Multi-user encrypted search method in cloud storage
A search method and multi-user technology, applied in the field of cloud computing security, can solve problems such as system damage, and achieve the effect of dynamic management, data security protection, efficiency and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] This embodiment is designed to complete the initial generation and distribution of secret keys. The purpose of key distribution is: users have their own key material, and the trusted private cloud stores their own key and the user's auxiliary key. Expressed in a form:
[0037] step content 100 TPC initializes to generate key material 102 TPC makes the public key public and the corresponding secret key remains private
[0038] 104 TPC calculates user secret key and user auxiliary secret key 106 TPC sends the user secret key to the user and stores the user auxiliary secret key at the same time
[0039] The steps in Embodiment 1 are described as follows:
[0040] Step 100: TPC initialization generates key material. TPC creates a q-order cyclic group G according to the generator g; H is a secure hash function, f is a pseudo-random function f s (), s is its f s The secret key of (), h=g R ,in Defined as the set of {0...
Embodiment 2
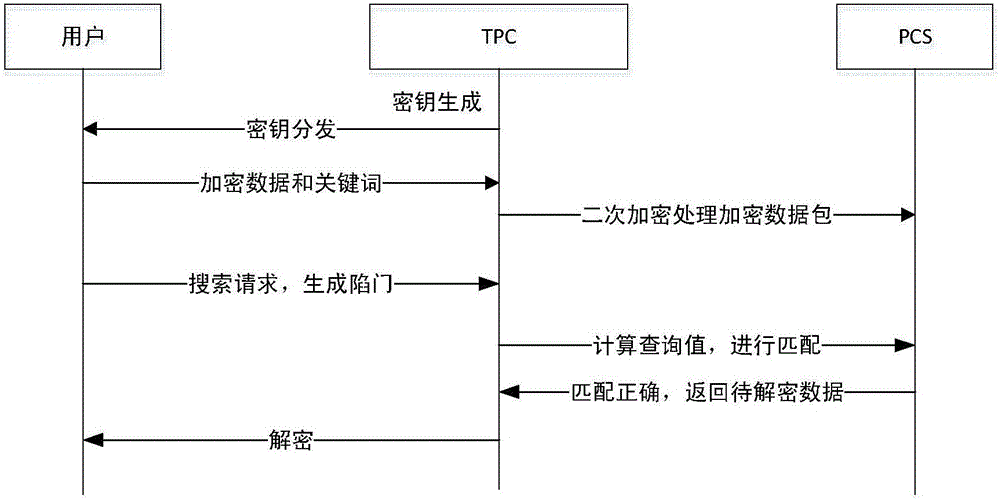
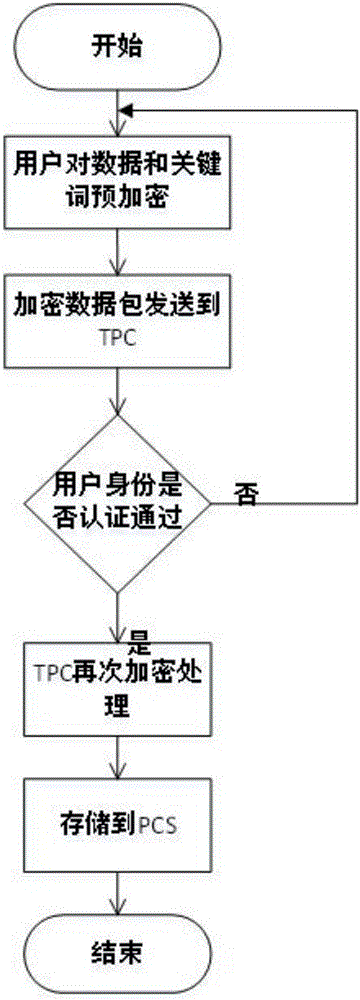
[0047] This embodiment is designed to complete the data upload stage. The purpose of this stage is to encrypt the data and keywords that users need to upload and store them on the public cloud. Data encryption upload is divided into user encryption and TPC encryption upload. Including but not limited to the following steps (expressed in a table):
[0048] step content 108 User U first needs to encrypt data and data keywords 110 The user sends the encrypted data and the keywords of the data to the TPC for processing 112 After the user passes the TPC authentication, the TPC will encrypt again 114 TPC uploads the encrypted data to the public cloud
[0049] The process of data upload stage is as follows: Down figure 2 shown.
[0050] The steps in Embodiment 2 are described as follows:
[0051] Step 108: the first user u encrypts the data d to be uploaded and the keywords of the data d.
[0052] The user uses the EIGamal encryp...
Embodiment 3
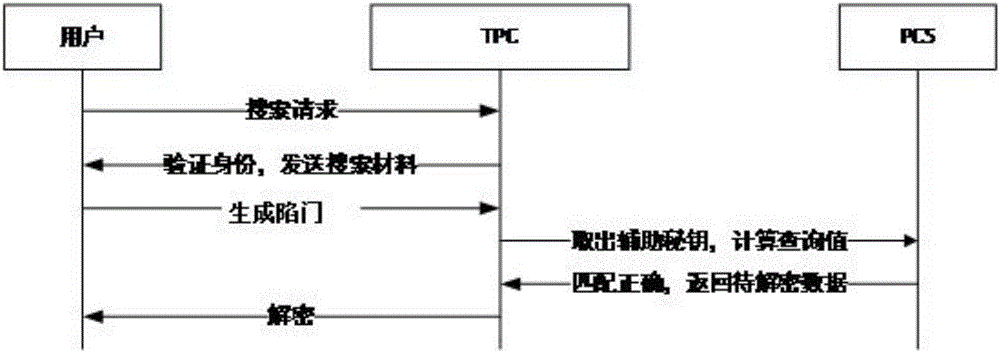
[0059] This embodiment is designed to complete the data search phase. The purpose of this stage is: the user submits a search request to the TPC, the TPC processes the search request, and sends the search trapdoor query value to the public cloud for search, and finally the TPC returns the data that the user is interested in. Including but not limited to the following steps (expressed in a table):
[0060] step content 116 The user submits a search request to the TPC, and the TPC then distributes the search materials after authenticating the user 118 User generates search trapdoor, sent to TPC 120 TPC takes out the user's auxiliary secret key and calculates the trapdoor query value 122 Match the trapdoor query value with the data item on the public cloud, and return the matched data to TPC 124 TPC first processes the retrieved data and sends it to the second user u 2 126 The user decrypts the data through the key material
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com