Apparatus and methods for safety-critical applications
A security, device technology, applied in the field of devices and methods for safety-critical applications, capable of solving the problem of costly post-authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
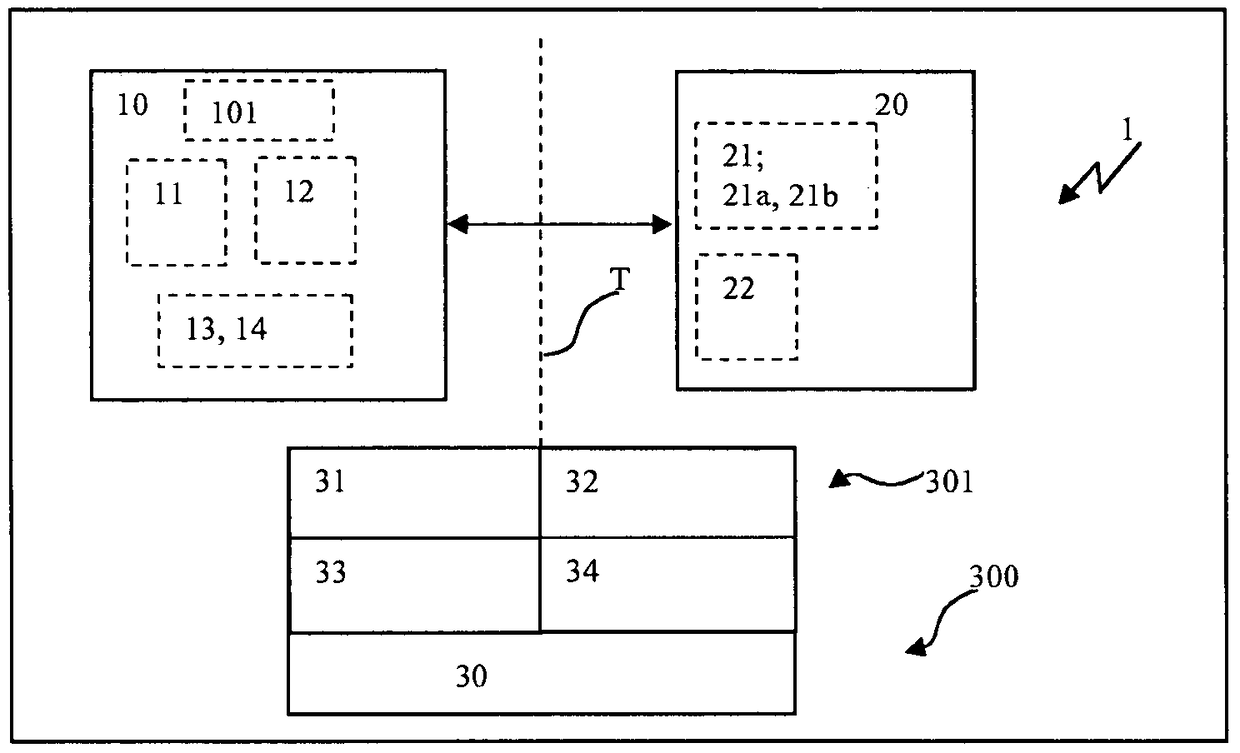
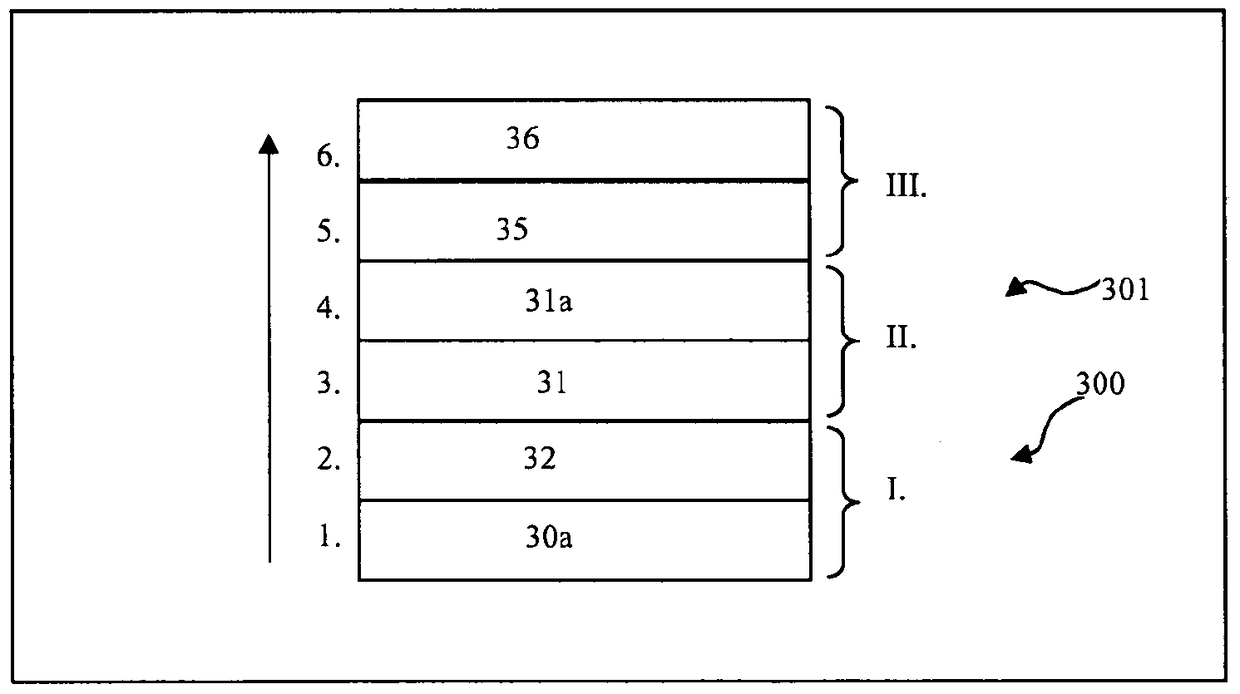
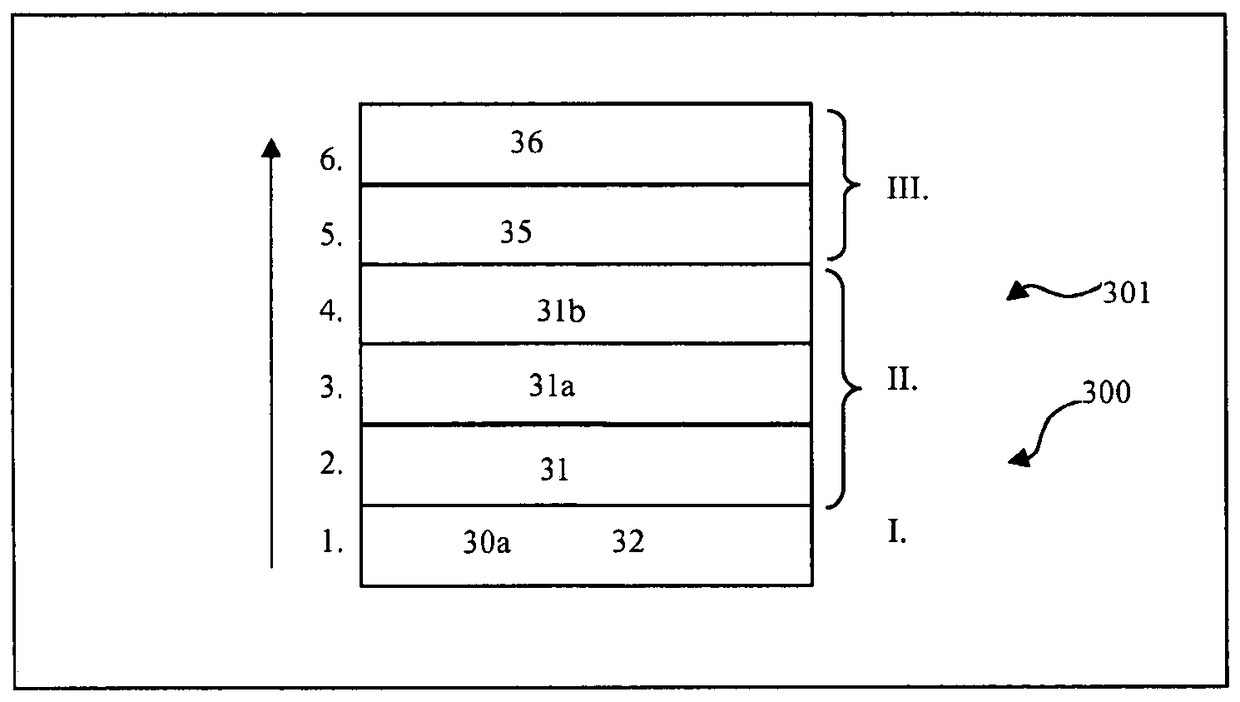
[0109] exist figure 1 A device 1 for safety-critical applications is shown in the figure, which has a central processing unit 10, the central processing instrument has a monitoring module 11 and / or a protection module 14, and the central processing unit is connected with a microcontroller 101 and a first storage module 12 communicates with the second storage module 13 or has these components. The central processing unit 10 communicates with a storage device 20 , which includes a data exchange device 21 and a storage area 22 . Furthermore, a hardware component 30 is shown, which is connected to a safe runtime system (LZS) 33 and a safe application program (AWP) 31 as well as a normal runtime system (LZS) 34 and a normal application program (AWP) 32 Or have these components. The illustrated configuration is part of a hardware architecture 300 or a runtime system architecture 301 . exist figure 1 Indicates the separation level T which extends between the normal LZS 34 or AWP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com