Semantics-based registration information security officer authentication capability evaluation method and system
A technology for registration information and information security, which is applied in the field of semantic-based registration information security personnel certification ability evaluation, can solve problems such as the inability to guarantee the level and ability of examinees in the test paper, and the inability to fully reflect the degree of mastery of the necessary knowledge for students' comprehensive application ability. , to reduce the memory burden, broaden the idea of the question, and reduce the search time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
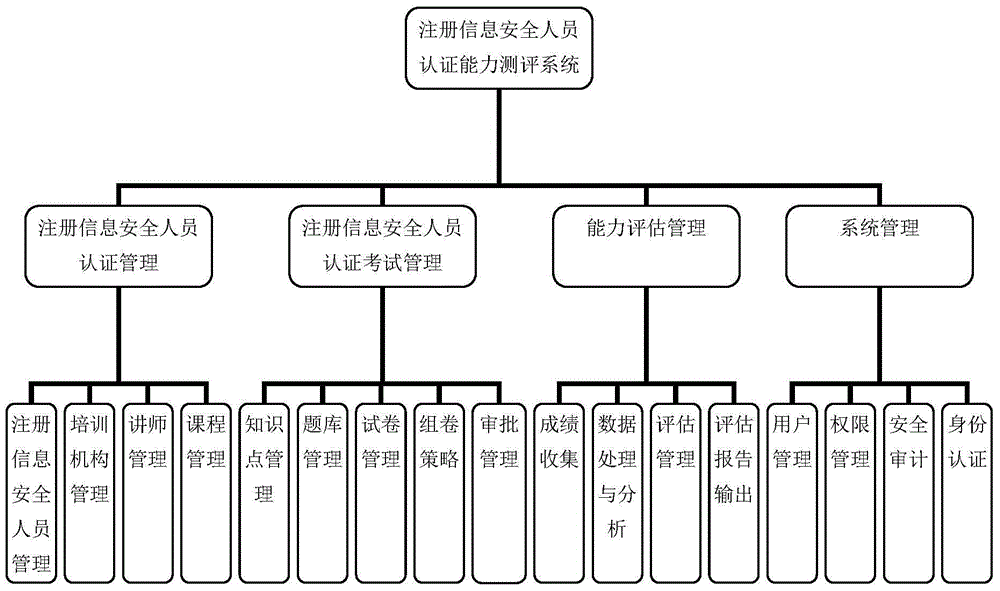
[0060] The specific implementation of the invention will be described below by taking Certified Information Security Professional (CISP for short) as an example.
[0061] The specific implementation process of the certification ability assessment method for registered information security personnel is as follows:
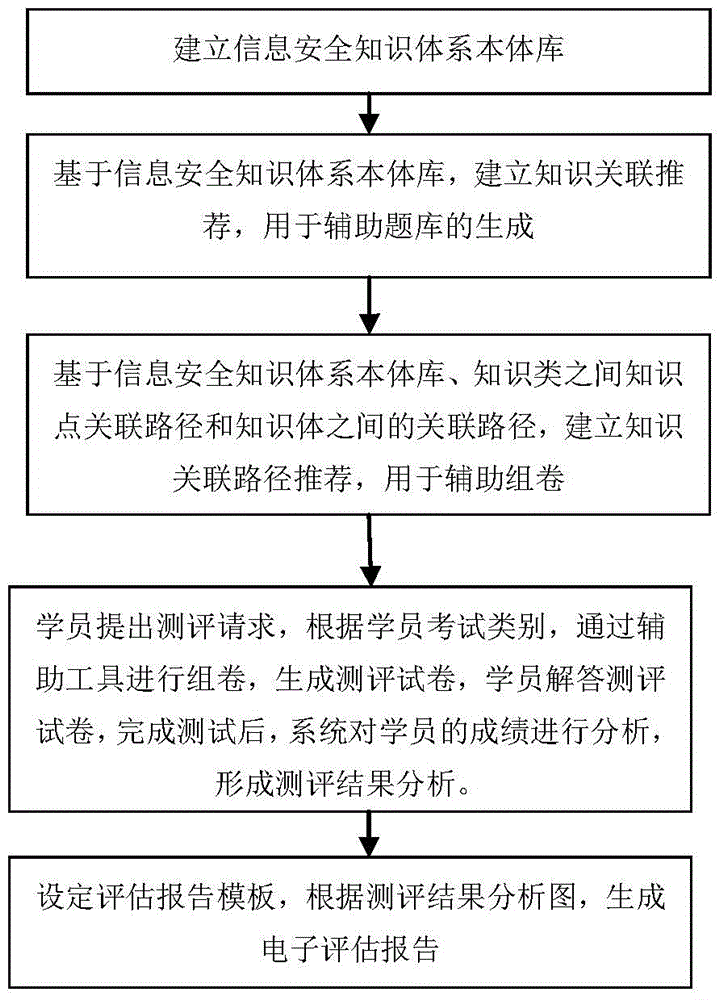
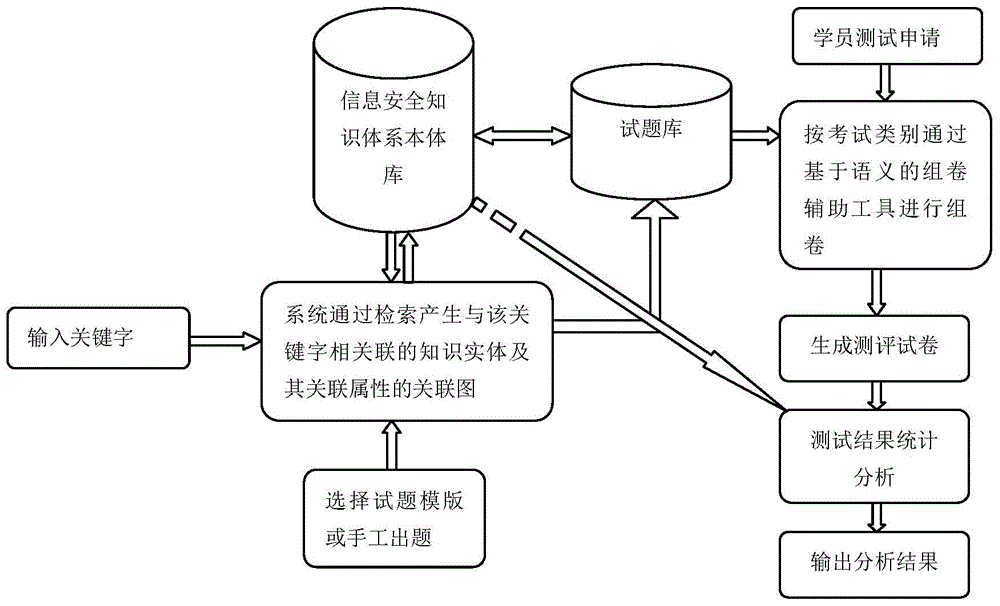
[0062] The first part: Establish the ontology database of information security knowledge system;
[0063] The CISP syllabus stipulates the content and depth requirements of each knowledge point in the knowledge sub-domain, and divides the ability level into three categories: "understanding", "understanding", and "mastery". Understanding: is the minimum depth requirement, students only need to correctly understand the basic concepts and principles of the knowledge points; understanding: is a medium-depth requirement, students need to understand the content in depth on the basis of correctly understanding the basic concepts and principles of the knowledge points, And...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com