Digital media content protection method, device, server and terminal
A digital media and protection device technology, applied in the field of communication, can solve the problems of cumbersome analysis and processing, cumbersome operation process, cumbersome operation, etc., and achieve the effect of simple and clear data structure, good scalability, and improved operation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
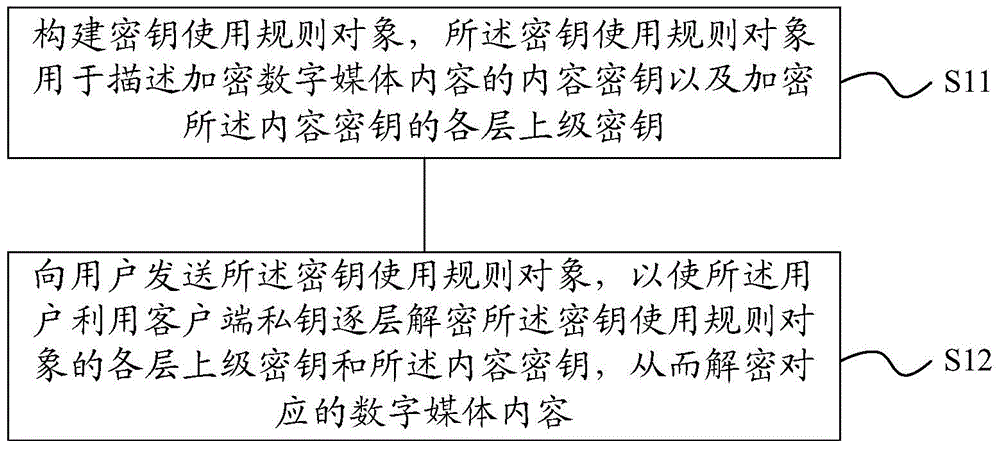
[0108] When a user requests to play a digital media content, the operator determines that the user has paid in the service system and allows the user to watch the content within 24 hours of the day. The protection of the digital media content is mainly realized through the following steps:
[0109] 1. The operator encrypts the content encryption key with the user's public key;
[0110] 2. According to the definition of the key use rules, the operator sets the start time and the deadline for the key to be used, and the time is 1 day;
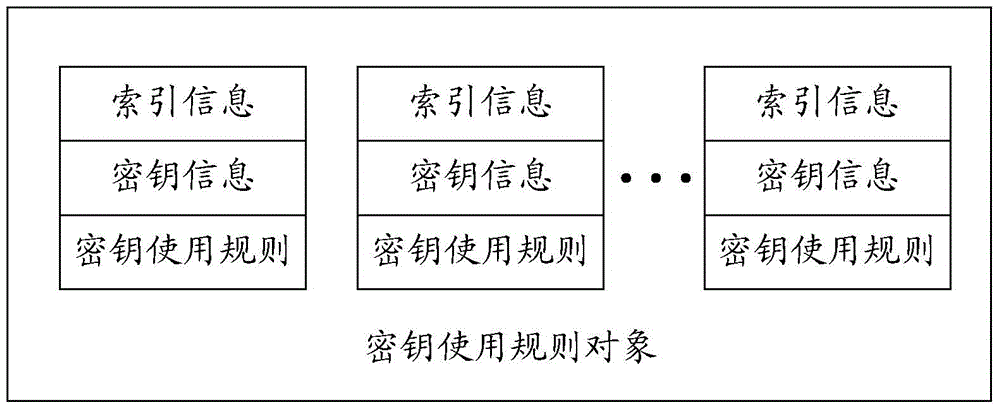
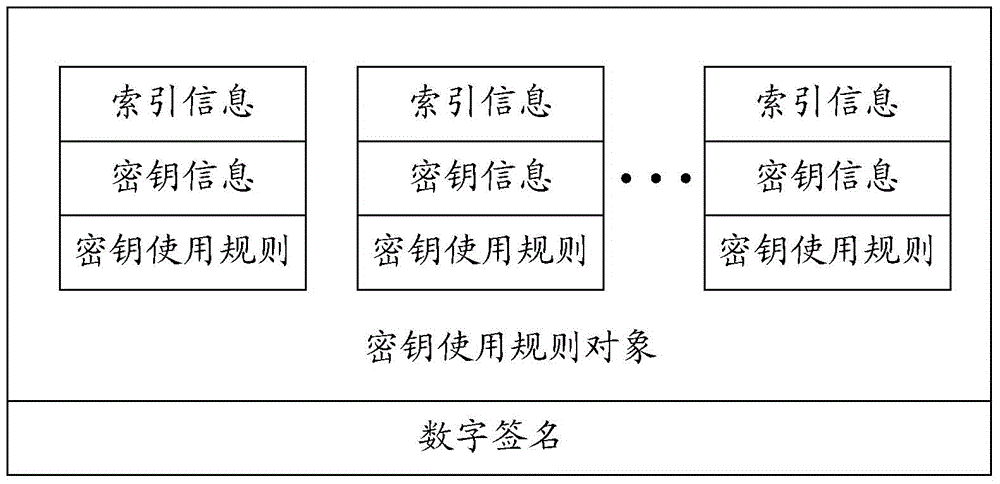
[0111] 3. The operator encapsulates the key usage rule and the encrypted content key into a key usage rule object according to the definition of the key usage rule object, and uses the operator's digital certificate to sign the key usage rule object to generate a signature The final key usage rule object is sent to the user;
[0112] 4. After receiving the key usage rule object, the user's terminal uses the operator's digital certificate to ver...
Embodiment 2
[0118] A user purchases a TV series service from an operator, and the TV series has 40 episodes, and the operator allows the user to watch the content within one month. The protection of the digital media content is mainly realized through the following steps:
[0119] 1. The operator encrypts the service key with the public key of the client device, sets the usage rule for the service key as one month, and encapsulates the encrypted service key and its usage rule into a key usage rule entity;
[0120] 2. The operator encrypts the content keys of 40 episodes of TV dramas with a business key, and encapsulates the encrypted content keys of 40 episodes of TV dramas and the key usage rules of each episode into 40 key usage rule entities;
[0121] 3. The operator encapsulates the above 41 key usage rule entities into a key usage rule object, which is digitally signed and sent to the user;
[0122] 4. After receiving the key usage rule object, the user terminal verifies the legalit...
Embodiment 3
[0129] There may be multiple devices in the user's home, and when there is a visitor, the visitor's device may also join the user's home network and use the digital media content purchased by the user.
[0130] For example, there are 2 devices in the user's family, and the monthly subscription period set by the operator to watch a certain content on the home network device is 1 month. Within 1 month, the user can watch the ordered content on 2 devices in the home; if a temporary visitor brings the device into the home, within the valid period of 1 month, the operator allows the visitor device to be available on 1 days to watch this family purchase. The protection of the digital media content is mainly realized through the following steps:
[0131] 1. The operator assigns a domain key to the user's home network, which is encrypted with the public keys of the user's two client devices, and limits the use rules of the key, that is, one month; encapsulation Use rule entities for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com