Method for authenticating user identity through P2P service request
A technology for user identity authentication and service request, which is applied to electrical components, transmission systems, etc., can solve problems such as storage and revocation troubles, and achieve a high safety factor
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
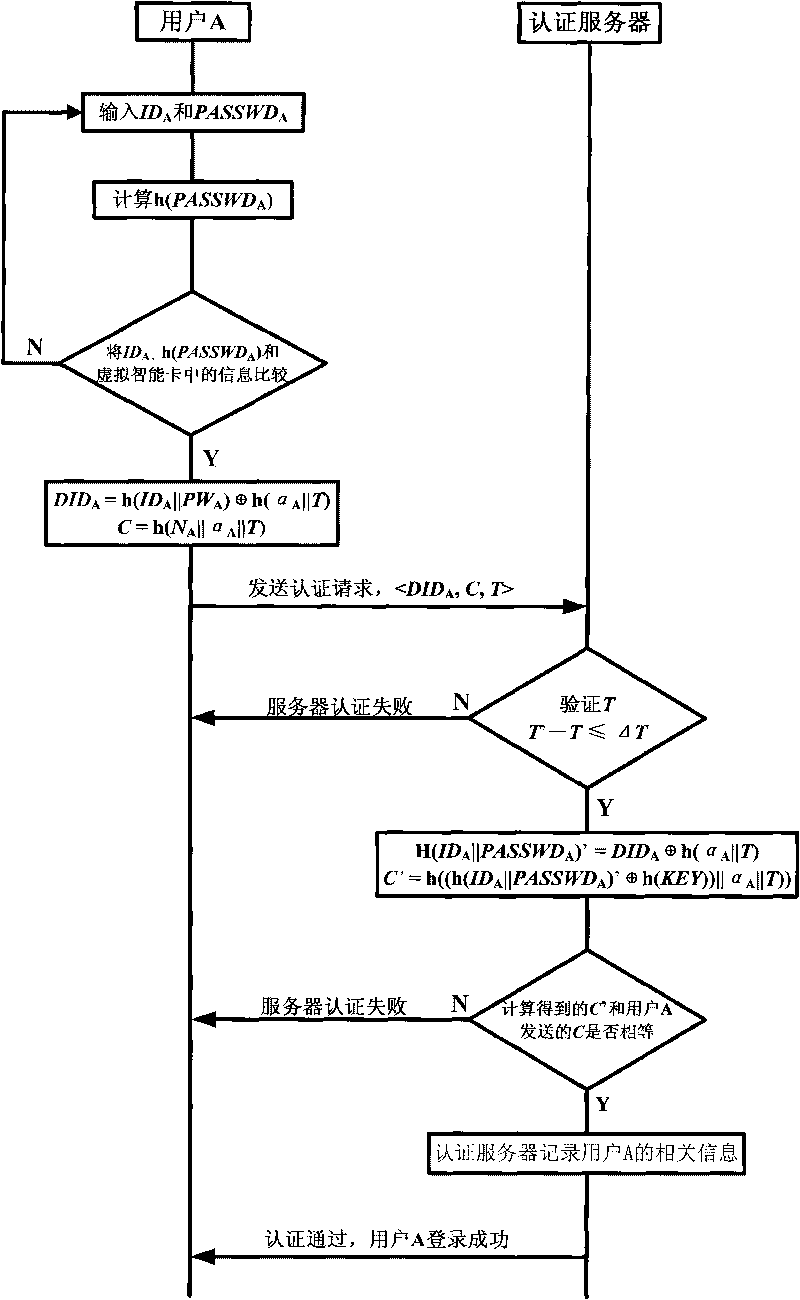
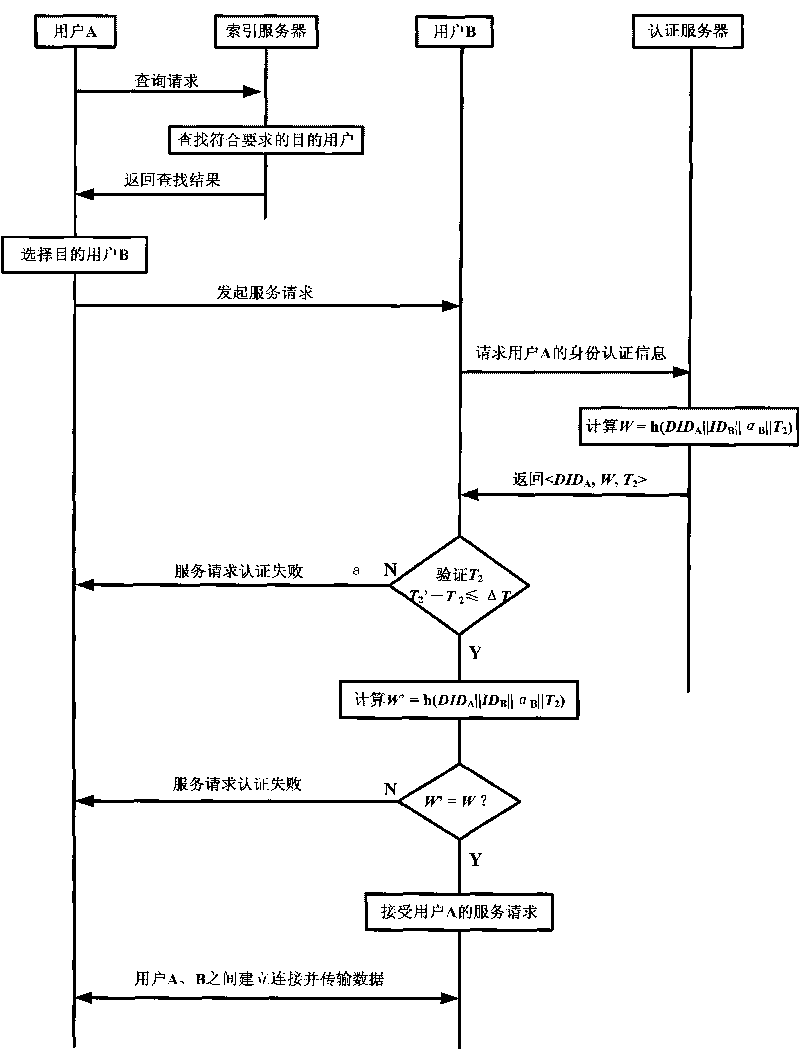
[0048] The specific implementation process of the P2P network authentication method proposed by the present invention will be further described below in conjunction with the accompanying drawings.
[0049] The framework of the entire P2P network is composed of registration server, authentication server, index server and common users in the Internet. The registration server is used to register new users, the authentication server is used to authenticate users, and the index server provides resource search services for users. The user finds the target user through the index server, and then establishes a connection with it and performs data transmission.
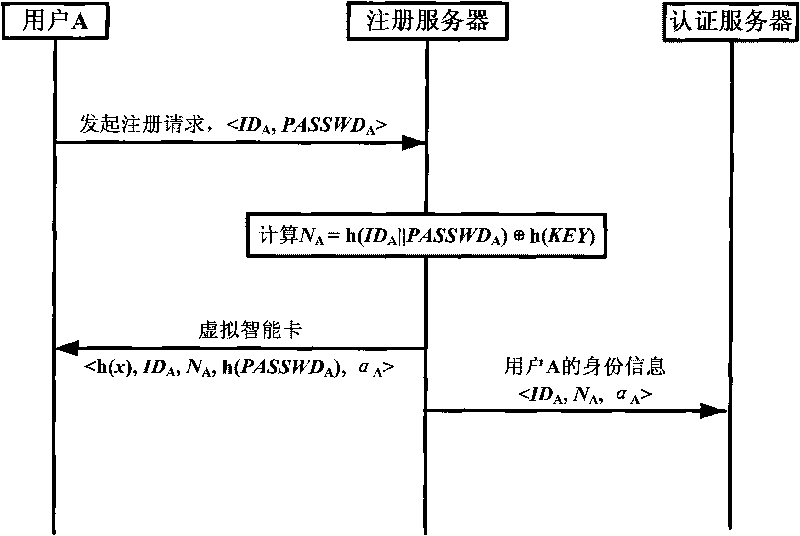
[0050] User registration: figure 1 The process of registering a new user with a registration server. Assuming that user A wants to join the P2P network and obtain services, he first needs to register with the registration server, including the following steps:
[0051] 1) User A submits his username (ID A ) and password (P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com