Sensitive word checking method and device
An inspection method and inspection device technology, which is applied in the field of sensitive word inspection methods and devices, can solve the problems of insufficient inspection, time-consuming and labor-consuming, and unsatisfactory inspection results, so as to improve inspection efficiency and solve low inspection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
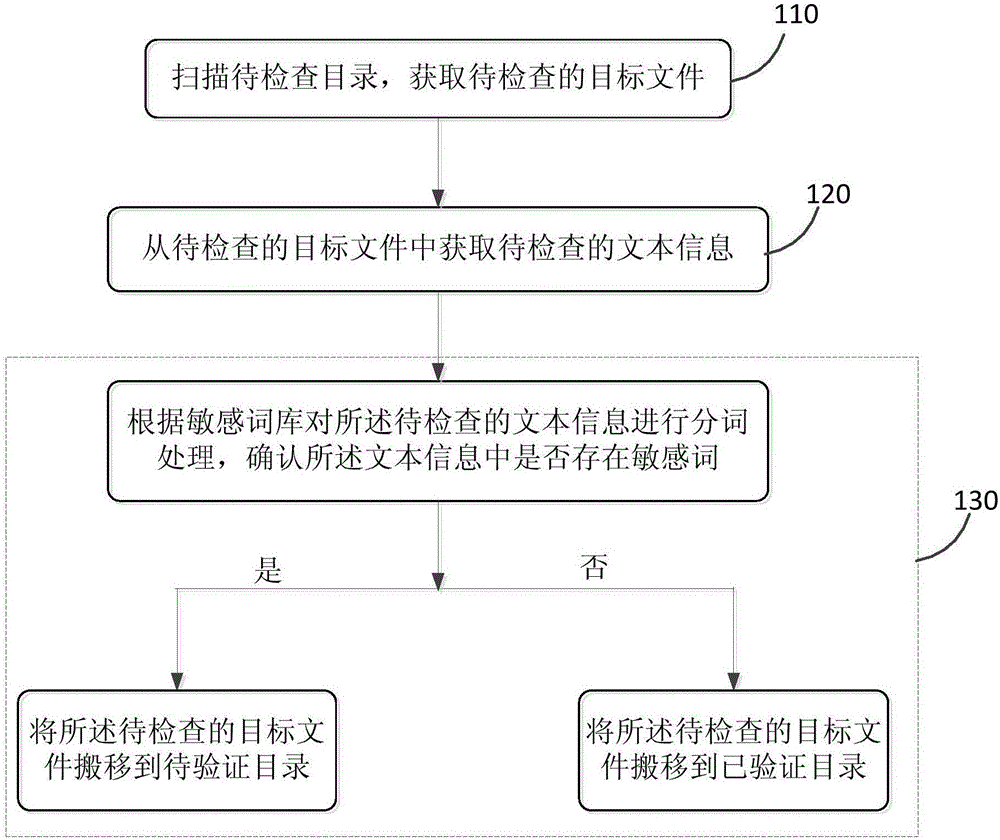
[0025] figure 1 It is a flow chart of a method for checking sensitive words provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of checking files containing sensitive words in storage devices. The method can be executed by the system, and specifically includes the following steps :
[0026] S110. Scan the directory to be checked to obtain the target file to be checked;
[0027] Wherein, the directory to be checked is a folder that can be used to store data in the storage device, and its specific scope can be a system default directory or a directory manually set by itself, which can be all storage space or part of the storage space. The directory to be checked can be scanned by itself at regular intervals, or can be started after receiving a request from the user for scanning.
[0028] The target file to be checked refers to a file whose file type belongs to one of the target file types, and the target file can be suffixes such a...
Embodiment 2
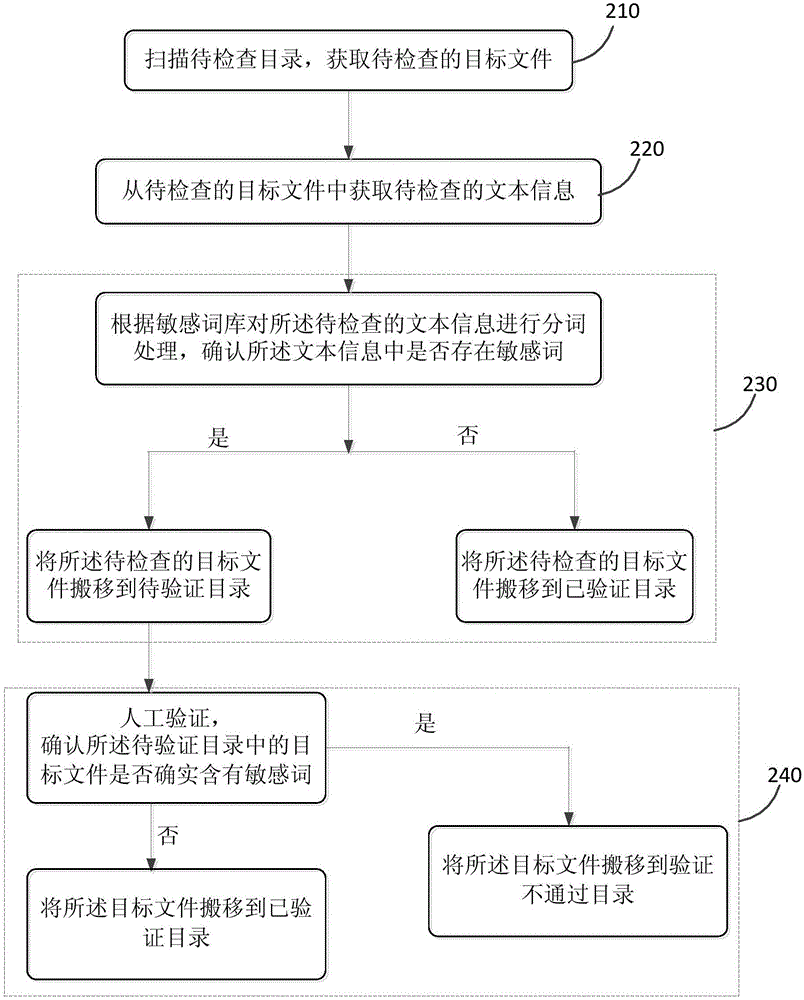
[0044] figure 2 It is a flow chart of another method for checking sensitive words provided by Embodiment 2 of the present invention. In this embodiment, on the basis of the foregoing embodiments, a manual verification step is added.
[0045] The method provided in this embodiment specifically includes the following:
[0046] S210. Scan the directory to be checked to obtain the target file to be checked;
[0047] S220. Obtain the text information to be checked from the target file to be checked;
[0048] S230. Perform word segmentation processing on the text information to be checked according to the sensitive lexicon, confirm whether there are sensitive words in the text information, if there are sensitive words, move the target file to be checked to the directory to be verified, otherwise , and move the target file to be checked to the verified directory.
[0049] S240. If there are sensitive words in the text information, add the corresponding file name of the target fi...
Embodiment 3
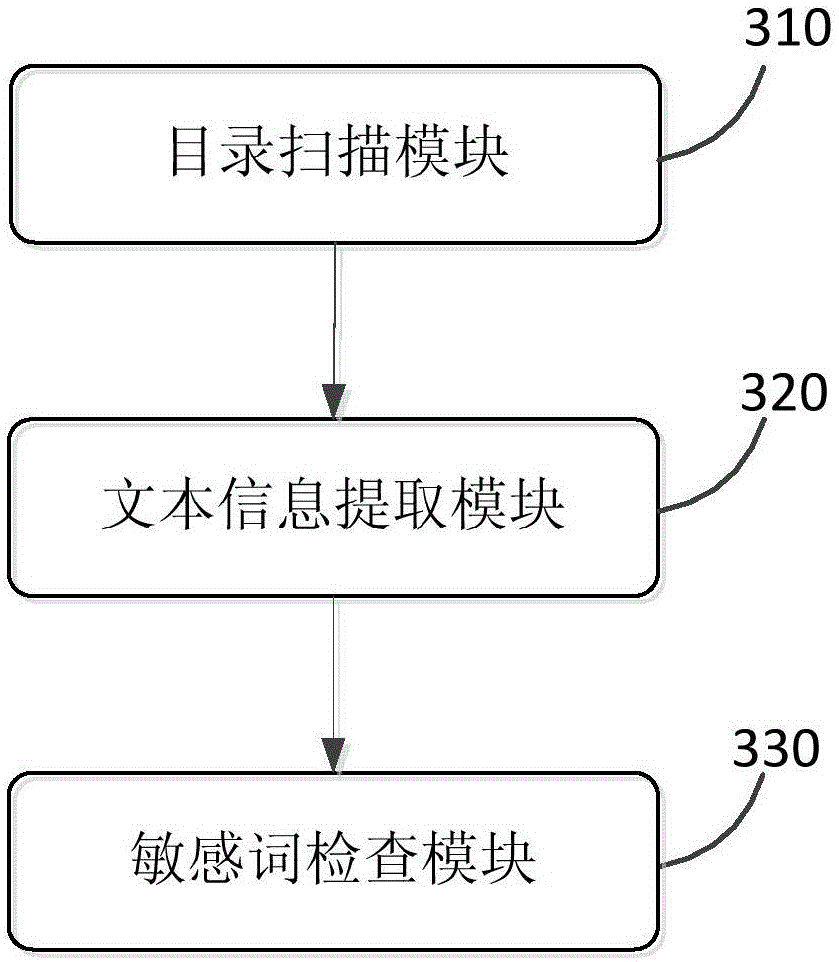
[0057] image 3 It is a sensitive word checking device provided by Embodiment 3 of the present invention, and the device includes: a catalog scanning module 310 , a text information extracting module 320 , and a sensitive word checking module 330 .
[0058] Wherein, directory scanning module 310 is used to scan the directory to be checked to obtain the target file to be checked; text information extraction module 320 is used to obtain the text information to be checked from the target file to be checked; sensitive word checking module 330 uses Perform word segmentation processing on the text information to be checked according to the sensitive lexicon, confirm whether there are sensitive words in the text information; and move the target file to be checked if there are sensitive words in the text information to the directory to be verified, otherwise, move the target file to be checked to the verified directory.
[0059] Further, the target scanning module 310 is specifically...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com