Method and system for migrating business tunnel
A technology for migrating systems and services, applied in the field of communication, can solve problems such as service tunnel service interruption, achieve the effect of improving security and reducing the risk of service interruption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
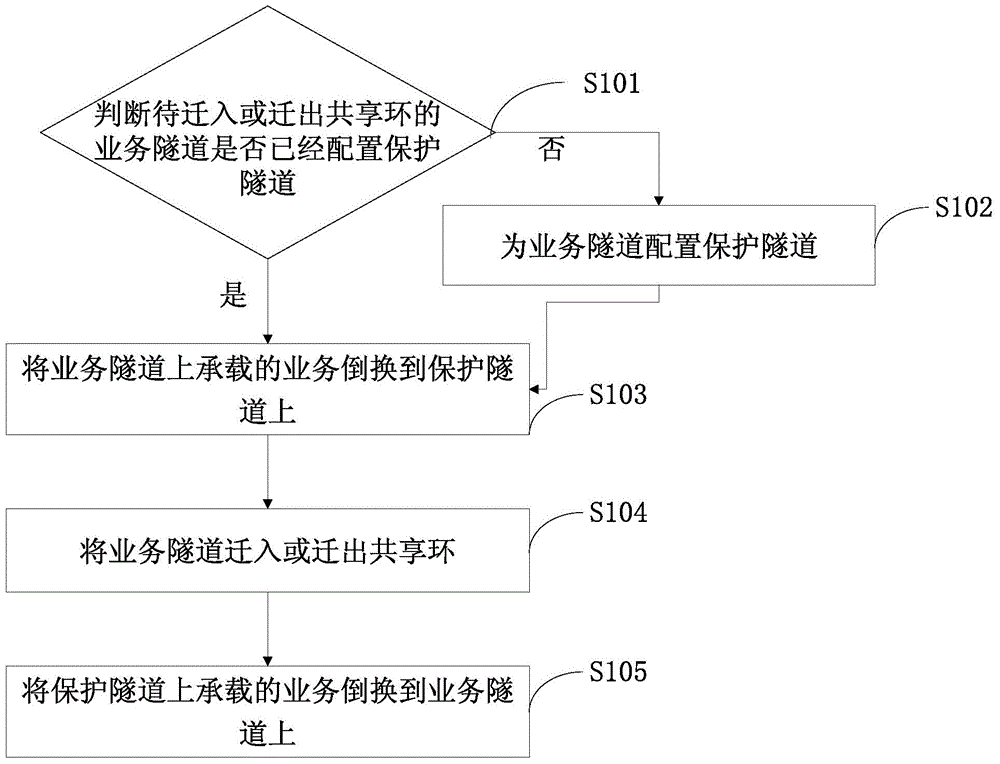
[0031] This embodiment provides a service tunnel migration method, please refer to figure 1 ,include:
[0032] Step S101: Determine whether the service tunnel to be migrated into or out of the shared ring has been configured with a protection tunnel, if not, execute step S102, and if yes, execute step S103.
[0033] Step S102: Configure a protection tunnel for the service tunnel.
[0034] Step S103: Switch the service carried on the service tunnel to the protection tunnel.
[0035] Step S104: Migrate the service tunnel into or out of the shared ring.
[0036] Step S105: Switch the service carried on the protection tunnel to the service tunnel.
Embodiment 2
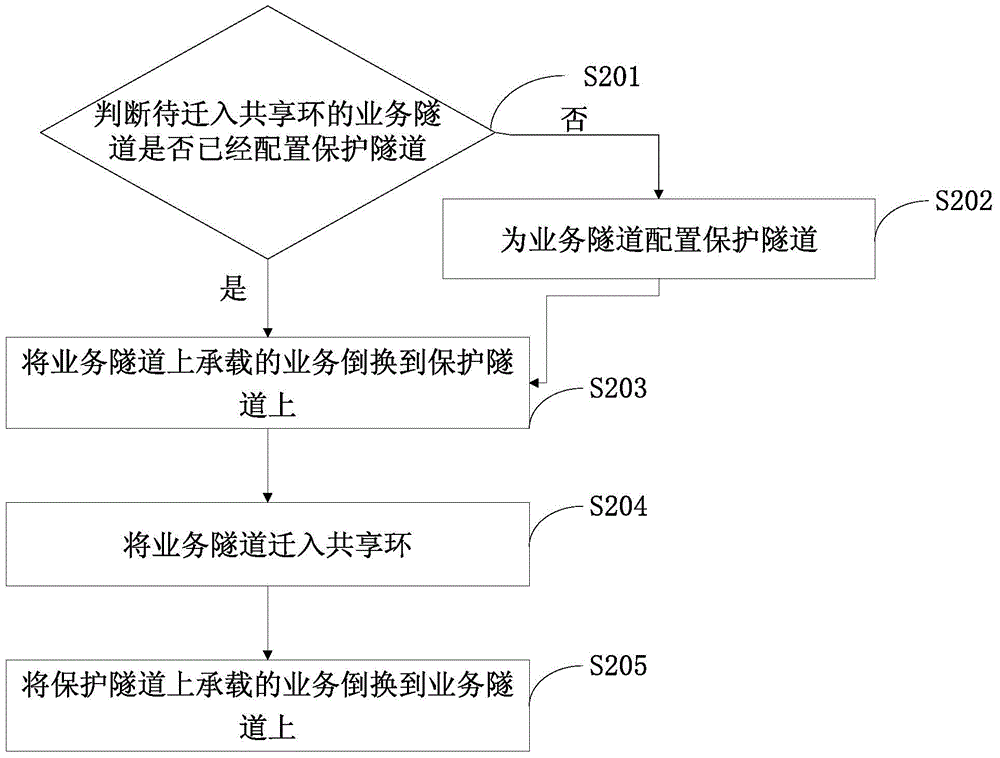
[0039] This embodiment provides a method for migrating a service tunnel to a shared ring. For details, see figure 2 ,include:
[0040]Step S201: Determine whether the service tunnel to be migrated into the shared ring has been configured with a protection tunnel, if not, execute step S202, and if yes, execute step S203.
[0041] Step S202: Configure a protection tunnel for the service tunnel.
[0042] Step S203: Switch the service carried on the service tunnel to the protection tunnel.
[0043] Step S204: Migrate the service tunnel into the shared ring.
[0044] Step S205: Switch the service carried on the protection tunnel to the service tunnel.
[0045] Before step S201, the method may further include: filtering out service tunnels in the entire network that can be migrated into the shared ring according to the target shared ring, and adding them as service tunnels to be migrated into the queue of service tunnels to be migrated into the shared ring. In this way, batch m...
Embodiment 3
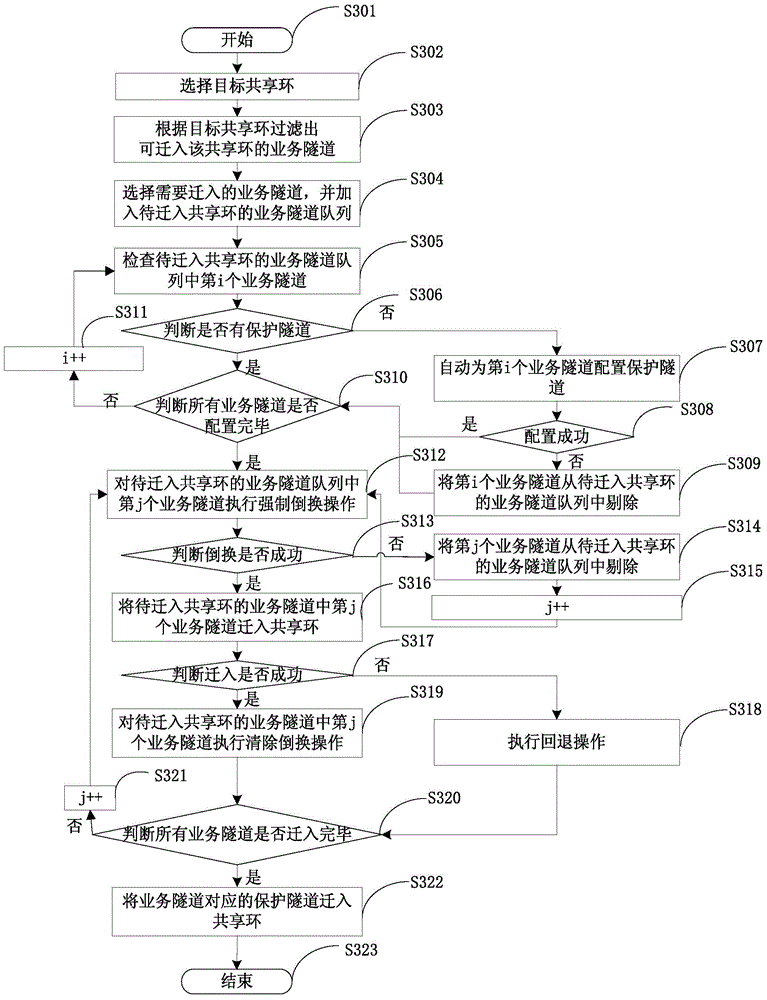
[0051] In order to describe the method for migrating business tunnels to the shared ring in batches mentioned in the second embodiment in more detail, this embodiment provides a method for migrating business tunnels to the shared ring in batches, see image 3 , the method includes the following steps:
[0052] Step S301: start.
[0053] Step S302: Select a target shared ring. The target shared ring is a configured or existing shared ring.
[0054] Step S303: According to the target shared ring, filter out all service tunnels in the entire network that can migrate into the target shared ring.
[0055] Step S304: Select the service tunnels that need to be migrated into the target shared ring according to the engineering application requirements, and add them to the queue of service tunnels to be migrated into the shared ring.
[0056] Step S305: Check the i-th service tunnel in the queue of service tunnels to be migrated into the shared ring. The i starts from 1, indicating ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com