A Secret Handshake Method Based on Lattice Cipher
A technology of secret handshake and lattice cipher, which is applied in the field of communication, can solve problems such as no solution, and achieve the effect of meeting security and confidentiality requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0043] Symbol Description:
[0044] Matrix: Bold capital letters, such as M
[0045] Vector: lowercase letters plus arrows, such as
[0046] The i-th element in the vector: the vector is subscripted, such as
[0047] For convenience, a vector is sometimes also treated as a string.
[0048] String length in bits: |t|
[0049] Connection between strings: s||t
[0050] XOR of strings: s⊕t
[0051] String from left to right l bit: |s| l
[0052] String from right to left l bit: |s| l
[0053] Orthogonal vector matrix: By the vector {s in the matrix S 1 ,s 2 ,...,s k}Obtained by Gram-Schmidt orthogonalization
[0054] Gram-Schmidt specification: The maximum two-dimensional distance of vectors in matrix S, ie max 1≤i≤k ||s i ||
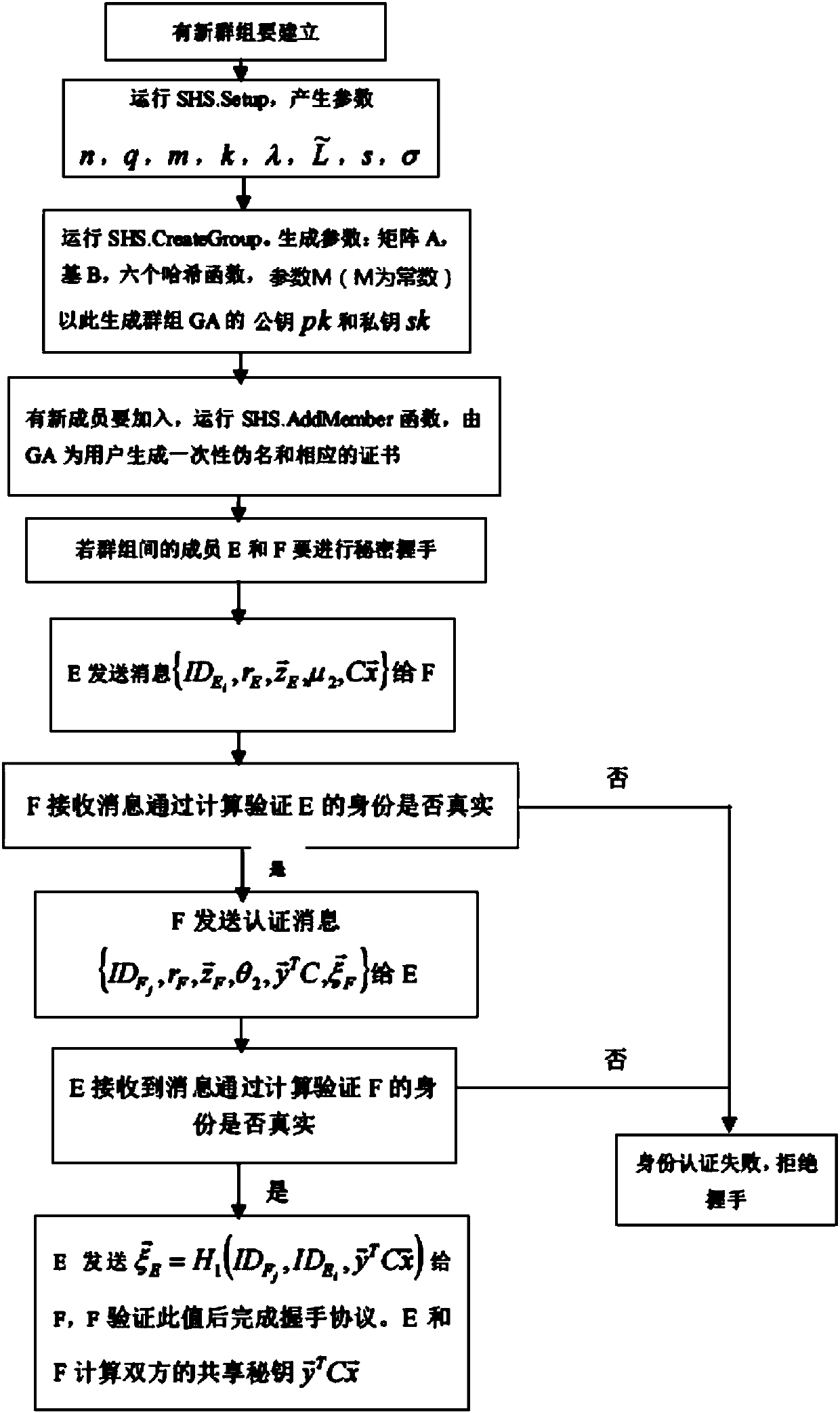
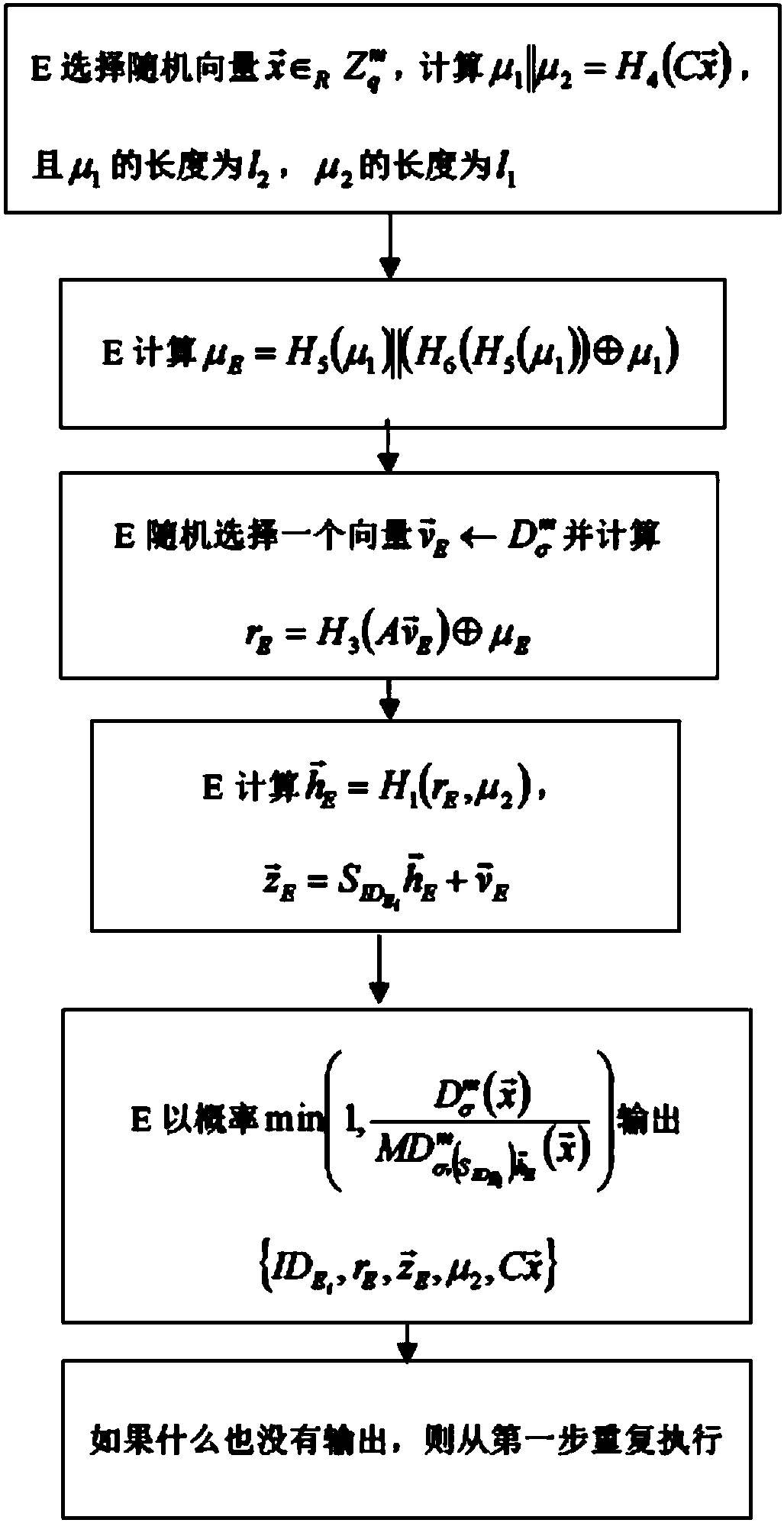
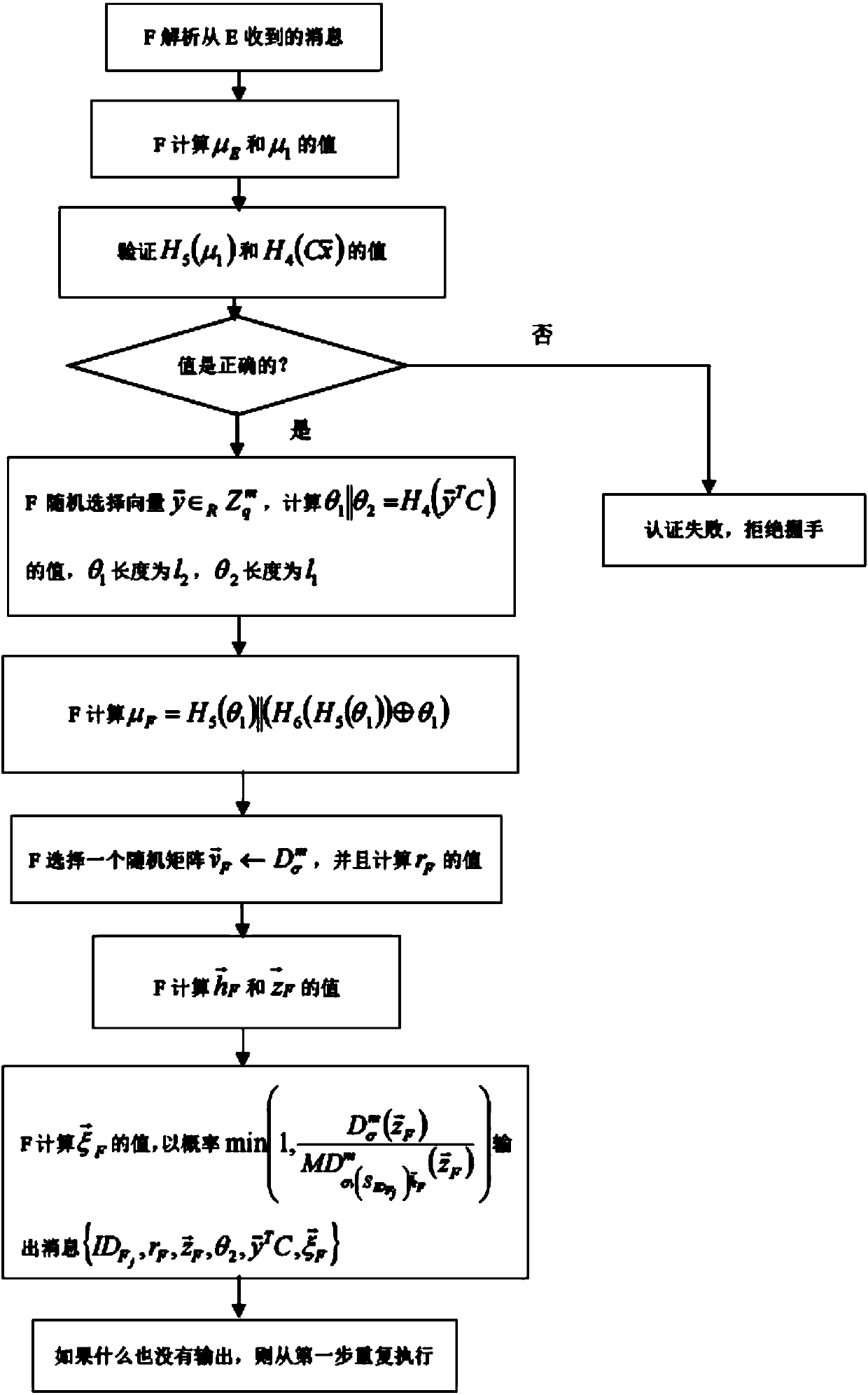
[0055] Such as Figure 1-5 Shown, the whole process of the scheme of the present invention is as follo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com