Control method and system for access control
An access control and central control module technology, applied in the field of access control methods and systems, can solve problems such as difficulty in meeting the real-time requirements of the access control system, time-consuming, etc., and improve recognition efficiency, recognition accuracy, safety and reliability. The effect of high and shortened face contrast time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
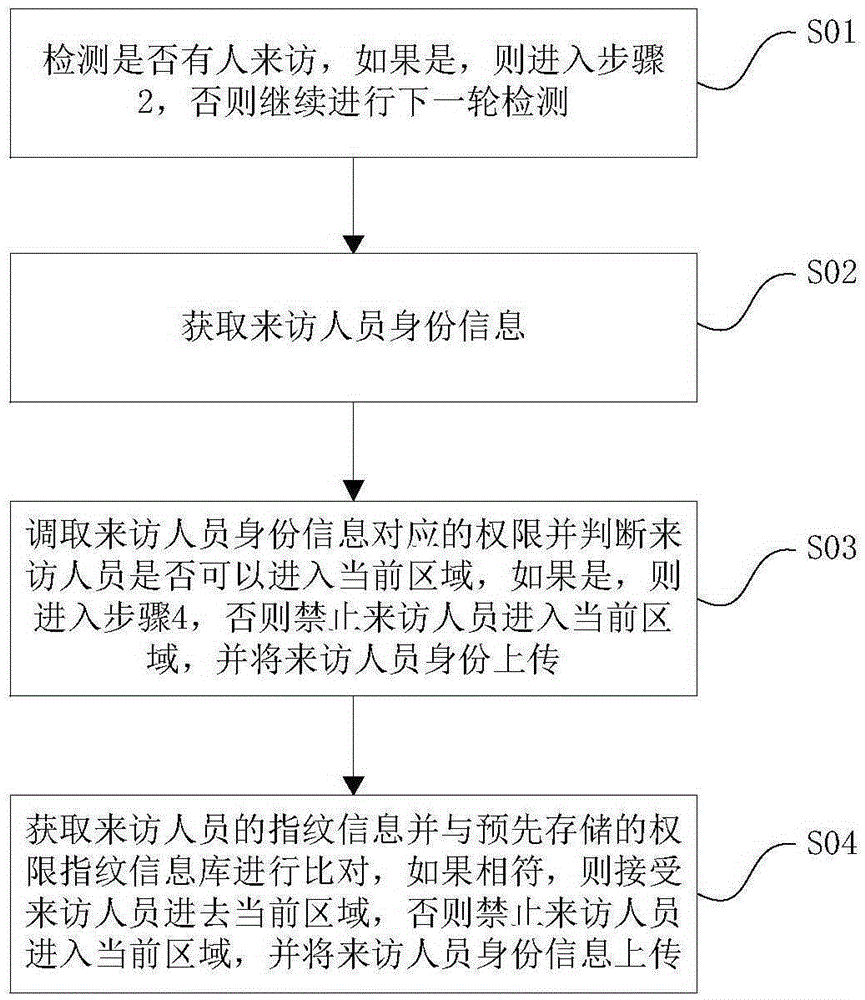
[0016] Embodiment one, a kind of door access control method, will be combined with the following figure 1 An access control method of the present invention is described in detail.
[0017] Such as figure 1 As shown, a flow chart of an access control method, including:
[0018] Step 1: Detect whether someone is visiting, if yes, go to step 2, otherwise continue to the next round of detection;
[0019] Step 2: Obtain the identity information of the visitor;
[0020] Step: 3: transfer the authority corresponding to the identity information of the visitor and judge whether the visitor can enter the current area, if yes, then enter step 4, otherwise the visitor is prohibited from entering the current area, and the identity of the visitor is uploaded;
[0021] Step 4: Obtain the fingerprint information of the visitor, and compare the fingerprint information of the visitor with the pre-stored authority fingerprint information database. If the two are consistent, the visitor is acc...
Embodiment 2
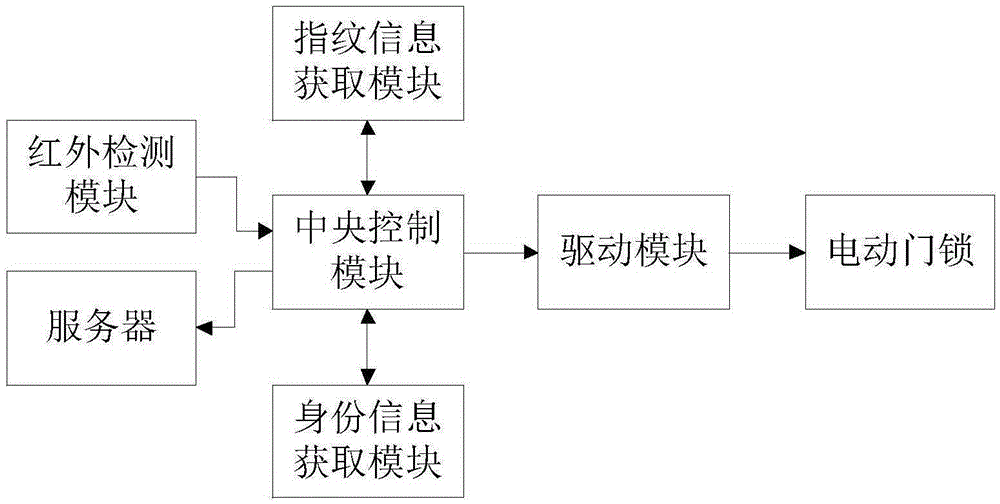
[0030] Embodiment two, a kind of entrance guard control system, will be combined with the following figure 2 An access control system of the present invention is described in detail.
[0031] Such as figure 2 As shown, a structural diagram of an access control system includes an infrared detection module, a central control module, an identity information acquisition module, a fingerprint information acquisition module, a drive module, an electric door lock and a server.
[0032] Wherein, the infrared detection module is used to detect whether someone is visiting; the central control module includes a starting unit, a first judging unit and the second judging unit; The identity information acquisition module sends the first start command; the first judging unit is used to receive the identity information of the visitor and transfer the authority corresponding to the identity information of the visitor, and judge whether the visitor can enter the current area, and if so, to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com