Access control method and system
An access control and personnel technology, which is applied in the direction of instruments, time registers, and individual input/output registers, etc., can solve the problems of poor real-time performance of the access control system, shorten the face comparison time, improve real-time performance, The effect of high safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
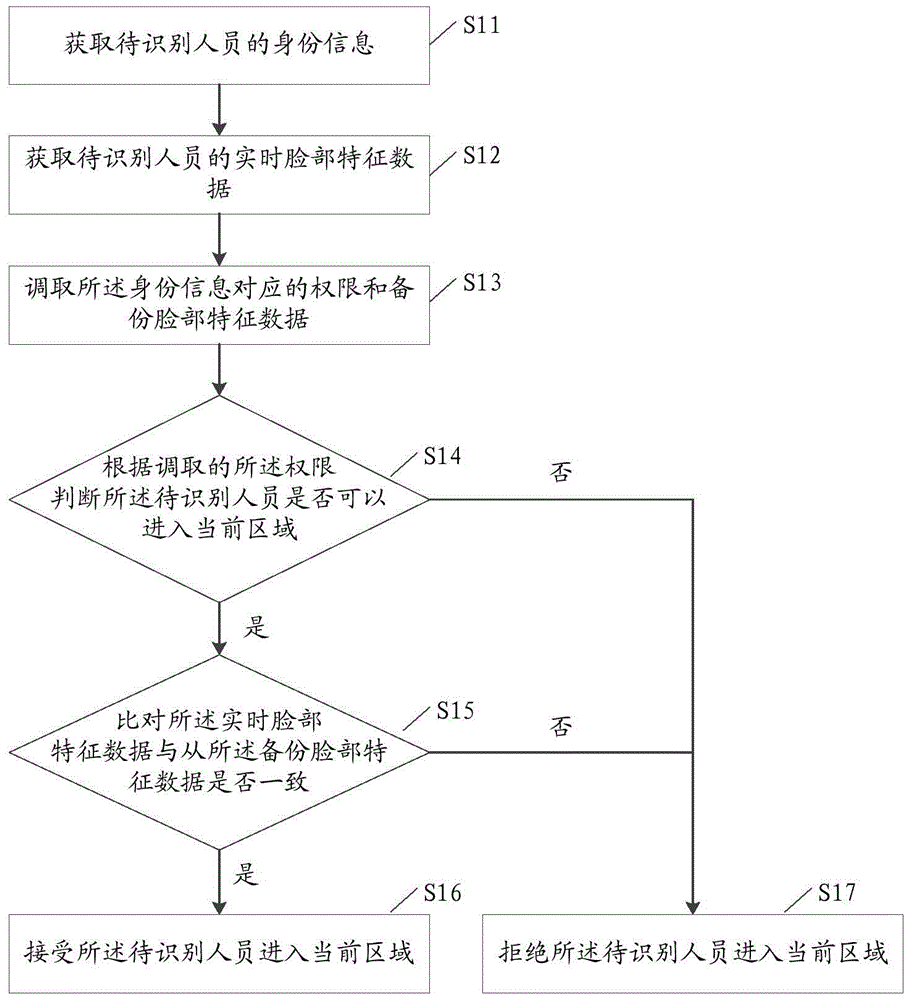
[0022] figure 1 An access control method according to Embodiment 1 of the present invention is shown, the method includes the following steps:
[0023] S11. Obtain the identity information of the person to be identified. The identity information may be an access control card number, or an ID card number, or a fingerprint. Correspondingly, the way to obtain the identity information may be to swipe the access control card of the person to be identified, or swipe the second-generation ID card, or enter fingerprints as required.
[0024] S12. Obtain real-time facial feature data of the person to be identified.
[0025] S13. Retrieving the authority corresponding to the identity information and backing up facial feature data. A personnel information database can be established in advance, which includes basic information data and backup facial feature data of each employee. Among them, the basic information includes the employee's name, gender, department, job number, access co...
Embodiment 2
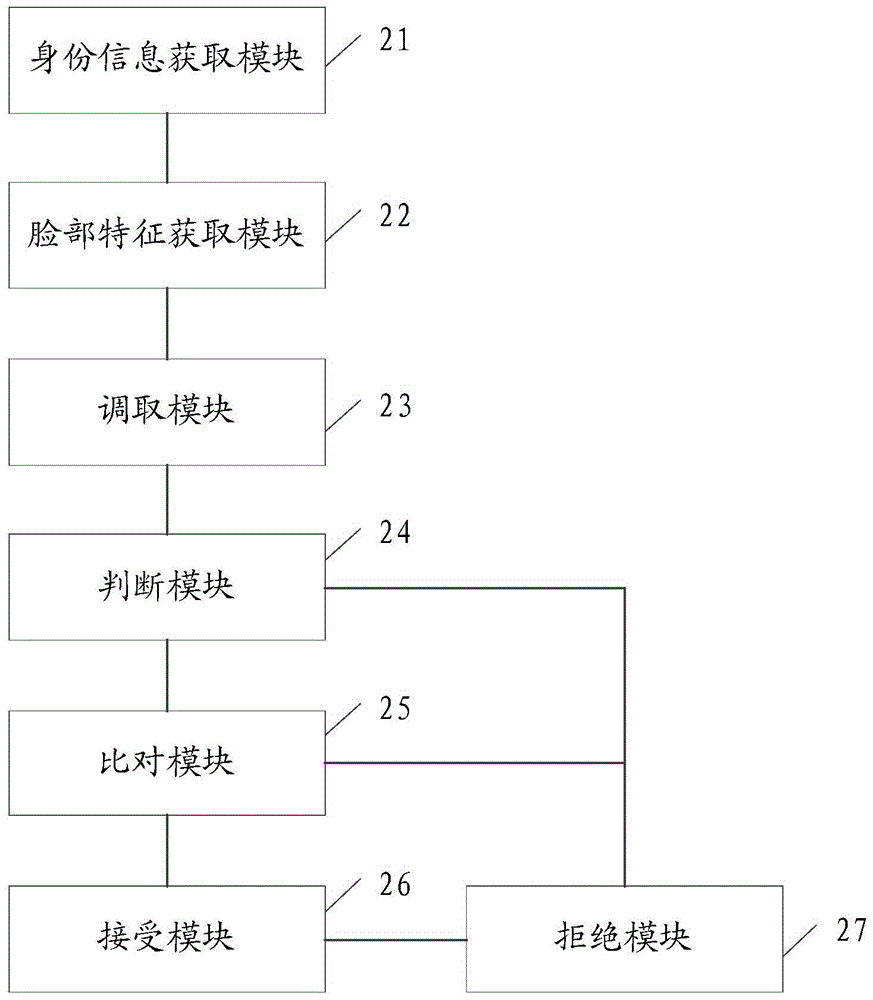
[0047] image 3 An access control system according to Embodiment 2 of the present invention is shown, which includes an identity information acquisition module 21, a facial feature acquisition module 22, a call module 23, a judgment module 24, a comparison module 25, an acceptance module 26 and a rejection module. Module 27.
[0048] The identity information acquisition module 21 is used to acquire the identity information of the person to be identified. The facial feature acquisition module 22 is used to acquire real-time facial feature data of the person to be identified. The calling module 23 is used to call the authority corresponding to the identity information and the backup facial feature data. The judging module 24 is used for judging whether the person to be identified can enter the current area according to the invoked authority. The comparison module 25 is used to compare whether the real-time facial feature data is consistent with the backup facial feature data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com