A method, system, device and storage medium for isolating user identity information
A technology for user identity information and users, which is applied in the field of isolating user identity information, and can solve problems such as inability to prevent privacy leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
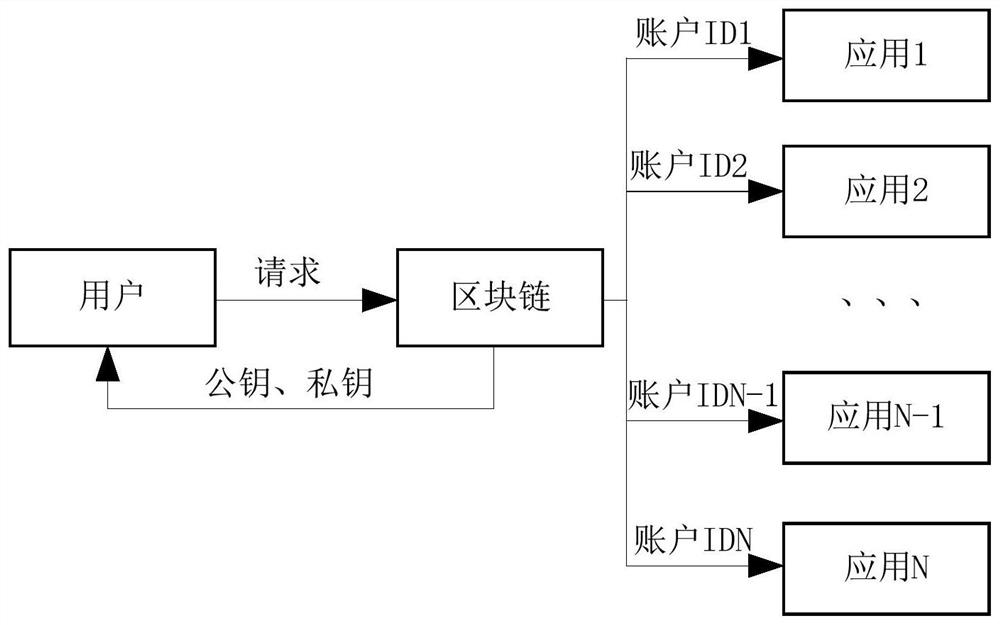
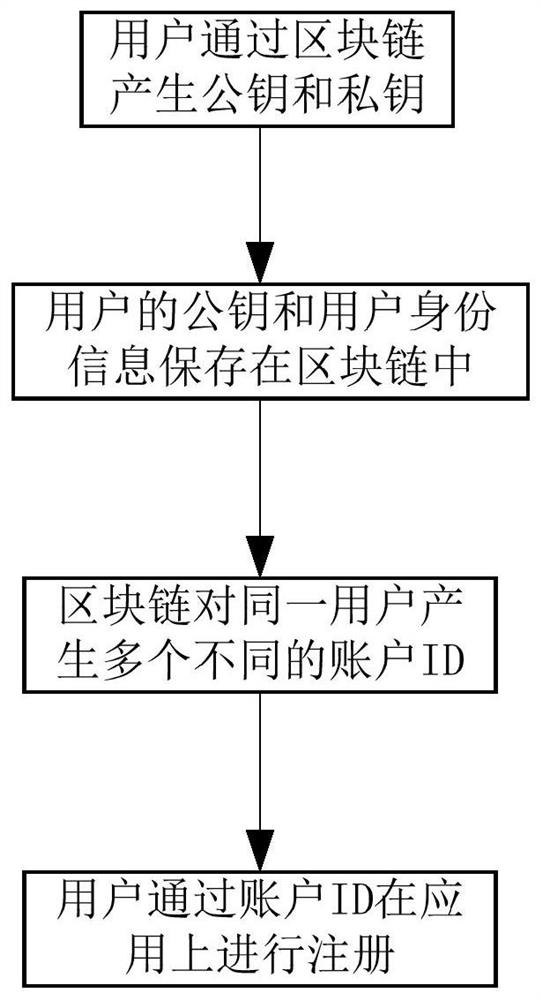
[0051] Such as figure 2 , 3 As shown, a method for isolating user identity information includes the following steps:
[0052] S1. The user generates a public key and a private key through the blockchain;
[0053] There are two ways to generate the public key and private key. One is to randomly generate the public key and private key through the blockchain. Once the private key is lost, it cannot be retrieved. (name, gender, ID number, mobile phone number, email address, voice, facial image, fingerprint, home address, place of household registration and other personal user identity information, or the name of the enterprise, organization, institution or unit, unified social credit code, address, Collective identity information such as tax number) is encrypted by Hash to generate a private key and a public key. If the private key is lost, it can be retrieved from the blockchain operator.
[0054] S2. The user's public key and user identity information are stored in the block...
Embodiment 2
[0063] A method for isolating user identity information is further improved on the basis of Embodiment 1, comprising the following steps:
[0064] S1. The user randomly generates the public key and private key through the blockchain, such as Figure 7 shown;
[0065] S2. The user's public key and user identity information are stored in the blockchain; in the blockchain, private chains and consortium chains are licensed chains, and each node participating in the blockchain system is licensed. Approved nodes cannot be connected to the system. However, if a limited number of multiple authentication nodes in the licensed chain are combined, it will also pose a certain threat to the leakage of user identity information. Therefore, if the blockchain is a licensed chain, after the user's public key and user identity information are Hash encrypted, Upload to the block chain; if the block chain is a public chain, user identity information can be selectively encrypted by Hash. Such a...
Embodiment 3
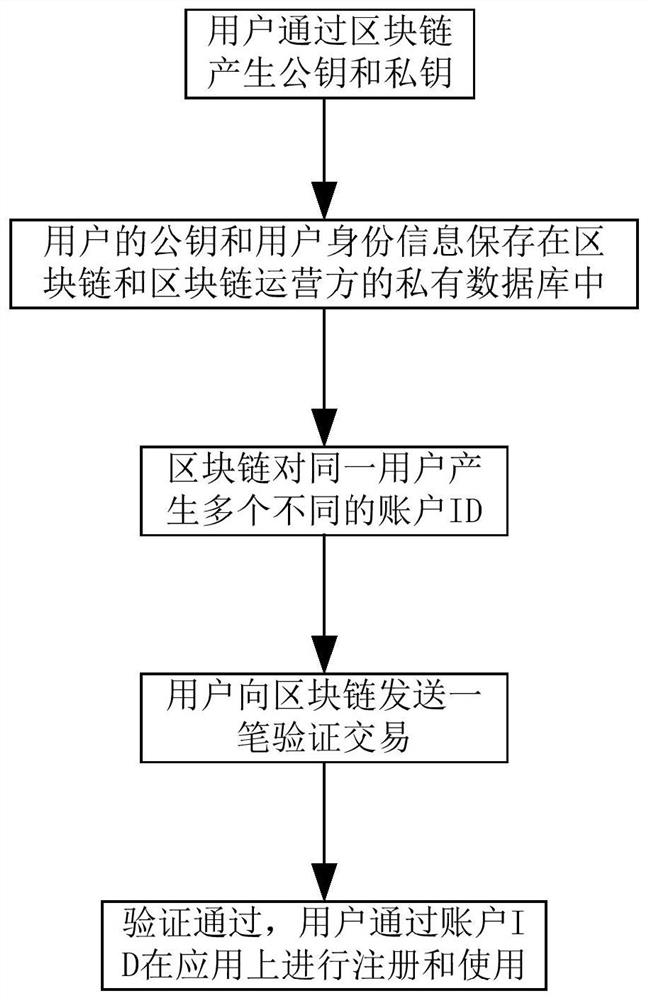
[0069] A method for isolating user identity information is further improved on the basis of embodiments 1 and 2, comprising the following steps:
[0070] S1. The user generates a private key and a public key through the blockchain operator based on the user's identity information, such as Figure 9 shown.
[0071] If the blockchain is a permissioned chain, the user's public key and user identity information are Hash-encrypted, and then the private key and public key are generated; if the blockchain is a public chain, user identity information can be selectively Hash-encrypted. Among them, the user identity information includes ID number, mobile phone number, mailbox, voice, facial image, fingerprint, home address, account location and other user identity information. If the private key is lost, it can be retrieved from the blockchain operator.
[0072] S2. The user's public key and user identity information are stored in the blockchain; in the blockchain, private chains and c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com