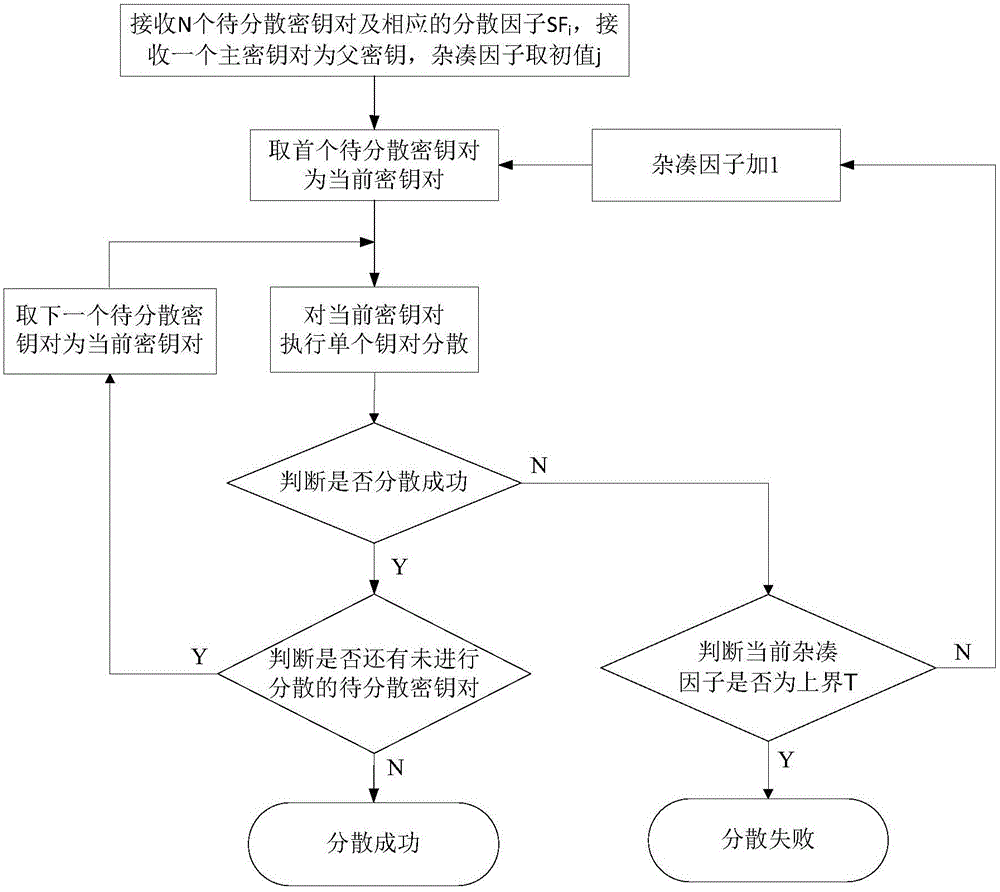
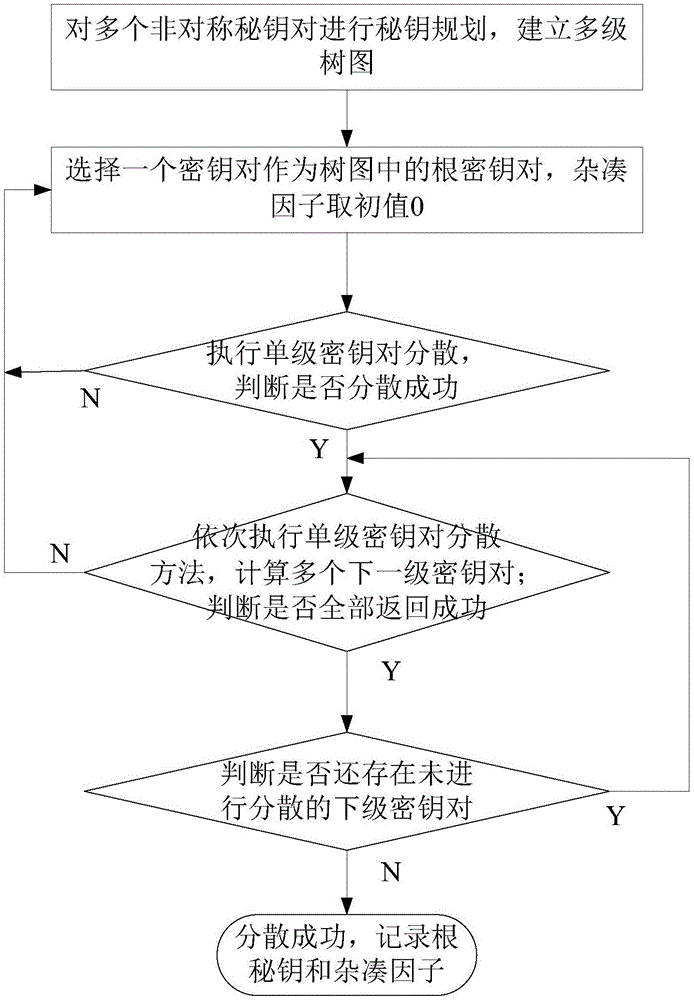
Scatter method and system for single asymmetrical secret key pair, single-stage asymmetrical secret key pair and multistage asymmetrical secret key pair
A key pair, decentralized technology, applied in key distribution, can solve the problem that asymmetric keys cannot be dispersed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0091] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
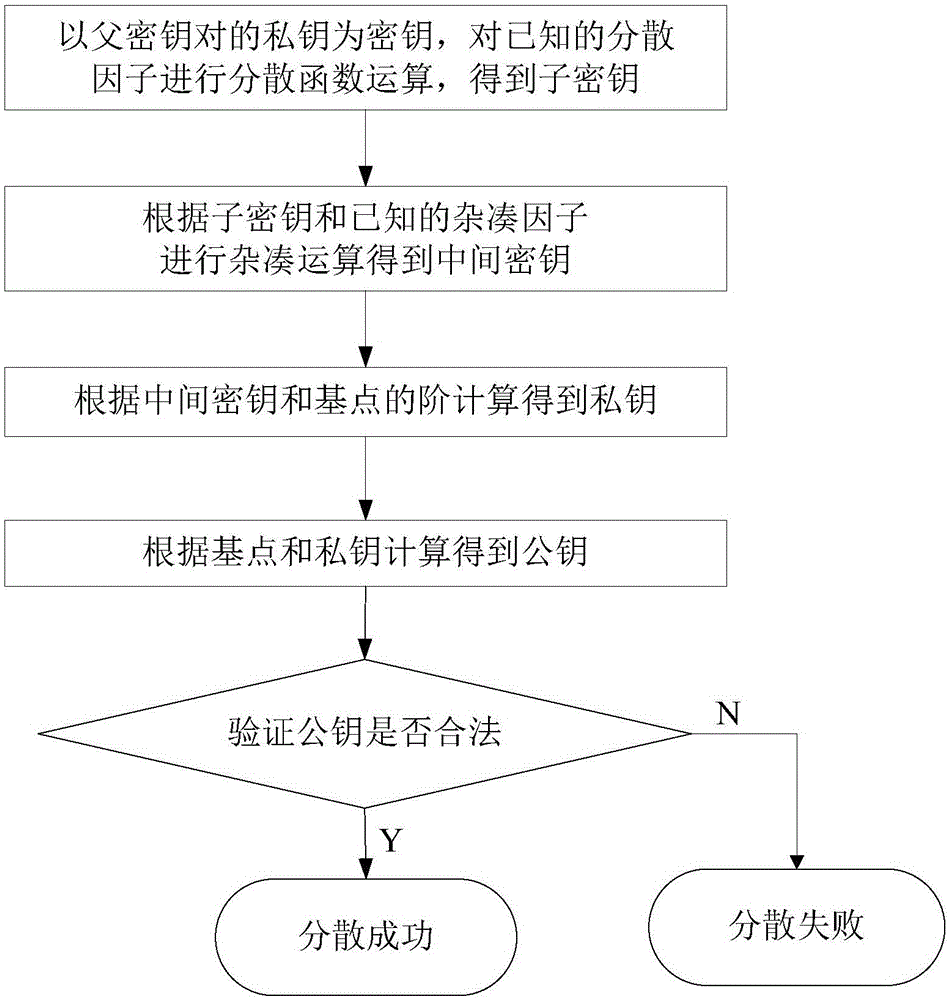
[0092] Such as figure 1 As shown, it is a single key pair dispersion method described in a specific embodiment of the present invention, which specifically includes the following steps:
[0093] Step a1: Take the parent key FK as the key, hash factor ZF=0, and perform the dispersal function S() operation on the known dispersal factor SF to obtain the child key SK. The calculation process is as follows:
[0094] SK=S(FK, SF) formula (1)
[0095] Key distribution algorithms include but are not limited to the following functions:
[0096] a1.1 encrypt the dispersion factor;
[0097] a1.2 Decipher the dispersion factor;
[0098] a1.3 Perform hash operations on the dispersion factors;
[0099] a1.4 Compound operatio...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap