Data identification method for two-dimension code safety verification
A security verification, two-dimensional code technology, applied in data processing applications, electronic digital data processing, computer security devices, etc., can solve problems affecting user experience, reducing user satisfaction, participation enthusiasm, database server paralysis, etc., to prevent The effect of brute force
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The specific technical content of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
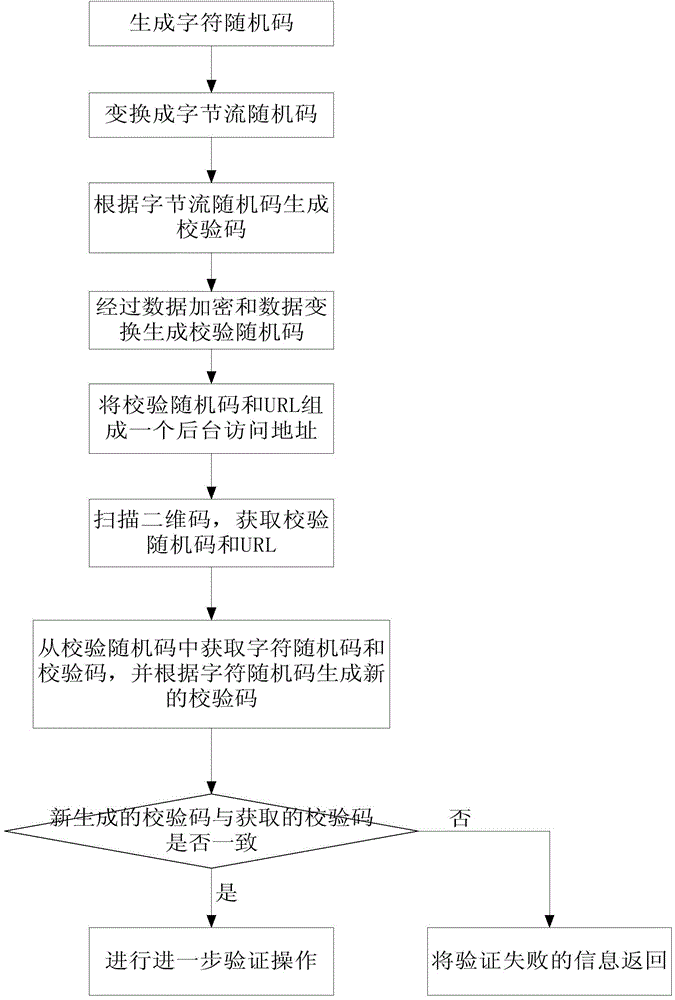
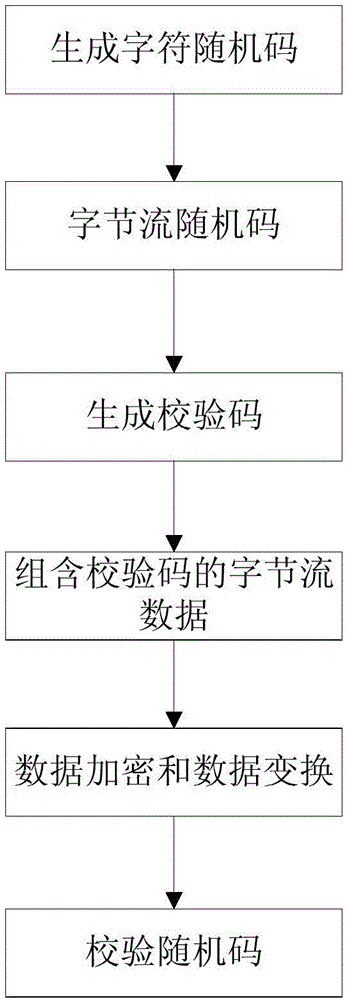
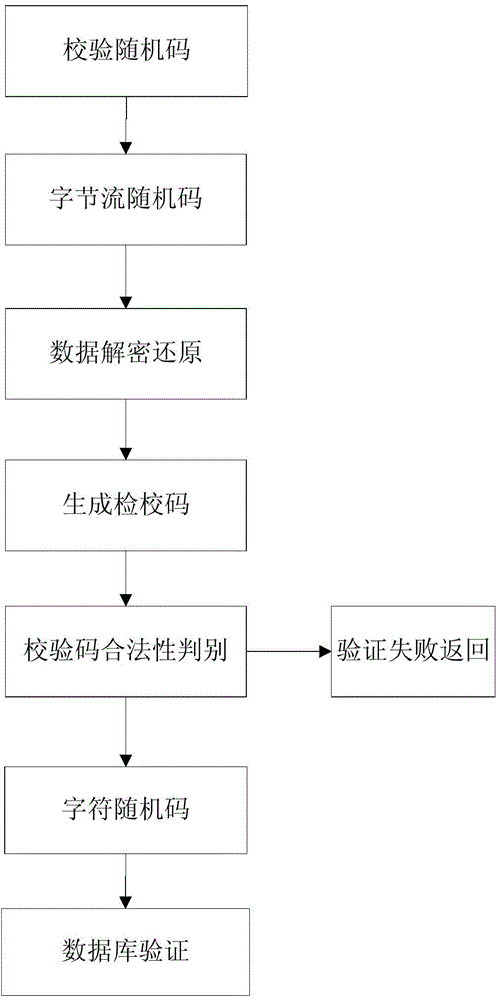
[0037] In order to prevent malicious cracking of random codes through programs, and simulation programs that cause a large number of database accesses, it is easy to paralyze the server. The invention provides a new method for authenticating data, that is, adopting a verification random code in a two-dimensional code. The so-called verification random code is to add a verification code to the random code. After the background server receives the verification random code, it analyzes whether the random code is legal through the verification code. Only the legal verification random code can access the database again. If it fails The random code verified by the check code is returned directly, thus effectively preventing brute force cracking and database paralysis caused by a large number of database acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com