Full virtualization storage method based on consistency hash algorithm
A fully virtualized and consistent technology, applied in the field of storage servers, can solve the problems of system performance short board, read and write data speed and addressing time have not been greatly improved, to eliminate hot spots, realize dynamic resource allocation, The effect of improving the system IO response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] A fully virtualized storage method based on a consistent hash algorithm, the implementation steps of the storage method are as follows:
[0030] 1) Create storage resource pools and tiers:
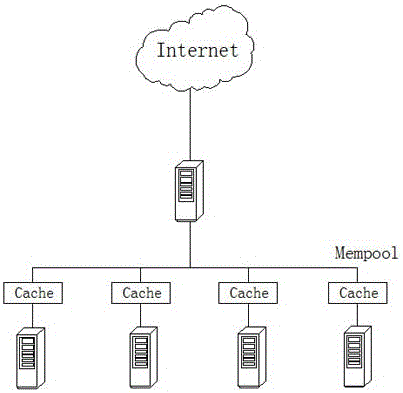
[0031] Such as figure 1 As shown, the storage server disk is automatically divided into blocks of the same size (for example, 1MB) by the storage software, and a storage resource pool (diskgroup) is created. The created storage resource pool is a unified storage space, and each small block Called a storage pellet;
[0032] This method of dispersing and recombining physical disks can shield the real situation of the underlying space, provide a unified storage perspective for the upper-layer software, and turn the storage space into a unified resource pool or super hard disk space. The resource pool is divided;
[0033] 2) Create a virtual LUN:
[0034] Each LUN is evenly assembled from the storage granules of each disk to the required space, providing a unified virtual storage space external...
Embodiment 2
[0039] On the basis of embodiment 1, when the space of the LUN described in this embodiment cannot meet the actual demand, the dynamic management of the LUN capacity is realized by increasing the number of storage particles in the LUN; compared with the traditional LUN method, the virtual LUN can Dynamically expand the number of disks to realize as much data as possible to be distributed to each disk, and improve the system IO response speed.
Embodiment 3
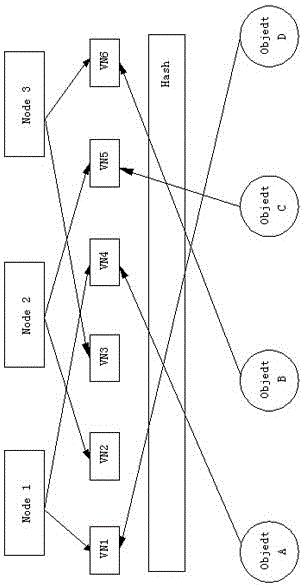
[0041] On the basis of embodiment 1, the SAN described in this embodiment implements LUN mapping through consistent Hash, and realizes automatic data migration at the bottom layer. The steps are as follows: figure 2 As shown, first put the hash value into a 2m ring space, and then calculate the corresponding key value of the data blocks ObjectA, B, C and D through the hash algorithm, and put the value into the hash space; finally A server is also regarded as an object to perform hash calculation and put it into the hash ring; through the above operation, the server node and data block are mapped in the same hash space, and then the data block is placed in the corresponding server node in a clockwise direction.
[0042] By virtualizing a number of virtual servers from each server and putting them into the hash space, then the physical node can obtain the virtual node through the algorithm, and map the virtual node to the hash space. The addition of virtual nodes can avoid a large ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com