Web caching with security as a service
A security and caching technology, applied in the field of computer networks, which can solve problems such as the inability to implement security policies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
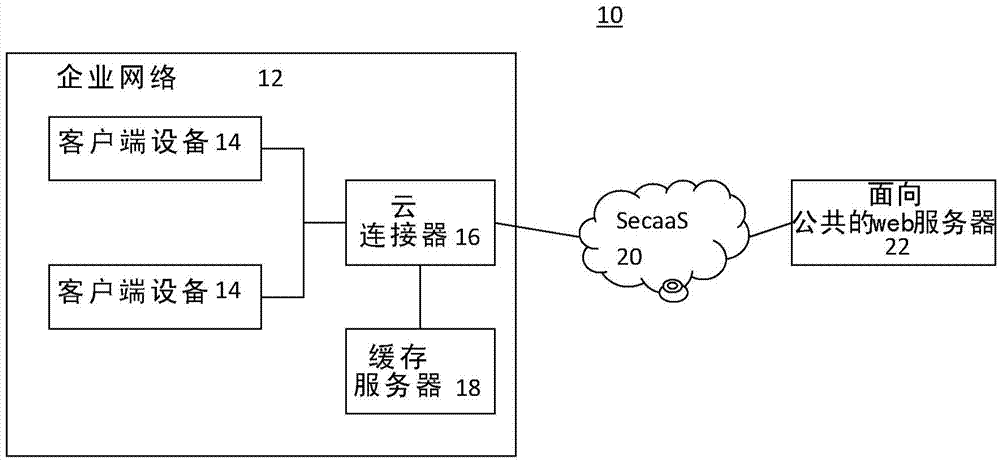
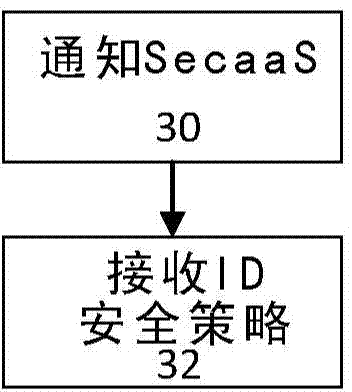
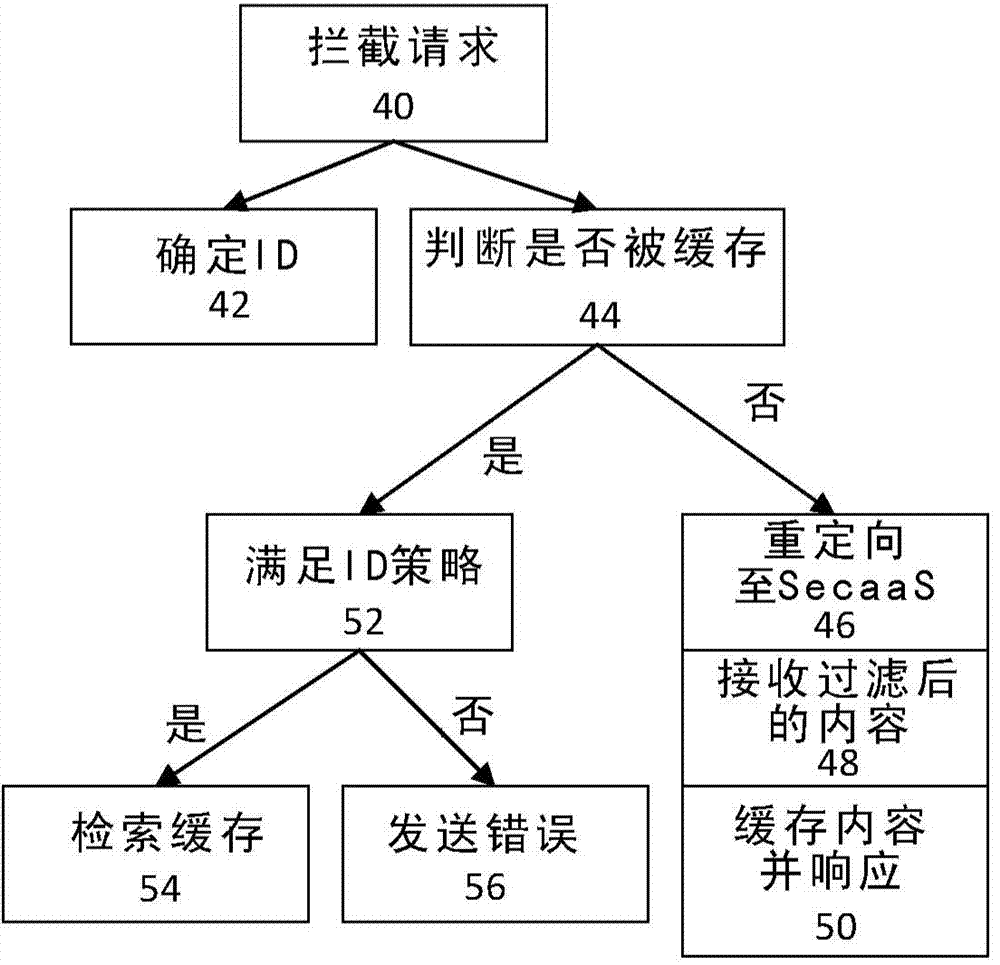
[0015] The cached content is filtered by SecaaS. However, the identity of the requester may change, so identity-based security is a security breach for cached content. When the content in the cache is not available, the cloud connector can fetch from the web cache or redirect the traffic to SecaaS. For security, Cloud Connector redirects HTTP traffic to SecaaS. It also collects user identities so that SecaaS can provide identity-based security on the cloud. This implies that the Cloud Connector is not aware of policies on the cloud. On the other hand, with the advent of web caching, cached content is obtained from a web cache rather than from a content server. Traffic is not redirected to SecaaS.
[0016] Combining web caching and SecaaS enables similar identity-based policies to be enforced both on SecaaS and on content delivered from web caching. Identity-based policy implementation outside the corporate network using SecaaS and within the network for web-cached content...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com