Website malicious attack prevention method and system
A malicious attack, website technology, applied in transmission systems, electrical components, etc., can solve the problem of high operating costs, and achieve the effect of reducing marketing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
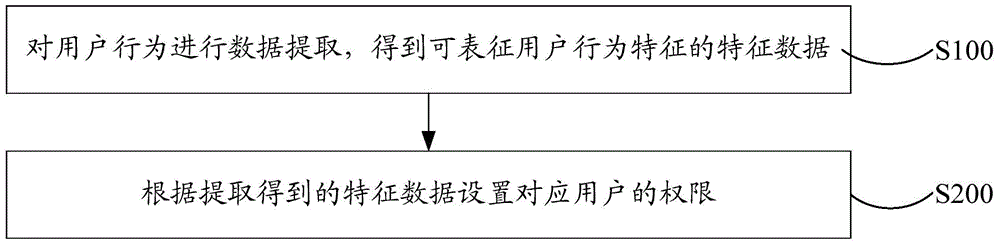
[0024] A method for preventing malicious website attacks, which can be applied to monitor and control abnormal account activities such as gift coupon lottery, fraudulent transaction identification, various market activities, large-value orders, and large-scale cash-on-delivery orders during the big promotion period. Such as figure 1 As shown, the website malicious attack prevention method includes the following steps:
[0025] Step S100: Extracting data from user behavior to obtain feature data that can characterize user behavior. By tracking user behavior for data statistics and extraction, feature data that can characterize user behavior characteristics are obtained.
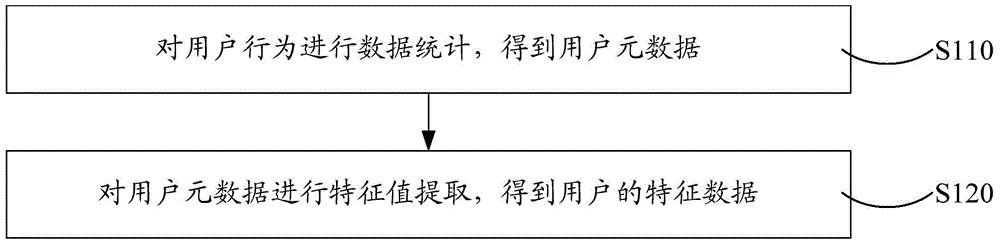
[0026] In one of the examples, as figure 2 As shown, step S100 includes step S110 and step S120.
[0027] Step S110: Perform data statistics on user behavior to obtain user metadata.
[0028] User behavior may specifically include at least one of the number of browsed product pages, whether an order has b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com