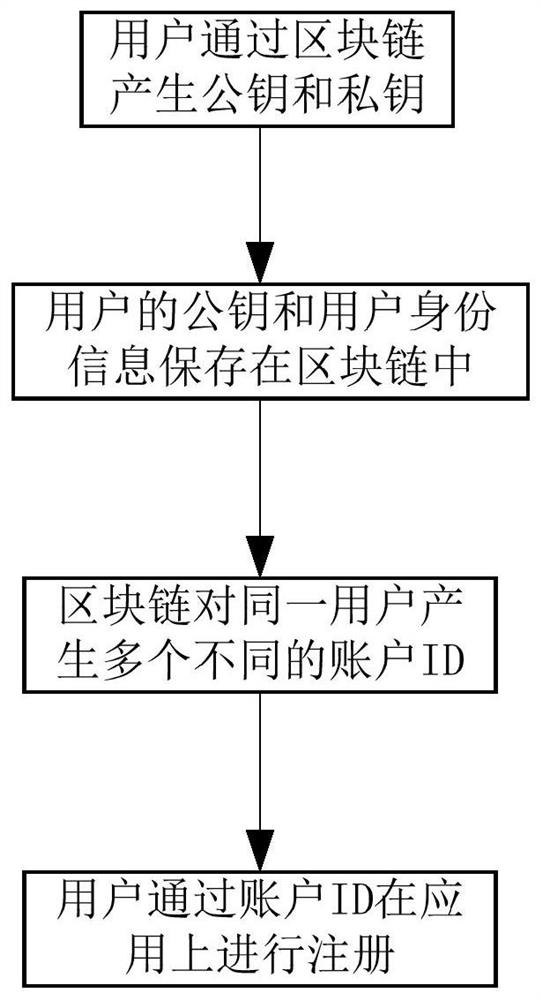
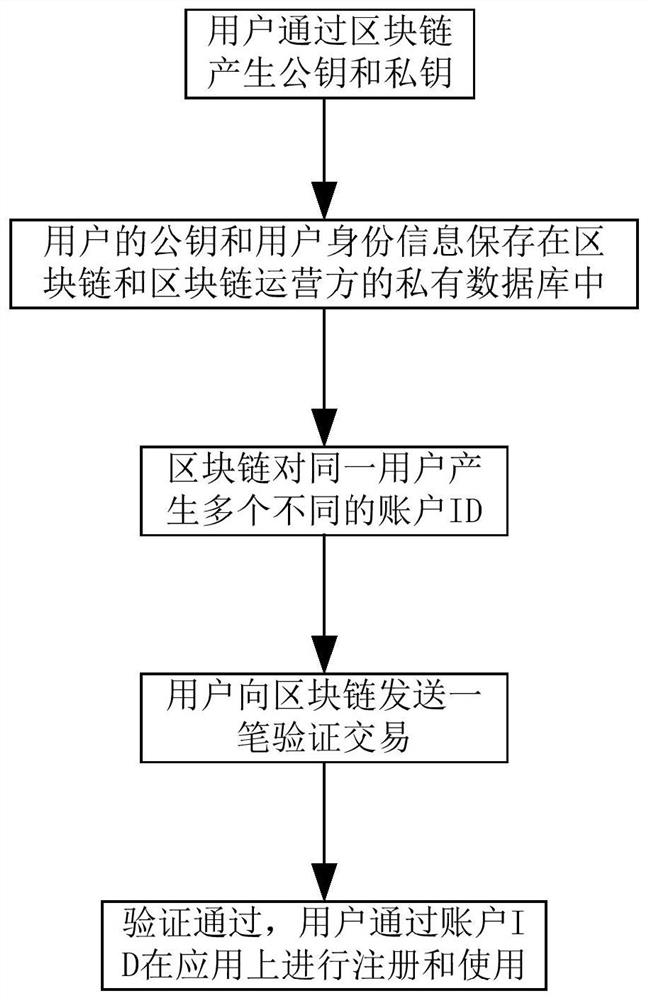
The invention discloses a method, a system, an apparatus and a storage medium for isolating user identity information, belonging to the technical field of block chains. The method comprises the following steps: a user generates a public key and a private key through a block chain, the user's public key and user's identity information are stored in the block chain; the block chain generates a plurality of different account IDs for the same user; the user registers on the application through the account ID. The invention also includes the corresponding system, apparatus and storage media, in view of the problem of user information disclosure, the invention can protect the privacy of the user and prevent the privacy of the user from being disclosed.
Owner:苏州交链科技有限公司 +1
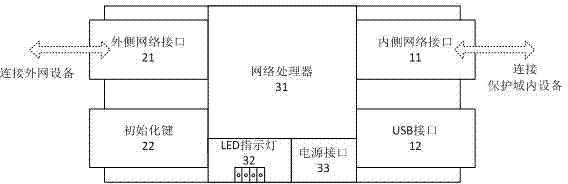
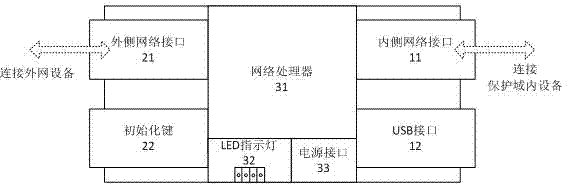
Device for establishing network isolated channel and method thereof
InactiveCN102316108AHighlight substantive featuresSignificant progressInternal/peripheral component protectionSecuring communicationThird partyVirtual network
The invention relates to a device for establishing a network isolated channel and a method thereof. A safe communication channel is established between two or multiple network devices through a network channel isolating device. The network channel isolating device is provided with an internal network interface and an external network interface. The internal network interface is connected with an internal network device. The external network interface is connected with an external network device. The network device which is connected with the internal network interface is protected by the network channel isolating device. A set of network devices protected by the network channel isolating device is called as a network channel isolating device protection domain. Host computers in different domains can communicate safely. By establishing a virtual network isolated channel through a public network among different geographic locations and by adopting an encryption algorithm recommended by the State Secrecy Bureau to conduct high-strength encryption to communication data, any third party cannot effectively decrypt the encrypted data and the communication data cannot be falsified; and the problem that different departments of small and medium enterprises cannot communicate safely through the public network is solved.
Owner:周伯生
Certificate making machine
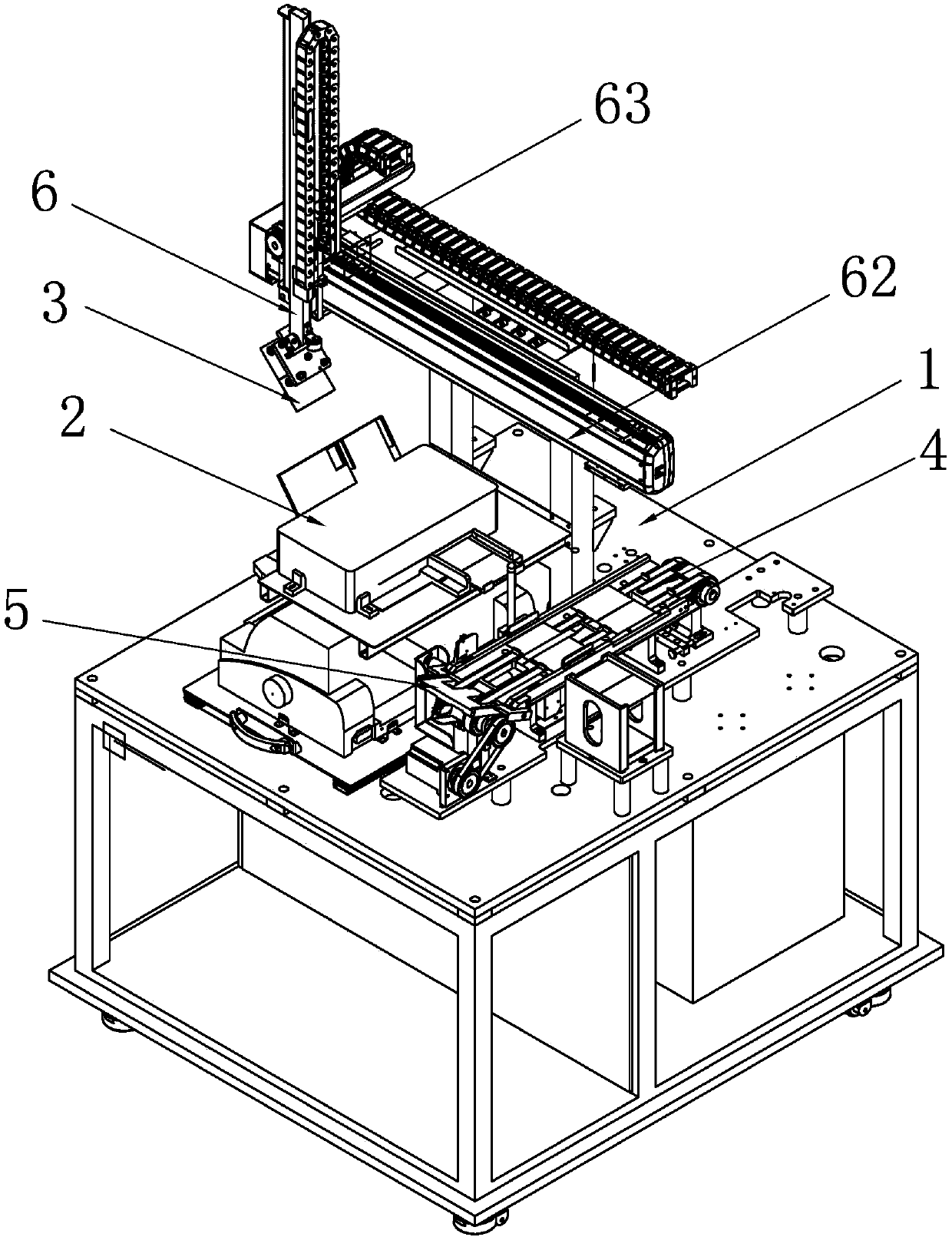
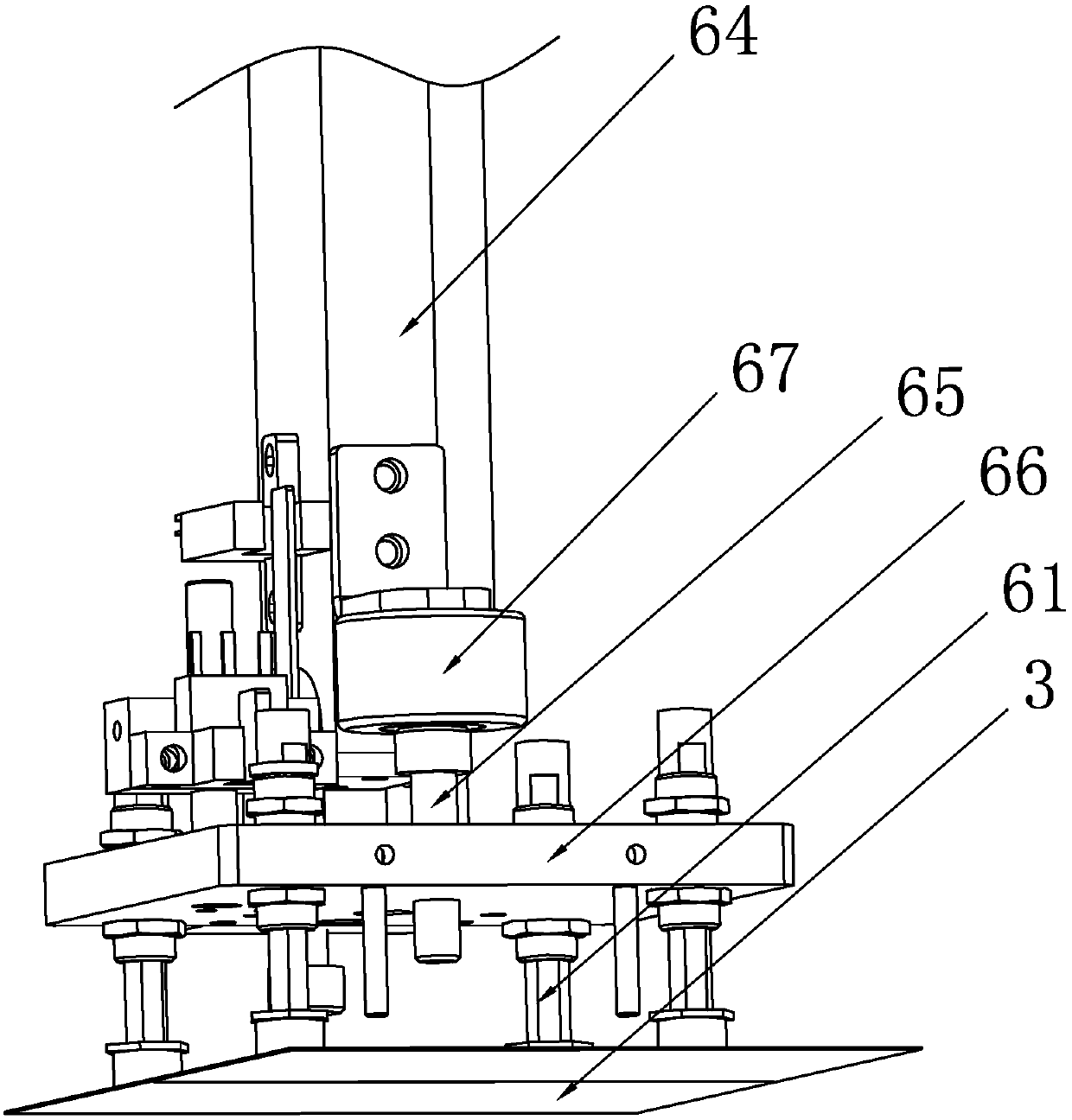
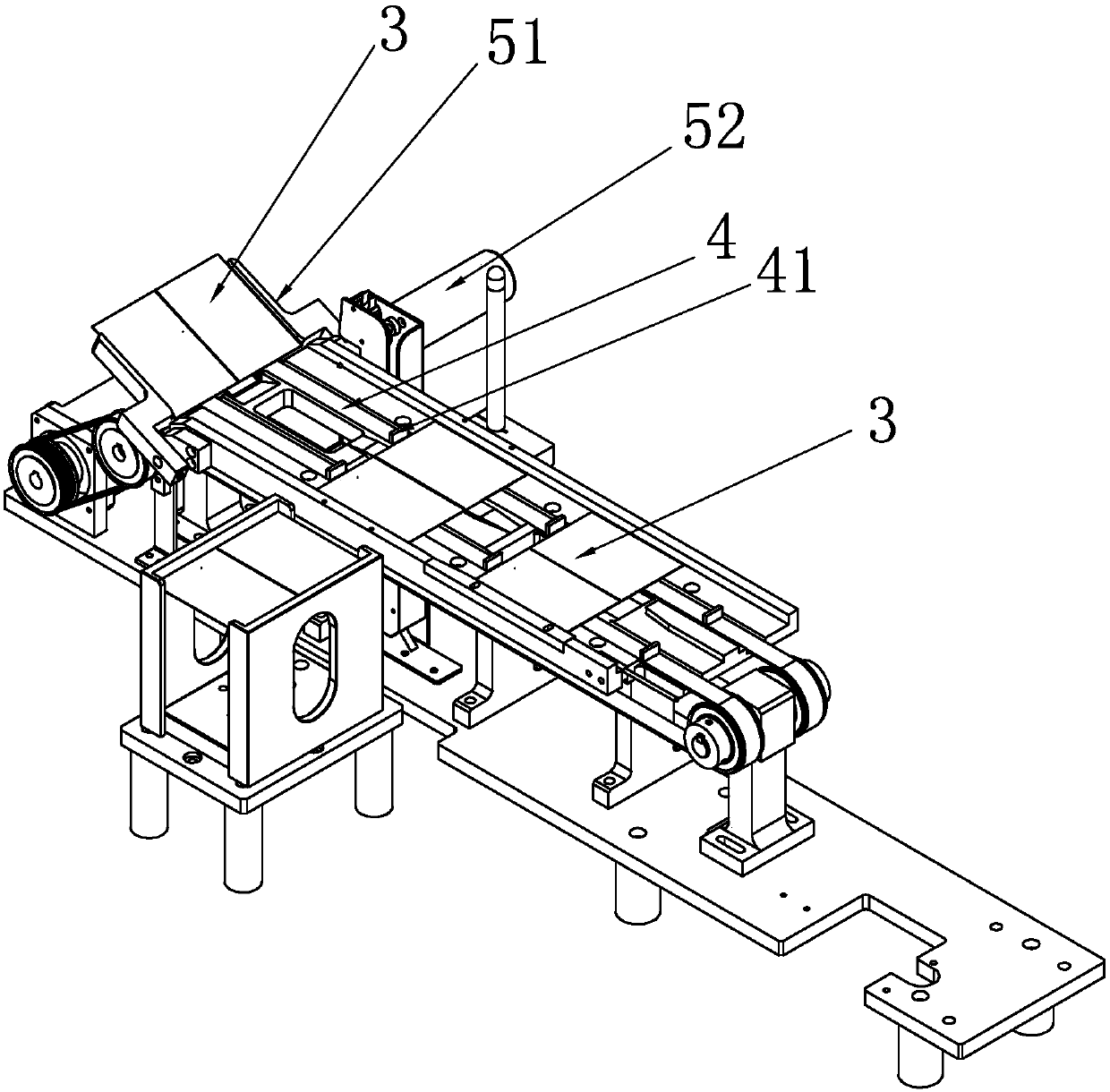
ActiveCN106865290ADon't worry about leakingImprove efficiencyOverturning articlesArticle feedersTectorial membranePulp and paper industry
The invention discloses a certificate making machine which comprises a printer, a conveyor belt, a turnover mechanism, a taking and putting mechanism and an assembling mechanism, wherein a turnover plate is cooperated with the conveyor belt to turn over certificate paper by 180 degrees; the taking and putting mechanism is arranged above the printer and the conveyor belt and travels to and fro between the printer and the conveyor belt to transfer the certificate paper; the assembling mechanism comprises a vacuum platform and a second vacuum sucking disc; the vacuum platform adsorbs the lower page of a protective film; and the second vacuum sucking disc adsorbs the upper page of the protective film. The certificate making machine adopts the second vacuum sucking disc to replace manual taking and putting of the certificate paper, turns over the certificate paper through the turnover plate and conveys the certificate paper through the conveyor belt, the protective film skillfully forms a V shape during film covering to facilitate insertion of the certificate paper; and the entire process is full-automatic, the efficiency is high, and high safety and reliability are realized without worrying about leakage of personal information.
Owner:珠海市技嘉科技有限公司
Method for protecting cipher of USB interface
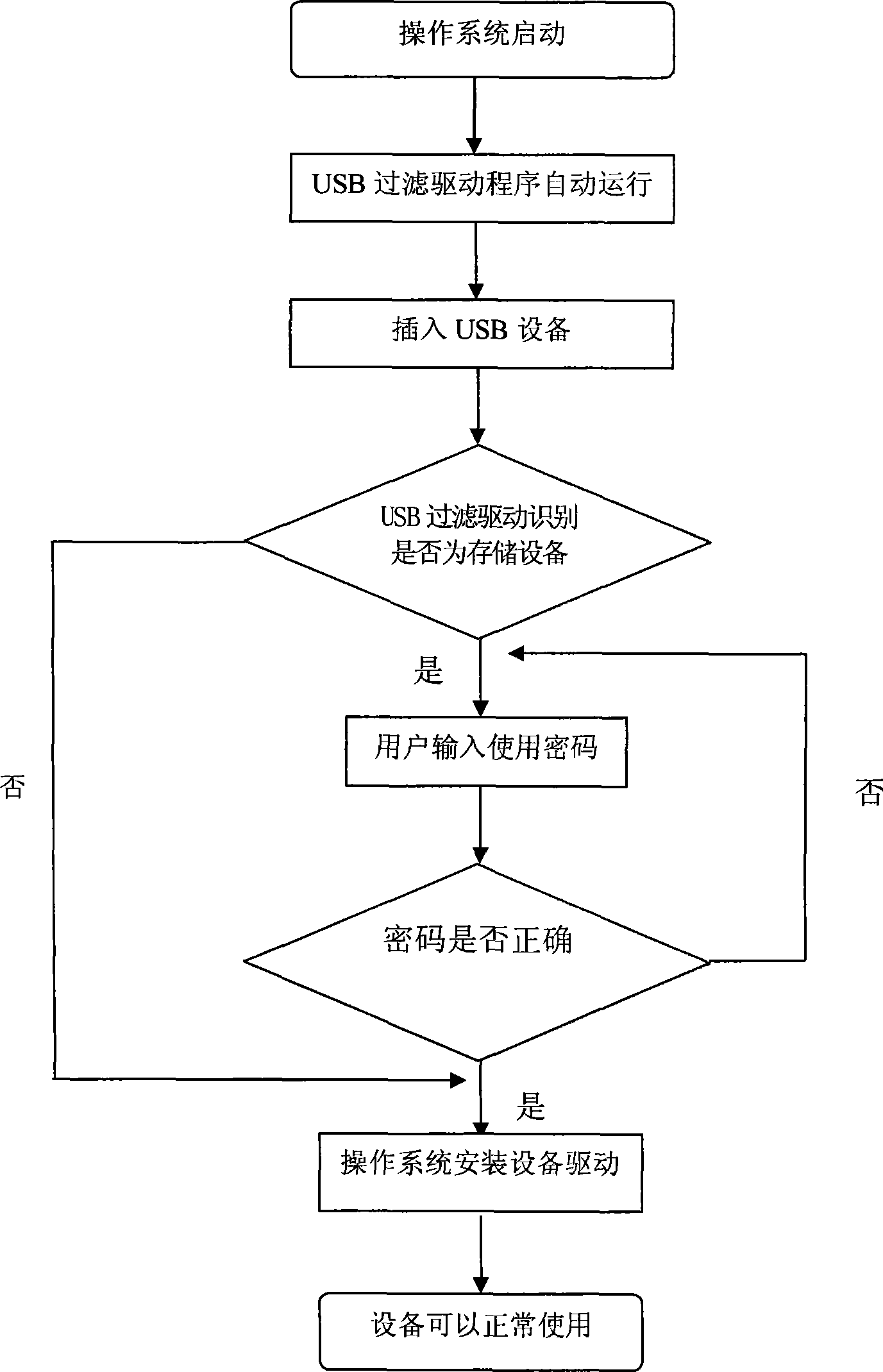
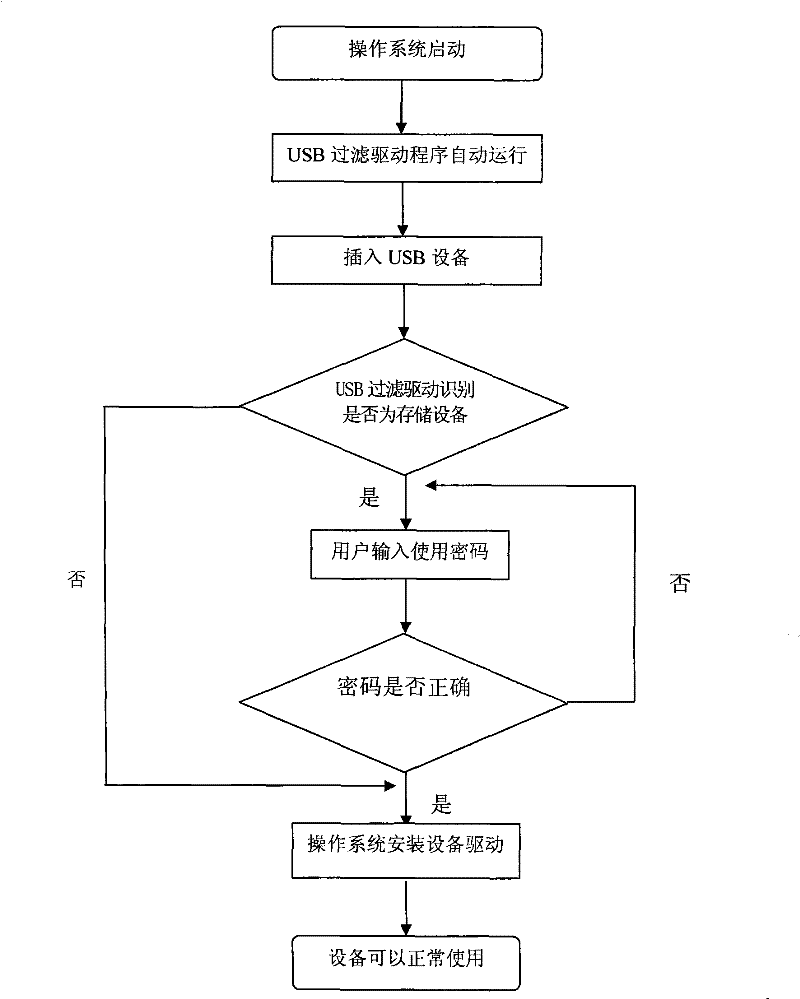
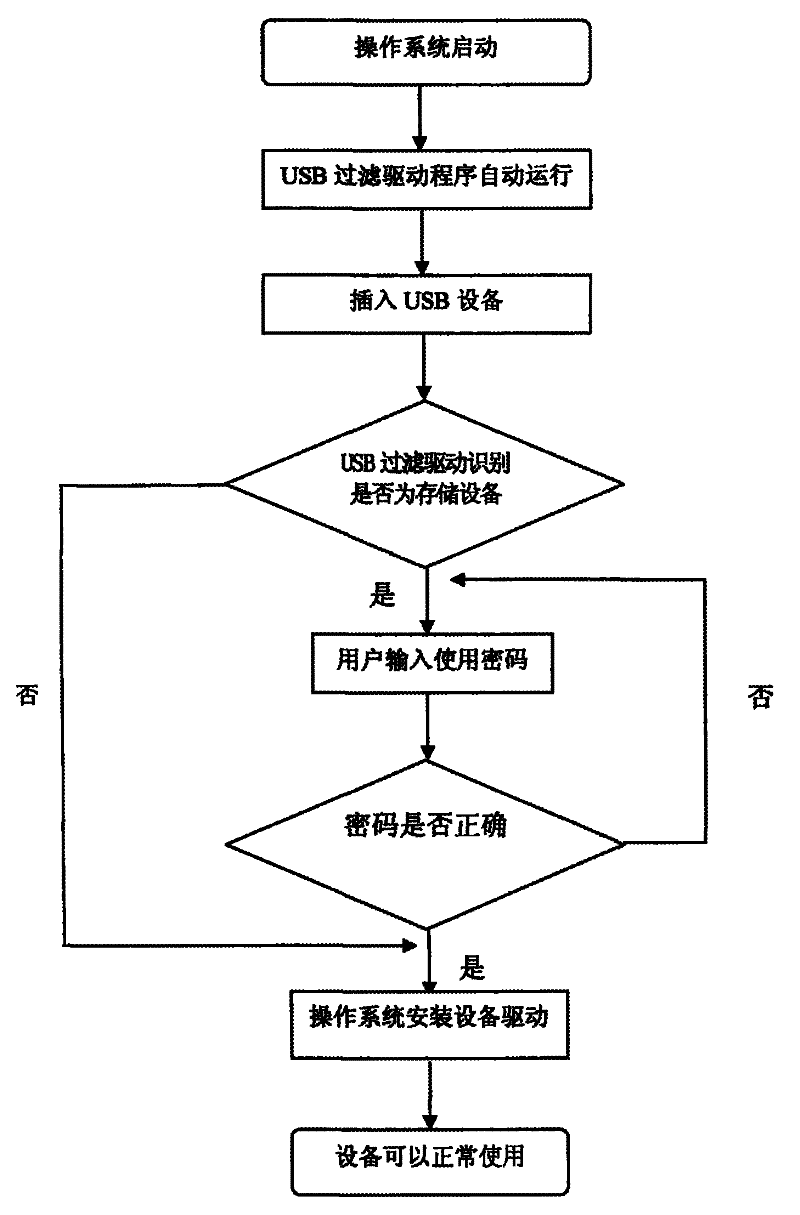
ActiveCN101533452ADon't worry about leakingEasy to useInternal/peripheral component protectionDigital data authenticationOperational systemUser input
The invention discloses a method for protecting a cipher of a USB interface, which is to set a layer of USB filtration drive in an operation system, and set a protection cipher for the USB interface. The method comprises the following steps that: 1) the USB filter drive is used to determine that whether equipment accessing to the USB interface is storage equipment or not; 2) when the accessing equipment is the storage equipment, a user is required to input a cipher, if the cipher is matched with the set protection cipher, the operation system loads drive of the equipment for the user, if not, the drive of the equipment is not loaded; if the accessing equipment is non-storage equipment, the operation system directly loads the drive of the equipment for the user. Type of the USB equipment can be identified by the method, so that the storage type USB equipment can be used through the cipher, the user can conveniently use the storage type equipment without worrying about leakage of classified document in a computer.
Owner:宏电脑上海
Aromatic insect-preventing vermifuge
ActiveCN102845416AHigh space insect repellent effectGood securityBiocideAnimal repellantsDiolInsect repellent
The invention provides an aromatic insect-preventing vermifuge used for preventing cloth injurious insects andor flying injurious insects. The aromatic insect-preventing vermifuge is a liquid-type aromatic insect-preventing vermifuge taking perfume element as the effective element. The aromatic insect-preventing vermifuge has good safety and has small volume. Even a container tilts down, the liquid of aromatic insect-preventing vermifuge does not leak. At the same time, the aromatic insect-preventing vermifuge can diffuse to space at an appropriate speed. The space preventing effect appears quickly and can last long. The aromatic insect-preventing vermifuge is characterized in that the perfume having insect-preventing and insect-expelling capacity and liquid perfume of diffusion-assisting agent containing at least one diol alcohol ether are diffused through a liquid perfume permeating film.
Owner:DAINIHON JOCHUGIKU CO LTD
Full decoupling steering-by-wire system
ActiveCN107672669ASolve the noise problemEliminate noise sourcesMechanical steeringElectrical steeringFailure rateSteering wheel
The invention discloses a full decoupling steering-by-wire system. The full decoupling steering-by-wire system is used for solving the problems that a motor in a traditional EPS is large in noise, andthe function of steering full decoupling needed by an intelligent automobile cannot be achieved; mechanical connection between a steering wheel and a steering wheel is omitted in parts of steering-by-wire systems, and consequently, efficacy-losing steering cannot be completed when the systems are powered off and lose efficacy; when the parts of the steering-by-wire systems adopts motors as steering-by-wire power sources, the noise is large, and the response speed is low; and when the parts of the steering-by-wire systems adopts liquid or gas as a steering medium, leakage occurs, the failure rate is increased, and maintenance is difficult. According to the full decoupling steering-by-wire system, electromagnetic force is adopted to drive a steering rod to move, so that an automobile completes a steering action rapidly and precisely; and the full decoupling steering-by-wire system can achieve full decoupling of a driver and the steering system, has the efficacy-losing protection function, and is free from constraints of the motors, the liquid and the gas, simple in structure and high in integration level.
Owner:JILIN UNIV
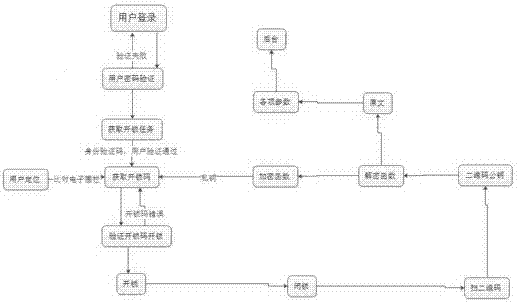
Multiple determination safety mechanism with identity recognition and movable location based on Internet of Things
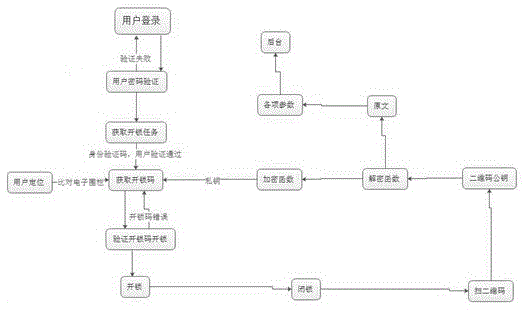
ActiveCN105632002AAdd security checkDon't worry about leakingIndividual entry/exit registersTransmissionUser needsIdentity recognition
The invention relates to a multiple determination safety mechanism with identity recognition and movable location based on Internet of Things. The safety mechanism is characterized by comprising the following steps: S10, a mobile terminal APP sends address information to a WEB terminal in real time after networking, a user logs in a user account at the mobile terminal APP, wherein the log-in is successful after passing verification at the WEB terminal, and the user clicks an unlocking task sent to the mobile terminal APP by the WEB terminal before, and applies to acquire an unlocking code by verifying personal passwords at the WEB terminal; S20, the WEB terminal verifies the address information received at the last step after receiving the unlocking code application, and continues to verify the received personal password after comparing the address information received at the last step with stored address information corresponding to the unlocking task and determining the address information is correct, and after the received personal password passes verification, the WEB terminal sends an unlocking private key to the mobile terminal APP; and S30, the unlocking private key is input to a dynamic code lock of an ATM, wherein if the unlocking private key is correct, the unlocking is successful, and if the unlocking private key is wrong, the user needs to go back to S10.
Owner:上海杰盛立业网络科技有限公司
Security and protection method for achieving security and protection function of mobile phone
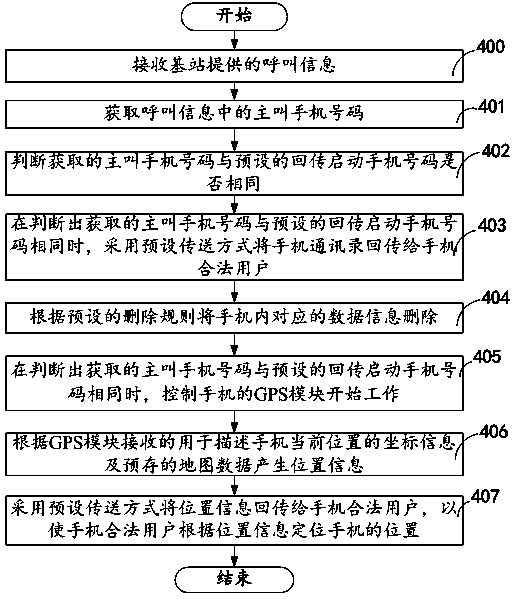
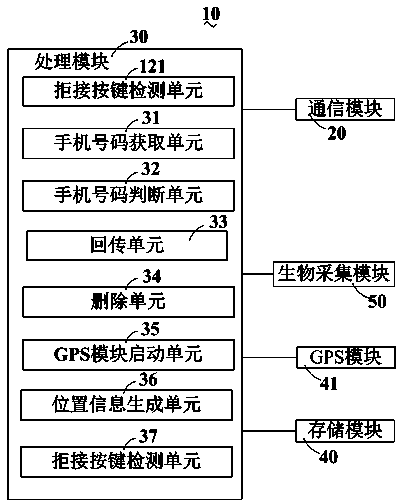
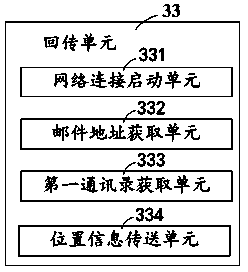
InactiveCN104270715ADon't worry about leakingCommmunication supplementary servicesSubstation equipmentData informationMobile phone
A security and protection method for achieving a security and protection function of a mobile phone comprises the following steps of receiving calling information supplied by a base station, obtaining a calling mobile phone number in the calling information, judging whether the obtained calling mobile phone number and a preset postback start mobile phone number are consistent, sending a mobile phone address list back to a legitimate user of the mobile phone when it is judged that the obtained calling mobile phone number and the preset postback start mobile phone number are consistent, and deleting corresponding data information in the mobile phone according to preset deletion rules.
Owner:NINGXIA TIANZONG HONGGUANG COGENERATION TECH
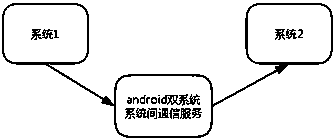
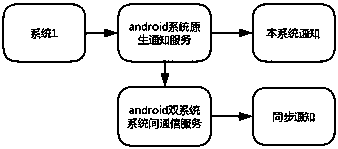
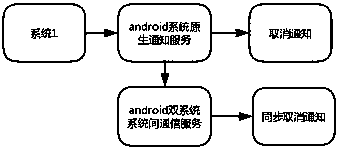
Inter-system notice synchronization method based on dual Android systems
ActiveCN108390989AHighlight substantiveSignificant progressInterprogram communicationSubstation equipmentComputer moduleDistributed computing
The invention provides an inter-system notice synchronization method based on dual Android systems, wherein a first Android system and a second Android system are provided, and each Android system ispreconfigured with a synchronous sending module, a synchronous canceling module and a synchronous receiving module; the synchronous sending module, the synchronous canceling module and the synchronousreceiving module are respectively added into a notice management module of each Android system; when sending a synchronous notice message, the synchronous sending module calls an interface of a communication service between the Android systems to notify the other Android system with the synchronous notice message; when canceling sending of the synchronous notice message, the synchronous cancelingmodule calls the interface of the communication service between the Android systems to notify the other Android system with the synchronous notice message; and when receiving the synchronous notice message, the synchronous receiving module calls the interface of the communication service between the Android systems to receive the synchronous notice message from the other Android system.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
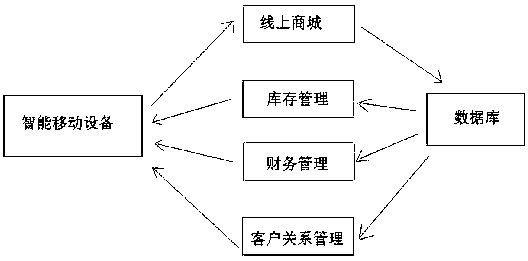
Cloud general store management system
PendingCN107657432AGuaranteed performance flexibilityReduce management costsOffice automationData switching networksEngineeringServer
The invention discloses a cloud general store management system comprises the components of more than one frontend intelligent mobile device, a backend database, and multiple layers of cloud platformswhich are arranged between the frontend intelligent mobile device and the backend database. The intelligent mobile device uploads information to the database through the local-layer cloud platform which is in signal connection with the intelligent mobile device. The intelligent mobile device downloads the information from the database through an upper-layer cloud platform which is in signal connection with the intelligent mobile device. The cloud general store management system has advantages of reducing user management cost, improving user management efficiency, improving user data safety and improving user accessing performance. The cloud server can be quickly upgraded and expanded according to the requirement, thereby ensuring quick response on the condition of increasing visiting amount.
Owner:江苏岳创信息科技有限公司
Portable terminal cradle
InactiveCN107074161AImprove bindingEasy to separateSecuring devicesStands/trestlesMechanical engineering
Owner:尹良俊
Artificial muscle and simulation arm
PendingCN108927787AImplement shrink functionReduce usageProgramme-controlled manipulatorArmsMagnetic polesEngineering
The invention is applicable to the technical field of robots, and provides artificial muscle and a simulation arm with the artificial muscle. The artificial muscle comprises a driving unit, wherein the driving unit comprises a controller, a first electromagnet electrically connected with the controller, a second electromagnet electrically connected with the controller and a telescopic mechanism with two ends connected with the first electromagnet and the second electromagnet correspondingly, and the magnetic poles of the adjacent ends of the first electromagnet and the second electromagnet aredifferent. According to the provided artificial muscle, the use of the ionic polymer is avoided, a liquid solvent does not need to be used, then the problem of liquid leakage does not need to be worried about, a closed environment does not need to be designed, and the structure is simple.
Owner:魏相东
Bag clamping mechanism
The invention relates to a bag clamping mechanism comprising a feeding hopper; the lower portion of the feeding hopper is communicated with a body; a first rib plate and a first upper mounting plate are arranged on one side of the bottom edge of an upper body flange mounting face of the body; a second rib plate and a second upper mounting plate are arranged on the other side of the upper body flange mounting face of the body; a first bag clamping arm mounting plate and a second bag clamping arm mounting plate are arranged on the two sides of the middle of the body respectively; a travel switch mounting plate is arranged on the upper middle portion of the body; bag opening mechanisms are symmetrically arranged on the first upper mounting plate and the second upper mounting plate; the bag opening mechanisms comprise push-pull air cylinder hinge frames; and the push-pull air cylinder hinge frames are installed on the upper portion of the first upper mounting plate and the upper portion of the second upper mounting plate. The structural design of symmetrically opening and clamping bags is adopted, the whole mechanism is designed on the body, the structure is compact, and mounting is convenient. The bag opening distance of bag opening rods can be adjusted through the push-pull structures, and the requirements of packaging bags of various specifications in the market are met.
Owner:WUXI NAITE ELECTROMECHANICAL INTEGRATING TECH
High-selectivity aggregation induced chemiluminiscence probe for <1>O2 as well as preparation method and application of chemiluminiscence probe
ActiveCN108727277AEnsuring energy transfer efficiencyHigh selectivityOrganic chemistryFluorescence/phosphorescenceHigh selectivityTetrahydrofuran
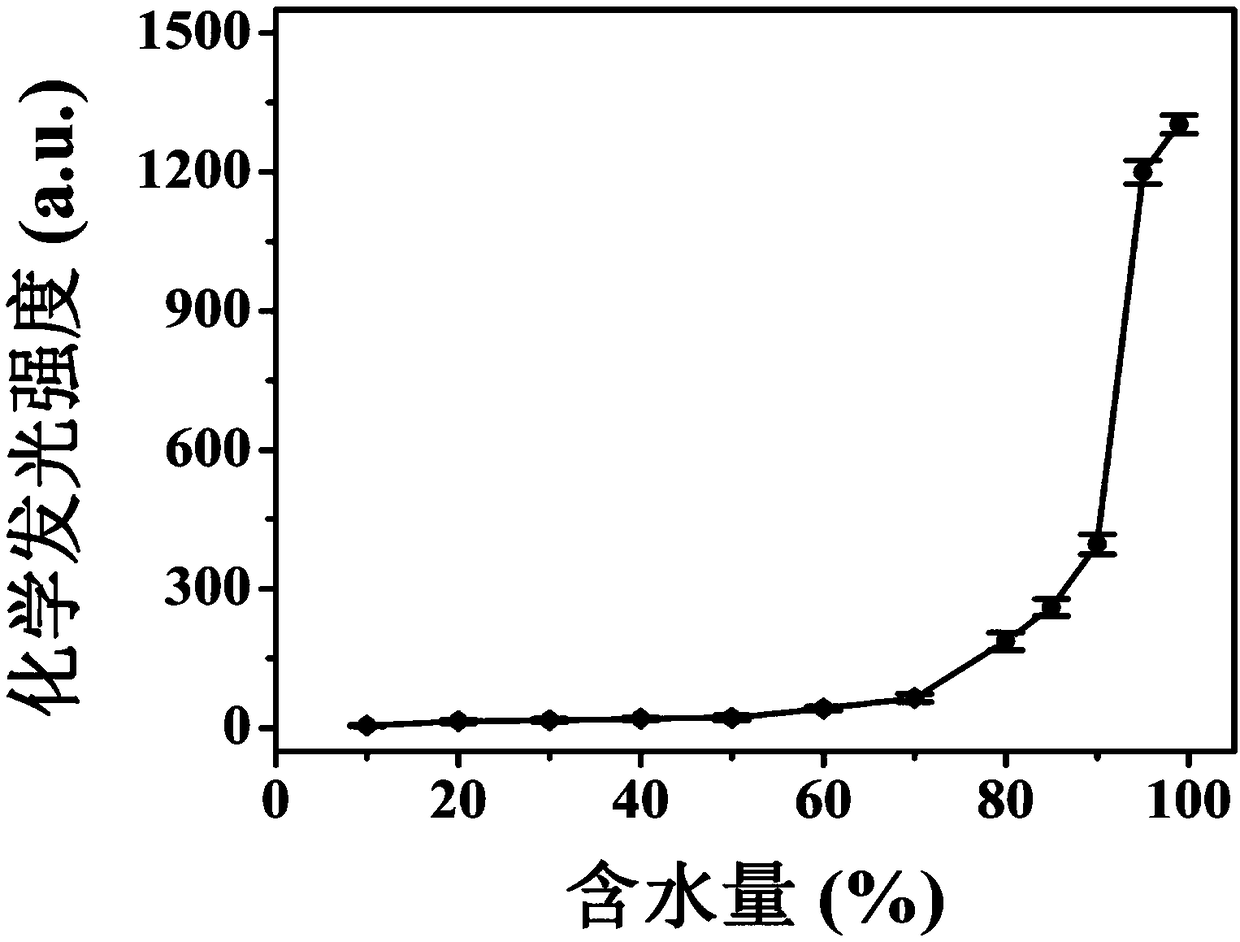
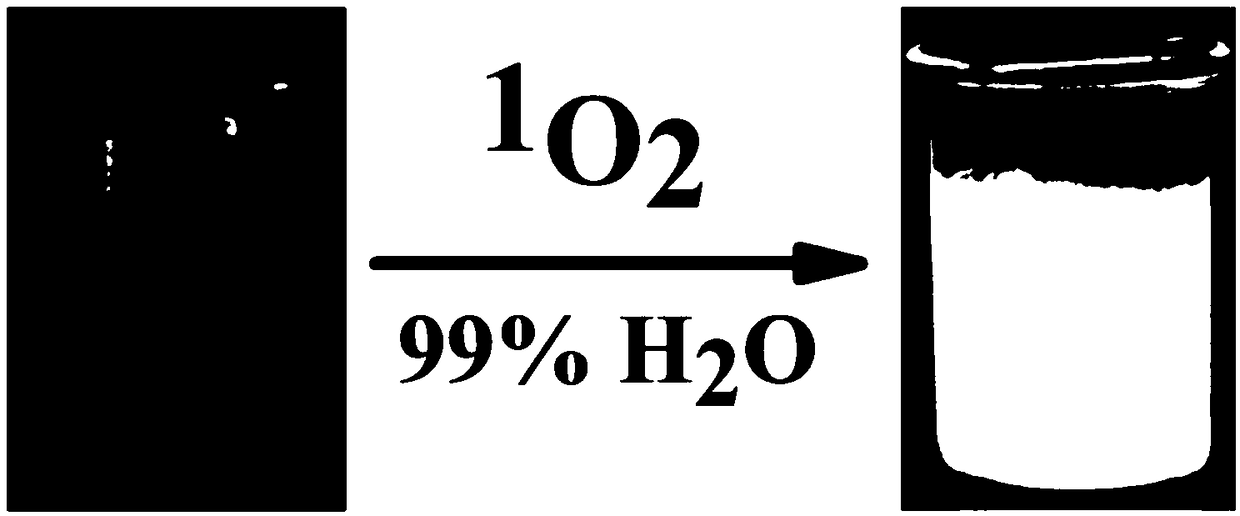
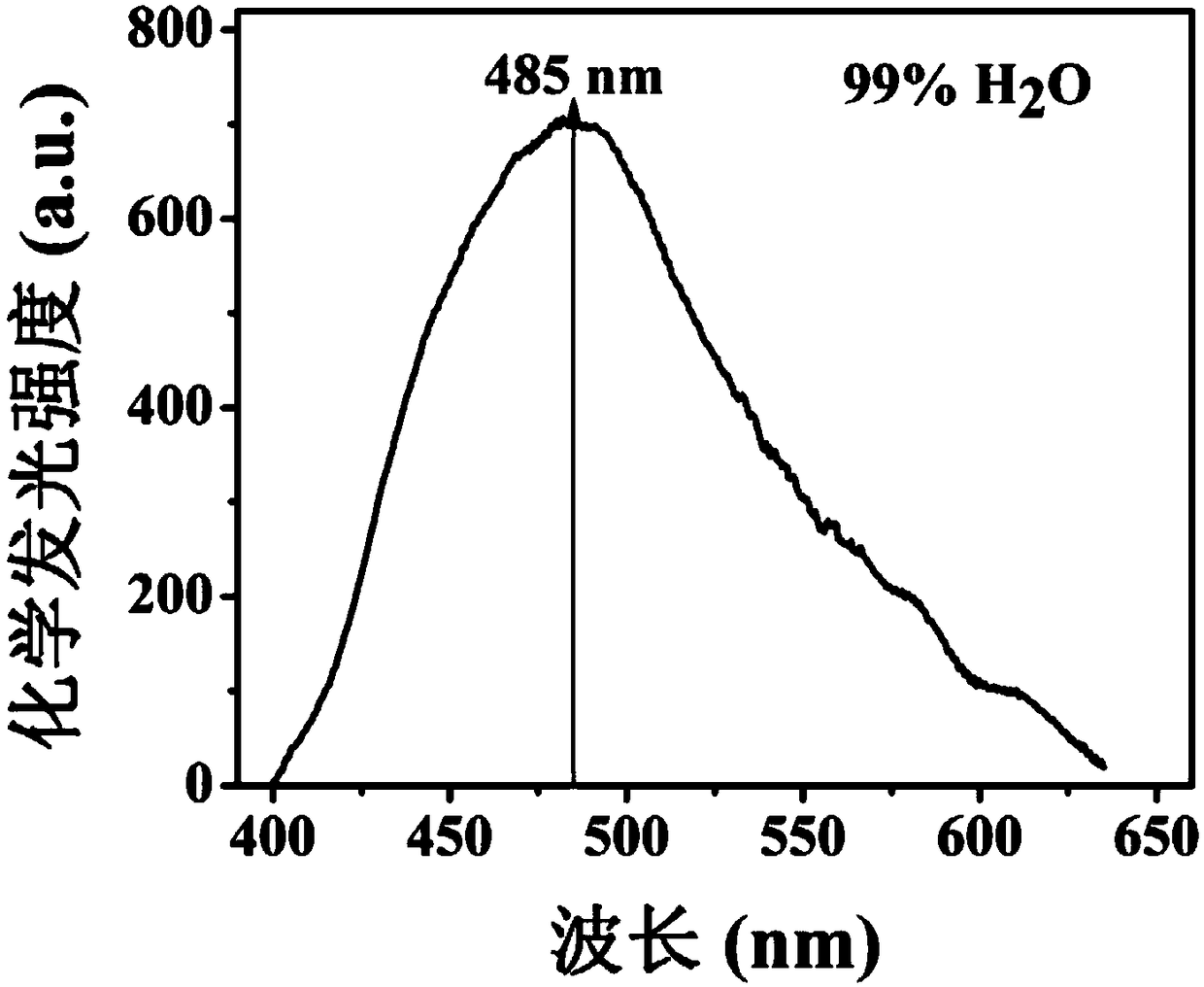
The invention discloses a high-selectivity aggregation induced chemiluminiscence probe for <1>O2 as well as a preparation method and an application of the chemiluminiscence probe. The structural formula of the chemiluminiscence probe is shown in the description, and the chemical name is 6-(4-(1,2,2-triphenylethyl)phenyl)-2,3-dihydrophthalazine-1,4-dione (TPE-PH for short). Chemiluminiscence of theprobe is weak when a solution is formed by the probe in a good solvent such as tetrahydrofuran. In a tetrahydrofuran-water mixed solvent, when proportion of water is larger than 70% (V / V), chemiluminiscence produced when formed nano-aggregate is oxidized by <1>O2 is enhanced sharply with increase of the proportion of water in the mixed solvent, the probe has typical aggregation induced reinforcedchemiluminiscence characteristic, and emission wavelength peak is 485 nm. The TPE-PH nano-aggregate has quite high chemiluminiscence selectivity for <1>O2 under physiological conditions and can recognize <1>O2 on nanomole level, which proves that TPE-PH is a novel chemiluminiscence probe capable of recognizing and detecting <1>O2 with high selectivity and high sensitivity in a physiological system.
Owner:SHAANXI NORMAL UNIV +1
Device integrating pneumatic conveying, fully-mechanized excavating and supporting
ActiveCN106894836ADon't worry about leakingAvoid safety hazardsMine roof supportsCantileverIndustrial engineering
The invention discloses a device integrating pneumatic conveying, fully-mechanized excavating and supporting. The device comprises a rail, a pneumatic traction device and a supporting device, wherein the rail is fixedly mounted at the top of a tunnel, the pneumatic traction device is mounted on the rail, the supporting device is driven by the pneumatic traction device to move along the rail, the support device comprises a supporting platform, a cantilever and a bottom rack for being hung on the rail, one end of the cantilever is hinged to the bottom rack, and the other end of the cantilever is connected with the supporting platform; a first support air cylinder is connected to the lower portion of the supporting platform, and the push rod of the first support air cylinder extends downwardly and can be supported on the ground; one end of the cylinder barrel of a second support air cylinder is hinged to the bottom rack, and the push rod of the second support air cylinder is hinged to the lower portion of the cantilever. The device integrating pneumatic conveying, fully-mechanized excavating and supporting can move on the rail to an appointed supporting operation positon to perform supporting operation and is affected by tunnel terrain.
Owner:北京双泰气动设备有限公司 +2
A method, system, device and storage medium for isolating user identity information
ActiveCN109005186BDon't worry about leakingAvoid the possibility of passive disclosureKey distribution for secure communicationUser identity/authority verificationUser privacyEngineering
The present invention relates to the technical field of blockchains. Disclosed are a method and system for isolating user identity information, a device, and a storage medium. The method comprises: a user generates a public key and a private key by means of a blockchain; save the public key and user identity information of the user in the blockchain; generate, by means of the blockchain, multiple different account IDs for the same user; the user registers on an application by means of the account IDs. A corresponding system, a device, and a storage medium are also comprised. With regard to the user information leakage problem, the method can protect the privacy of the user, and prevent the privacy leak of the user.
Owner:苏州交链科技有限公司 +1
Mobile phone with security and protection function
InactiveCN104284026ADon't worry about leakingSubstation equipmentMobile Telephone NumberData information
A mobile phone with the security and protection function comprises a communication module and a processing module. The communication module receives calling information provided by a base station; the processing module comprises a mobile phone number obtaining unit, a mobile phone number judgment unit, a back transmission unit and a deleting unit; the mobile phone number obtaining unit obtains a calling mobile phone number in the calling information; the mobile phone number judgment unit outputs a preset first transmission signal to the back transmission unit when judging that the obtained calling mobile phone number is the same with the preset back transmission starting mobile phone number; the back transmission unit responds to the first transmission signal, and provides a mobile phone address list to the communication module in a preset transmission mode so as to transmit the mobile phone address list back to a valid mobile phone user; the back transmission unit outputs a preset deleting signal to the deleting unit; the deleting unit responds to the deleting signal and deletes corresponding data information in a mobile phone according to the preset deleting rule.
Owner:NINGXIA TIANZONG HONGGUANG COGENERATION TECH
Pneumatic temporary support device for fully-mechanized excavating
The invention discloses a pneumatic temporary support device for fully-mechanized excavating. The pneumatic temporary support device comprises a support platform, a cantilever and a bottom rack used for being hung on a rail, wherein one end of the cantilever is hinged to the bottom rack, and the other end of the cantilever is connected to the support platform; a first support air cylinder is connected to the lower portion of the support platform, and the push rod of the first support air cylinder extends out downwardly to support the ground; one end of the cylinder barrel of a second support air cylinder is hinged to the bottom rack, and the push rod of the second support air cylinder is hinged to the lower portion of the cantilever. The pneumatic temporary support device has the advantages that the support device can be hung on the rail and moved to an appointed support operation position to perform support operation, and the support device is unaffected by tunnel terrain.
Owner:北京双泰气动设备有限公司 +2
Agent-based single sign on (SSO) method and system
InactiveCN102111410BThe configuration cost is reasonableProtect personal privacyUser identity/authority verificationApplication serverCiphertext
The invention discloses an agent-based single sign on (SSO) method and system, belonging to the technical field of computer information. In the method, a user (U) registers and acquires a user certificate (C) in an application server (S); the U logs in an SSO server (L) and sends a certificate setting request; the L stores user identifications, application server identifications and ciphertext (C') in an associated manner; the U logs in the L and requests to access the S; the L is interacted with the S to acquire a token issued by the S and a signature (sig) of the S for the token; the L usesa self-private key to sign the token to acquire sig' and then searches the C' associated with the U identifications and the S identifications as well as sends the C', the token and the sig' to the U;the U uses a private key in the user C to decrypt c' so as to acquire C, and sends SSO server identifications, the C, the token and the sig' to the S; and the S verifies the token and the sig', if the token and the sig' pass the verification, the user C is continued to be verified; and if the user C passes the verification, the U is permitted to log in. The invention also discloses an SSO system corresponding to the SSO method.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
A multi-confirmation security operation method for identity recognition and mobile positioning based on the Internet of Things
ActiveCN105632002BDon't worry about leakingGet rid of the password operation methodIndividual entry/exit registersTransmissionUser needsPassword
The invention relates to a multiple determination safety mechanism with identity recognition and movable location based on Internet of Things. The safety mechanism is characterized by comprising the following steps: S10, a mobile terminal APP sends address information to a WEB terminal in real time after networking, a user logs in a user account at the mobile terminal APP, wherein the log-in is successful after passing verification at the WEB terminal, and the user clicks an unlocking task sent to the mobile terminal APP by the WEB terminal before, and applies to acquire an unlocking code by verifying personal passwords at the WEB terminal; S20, the WEB terminal verifies the address information received at the last step after receiving the unlocking code application, and continues to verify the received personal password after comparing the address information received at the last step with stored address information corresponding to the unlocking task and determining the address information is correct, and after the received personal password passes verification, the WEB terminal sends an unlocking private key to the mobile terminal APP; and S30, the unlocking private key is input to a dynamic code lock of an ATM, wherein if the unlocking private key is correct, the unlocking is successful, and if the unlocking private key is wrong, the user needs to go back to S10.
Owner:上海杰盛立业网络科技有限公司
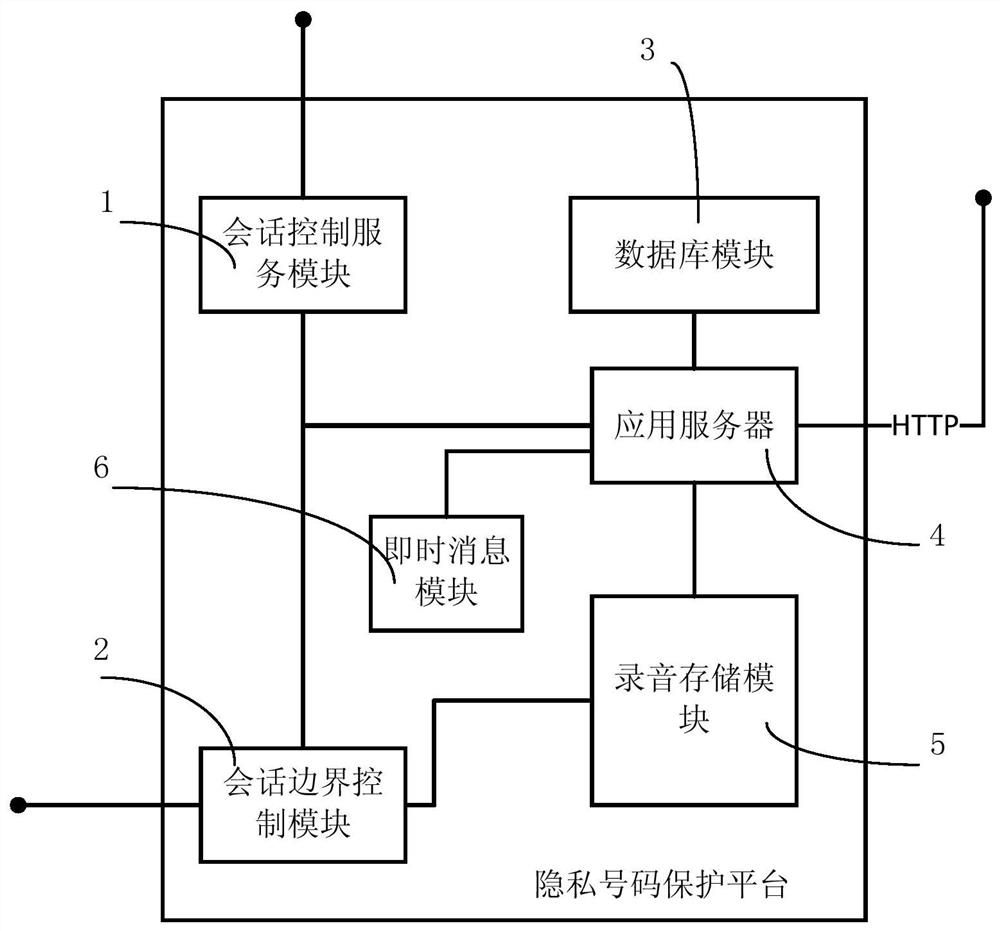
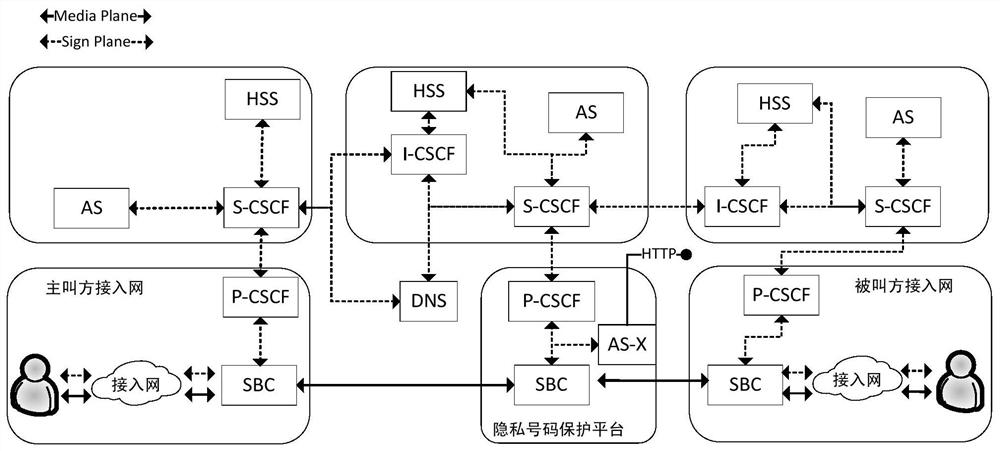
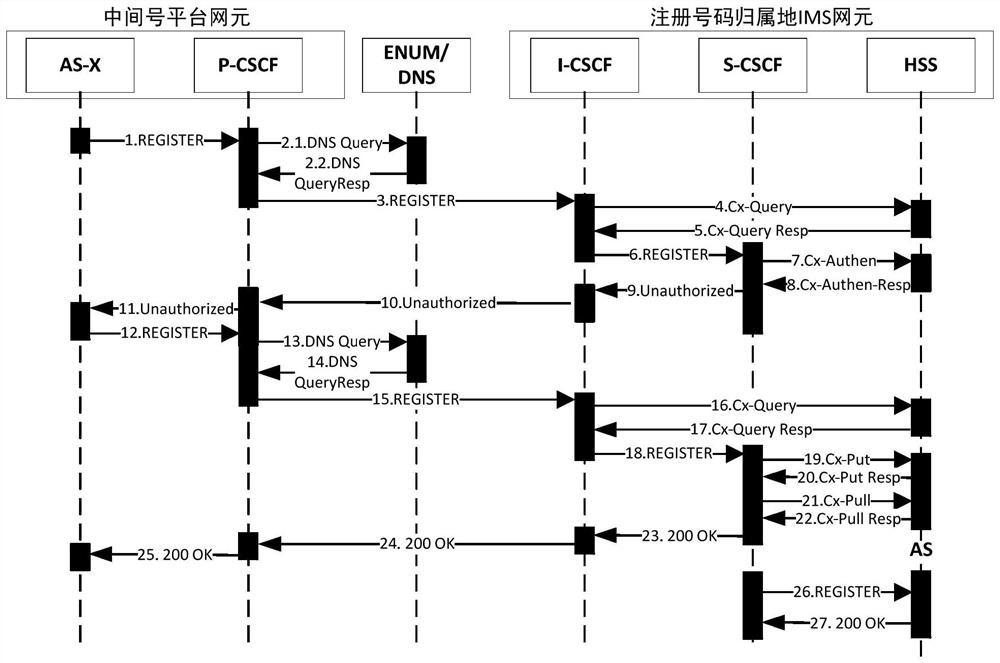
A mobile phone security privacy number protection platform based on IMS networking
ActiveCN108521404BAchieve protectionEasy to useSpecial service for subscribersMessaging/mailboxes/announcementsThird partyApplication server
Owner:中国东盟信息港股份有限公司
Method for authenticating user identity through P2P service request
InactiveCN101697540BSituations that prevent loginDon't worry about leakingTransmissionUser inputPassword
Owner:ZHEJIANG UNIV
Method for protecting cipher of USB interface
ActiveCN101533452BDon't worry about leakingEasy to useInternal/peripheral component protectionDigital data authenticationFiltrationUSB
The invention discloses a method for protecting a cipher of a USB interface, which is to set a layer of USB filtration drive in an operation system, and set a protection cipher for the USB interface. The method comprises the following steps that: 1) the USB filter drive is used to determine that whether equipment accessing to the USB interface is storage equipment or not; 2) when the accessing equipment is the storage equipment, a user is required to input a cipher, if the cipher is matched with the set protection cipher, the operation system loads drive of the equipment for the user, if not,the drive of the equipment is not loaded; if the accessing equipment is non-storage equipment, the operation system directly loads the drive of the equipment for the user. Type of the USB equipment can be identified by the method, so that the storage type USB equipment can be used through the cipher, the user can conveniently use the storage type equipment without worrying about leakage of classified document in a computer.
Owner:宏电脑上海
A certificate making machine
ActiveCN106865290BDon't worry about leakingImprove efficiencyOverturning articlesArticle feedersPulp and paper industryAccreditation
The invention discloses a certificate making machine which comprises a printer, a conveyor belt, a turnover mechanism, a taking and putting mechanism and an assembling mechanism, wherein a turnover plate is cooperated with the conveyor belt to turn over certificate paper by 180 degrees; the taking and putting mechanism is arranged above the printer and the conveyor belt and travels to and fro between the printer and the conveyor belt to transfer the certificate paper; the assembling mechanism comprises a vacuum platform and a second vacuum sucking disc; the vacuum platform adsorbs the lower page of a protective film; and the second vacuum sucking disc adsorbs the upper page of the protective film. The certificate making machine adopts the second vacuum sucking disc to replace manual taking and putting of the certificate paper, turns over the certificate paper through the turnover plate and conveys the certificate paper through the conveyor belt, the protective film skillfully forms a V shape during film covering to facilitate insertion of the certificate paper; and the entire process is full-automatic, the efficiency is high, and high safety and reliability are realized without worrying about leakage of personal information.
Owner:珠海市技嘉科技有限公司
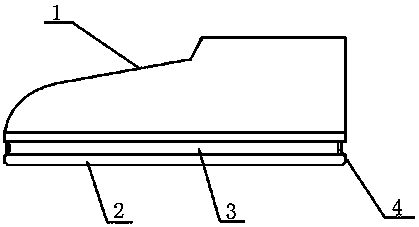
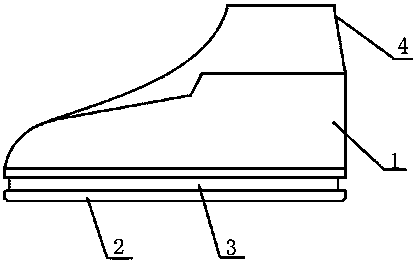
Integrated waterproof shoes
The one-piece waterproof shoe includes a vamp and a sole. The sole is provided with a circle of grooves; the waterproof part is fixedly placed in the groove; the waterproof part is made of elastic waterproof material. The invention has simple structure, reasonable design and convenient use. The waterproof part is set in the groove of the sole, and there is no need to store the waterproof part when going out, and it is not affected by the weather and environment during use, and the design is simple and easy to operate. The waterproof part is made of elastic material, which is in good contact with the upper part and tightly wrapped, so there is no need to worry about water leakage.
Owner:HUBEI UNIV OF ARTS & SCI
Pneumatic temporary support device for fully mechanized excavation
The invention discloses a pneumatic temporary support device for fully-mechanized excavating. The pneumatic temporary support device comprises a support platform, a cantilever and a bottom rack used for being hung on a rail, wherein one end of the cantilever is hinged to the bottom rack, and the other end of the cantilever is connected to the support platform; a first support air cylinder is connected to the lower portion of the support platform, and the push rod of the first support air cylinder extends out downwardly to support the ground; one end of the cylinder barrel of a second support air cylinder is hinged to the bottom rack, and the push rod of the second support air cylinder is hinged to the lower portion of the cantilever. The pneumatic temporary support device has the advantages that the support device can be hung on the rail and moved to an appointed support operation position to perform support operation, and the support device is unaffected by tunnel terrain.
Owner:北京双泰气动设备有限公司 +2
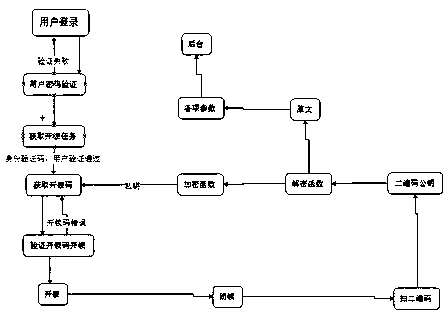
A three-party cross-certification security mechanism for ATM operation and maintenance management
ActiveCN105844755BDon't worry about leakingComplete banking machinesATM softwaresPasswordMaintenance management
The invention relates to a three-party cross-certification security mechanism used for ATM operation and maintenance management. The security mechanism is characterized by including the following steps: S10, logging in a user account at mobile terminal APP by a user, logging in successfully after verifying successfully by an online WEB terminal, clicking an unlocking task by the user wherein the unlocking task is sent to the mobile terminal APP by the WEB terminal, performing verification with the WEB terminal by using an individual password to applying for obtaining an unlocking code, and obtaining the unlocking private key of the unlocking task sent by the WEB terminal online after passing the validation successfully; S20, inputting the unlocking private key to the dynamic coded lock of ATM, unlocking successfully if the private key is correct, and returning the step S10 if the private key is wrong; and S30, adding cash after unlocking, pressing the dynamic coded lock key to lock ATM after adding cash, and calculating and compiling the information of the dynamic coded lock to be a 2D code by the embedded code in the dynamic coded lock after locking ATM.
Owner:上海杰盛立业网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com