A method of detecting sha-1 algorithm against differential fault attack
A differential fault attack and algorithm technology, applied in the field of information security, can solve problems such as hidden dangers of cryptographic equipment security, and achieve the effect of simple, easy and accurate implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to make the present invention more comprehensible, a preferred embodiment is described in detail below with accompanying drawings.
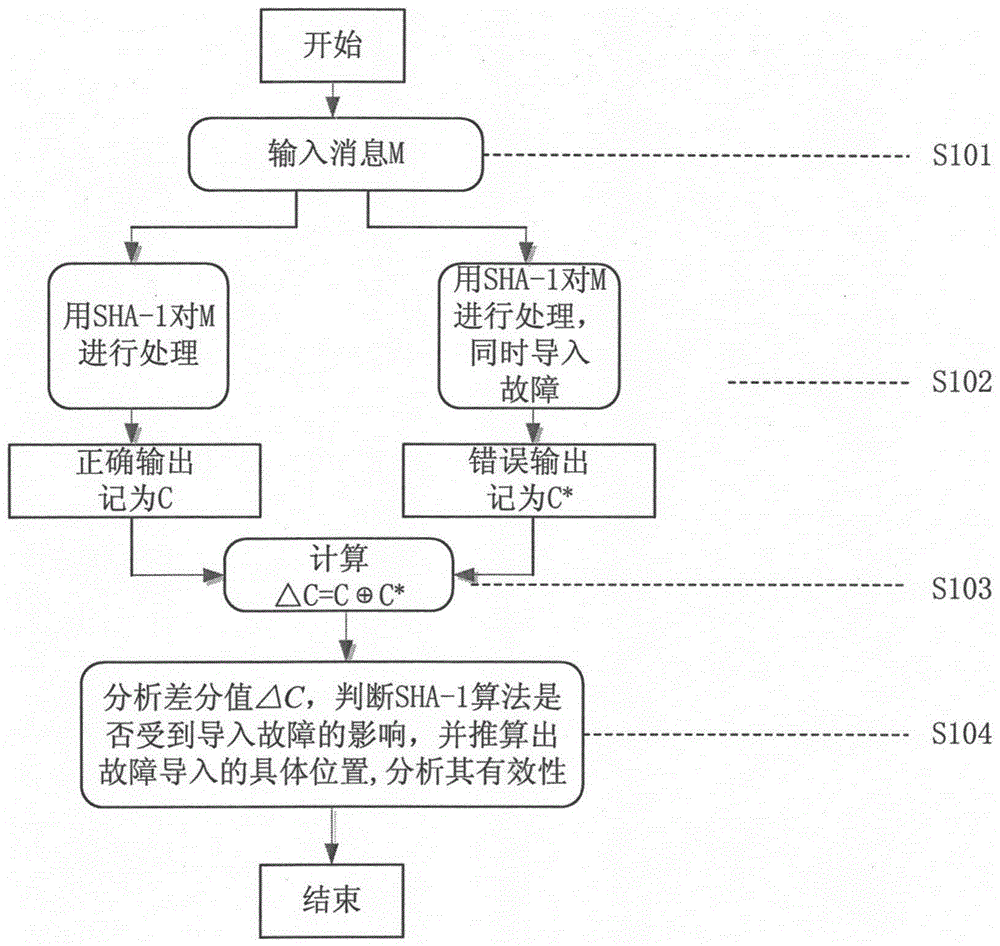
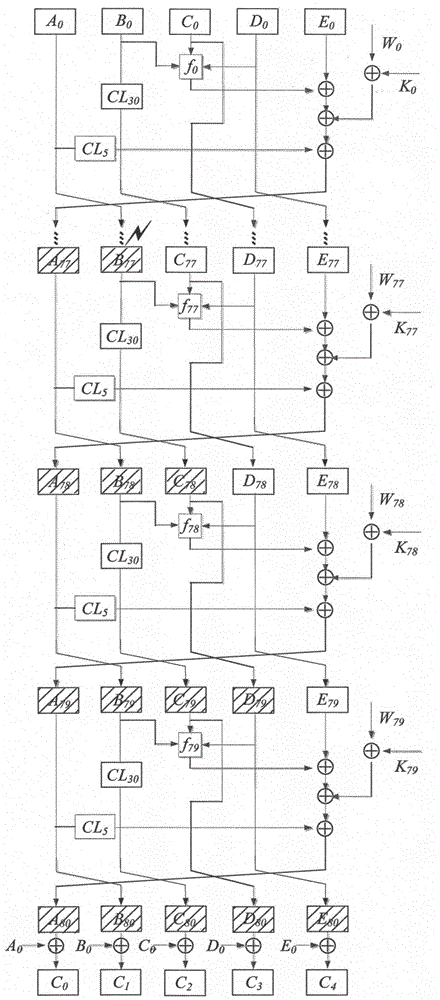
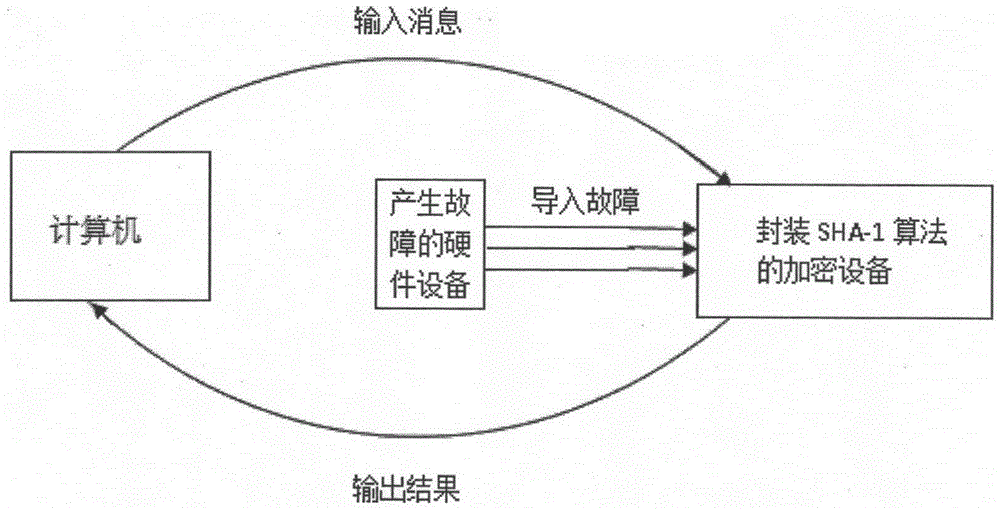
[0042] When using the SHA-1 algorithm to process the same message M, if the experimental execution environment is different, such as voltage, clock, temperature, radiation, light, and eddy current, the attacker can obtain the correct output under the same key K C and error output C * , by calculating the output difference value of these two values, namely Key information can be deduced. Attackers can induce faults during the operation of the processing equipment encapsulated with the SHA-1 algorithm, but they do not know the specific location of the fault and the specific error value, so the location of the fault at this stage becomes the key. To analyze the difference ΔC To obtain important information, the location where the fault is imported must be valid, otherwise, the fault imported this time will not affect the processin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com