Multi-feature mobile terminal malicious software detecting method based on network flow and multi-feature mobile terminal malicious software detecting system based on network flow
A network traffic and malware technology, applied in the field of detecting malware network behavior, can solve the lack of mobile terminal malware network interaction behavior characteristics, lack of unknown malware capabilities, and lack of mobile terminal network traffic characteristics. Systematic summary detection method, etc. problems, to achieve the effect of meeting individual needs, improving accuracy, and improving the accuracy of detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] The present invention is described in detail below in conjunction with accompanying drawing:
[0076] A multi-feature mobile terminal malware detection method based on network traffic, combined with the embodiments, the specific working process is:
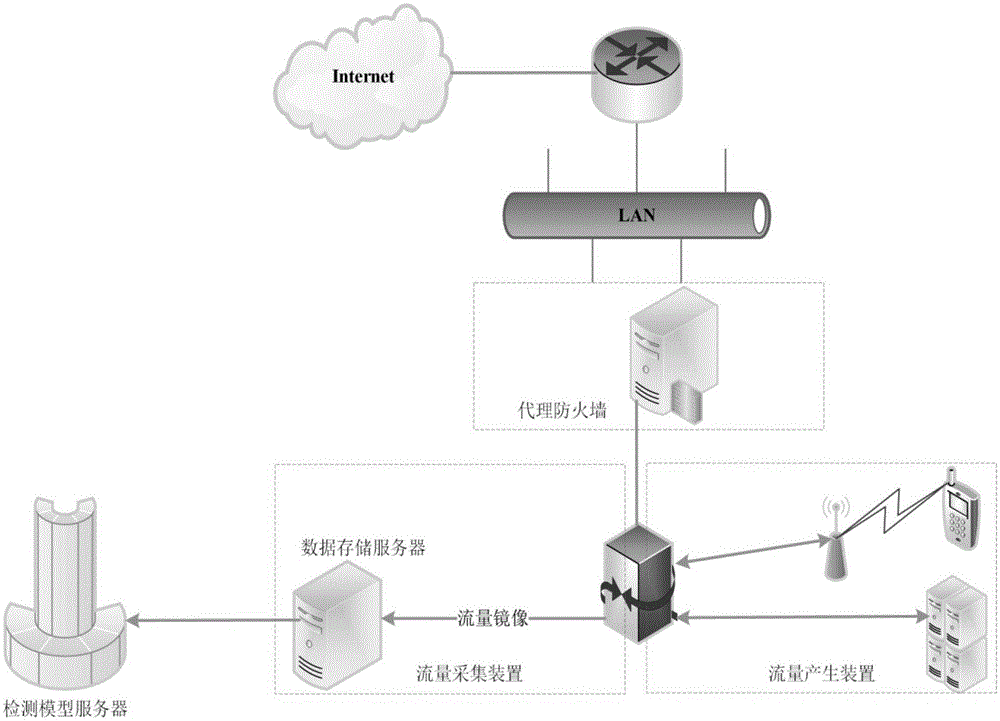
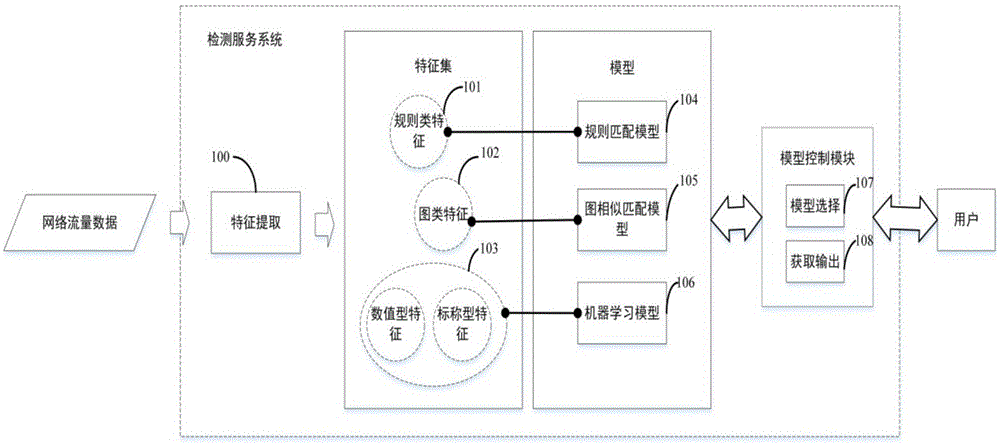
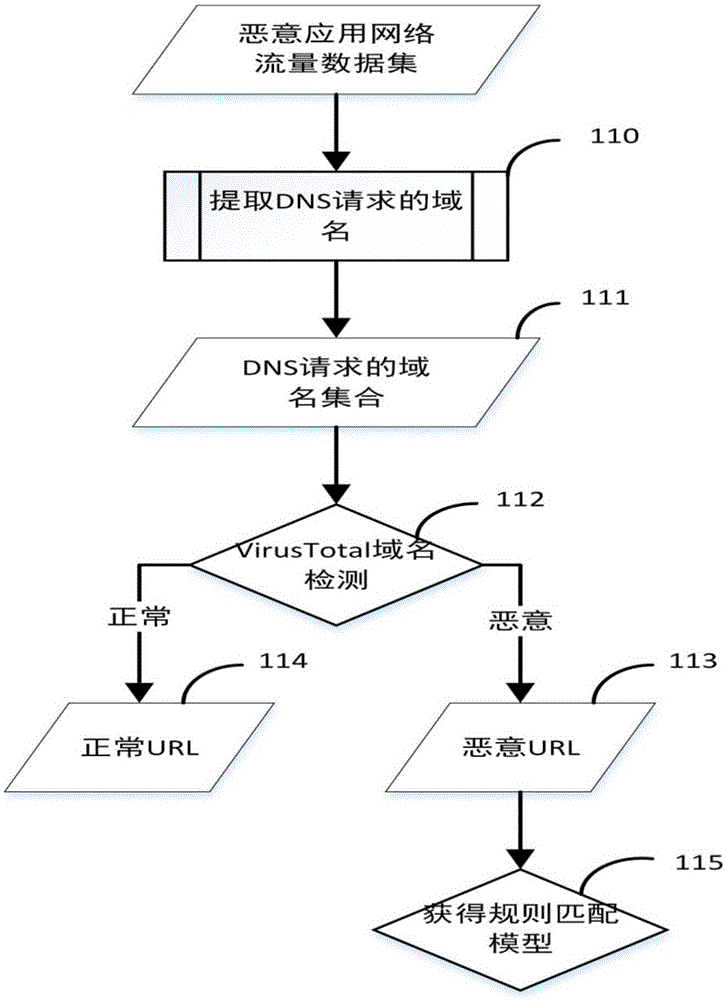
[0077] 1. Feature extraction and classification of features. First, according to the characteristics that can effectively characterize the network behavior of mobile terminal malware, design the corresponding feature extraction program to complete the feature extraction from the original network traffic data; secondly, classify the features according to different feature types. For example, for the domain name query of DNS requests, the ratio of traffic upload and download, connection duration, port number, behavior sequence diagram and other characteristics that can effectively characterize the behavior of mobile terminal malware, design corresponding feature extraction programs; then, for these features According to diff...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com