An Encoding Method for Invisible Image Cipher
An image encryption and encoding method technology, applied in the field of image encryption, can solve the problems of strengthening confidential information, geometric shapes are easy to be cracked, copied, stolen, and insufficient information protection, achieving simple encoding rules and preventing reverse identification by people. The effect of extracting information and hidden code is fast
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] The invention discloses a method for encoding invisible image passwords, which is characterized in that the method comprises the following steps:
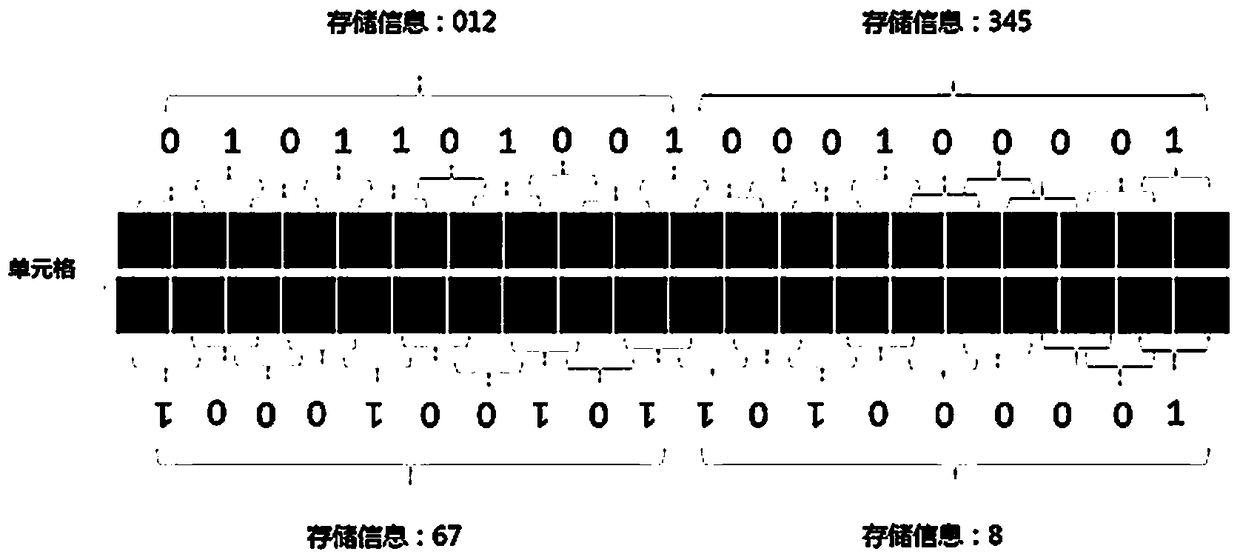
[0030] S101: The system receives the specified picture and encryption request from the client, the encrypted information is such as 123456789; the picture is divided into cells and divided according to the horizontal arrangement;
[0031] S102: Perform CMYK four-color color value calculation on the equally divided cells to form a color value database with different values;
[0032] Such as figure 1 , S103: Comparing the C value color difference between two adjacent cells, CN+m-CN≥0 is defined as 1, and the others are defined as 0, adjacent to that is m=1; comparison results are pre-stored according to rules Assign 1 and 0 to form a new set of source characters composed of "0" and "1" with internal logic basis;
[0033] S104: The above-mentioned source characters take 10 data as a unit, and each unit records different infor...
Embodiment 2
[0037] In the above step S103, for the M-value color value difference comparison, KN+m-KN≥0 is defined as 1, and the others are defined as 0, adjacent to that is m=1; the comparison results are assigned 1 and 0 in pre-stored rules, A new set of source characters composed of "0" and "1" with internal logic basis is formed.
Embodiment 3
[0039] In the above step S103, the CMYK value color value difference is compared, and the color value difference is compared by adding the absolute value of each color value of CMYK, and the large cell item of the serial number is greater than or equal to the small cell item of the serial number according to the definition, which is defined as 1, and other Defined as 0, forming a new set of source characters composed of "0" and "1" with internal logic basis.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com