Secure non-embedded steganography method based on generative adversarial network
A safe and steganographic technology, applied in the field of information security, can solve the problems of dissatisfaction, low embedding capacity, low recovery accuracy, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
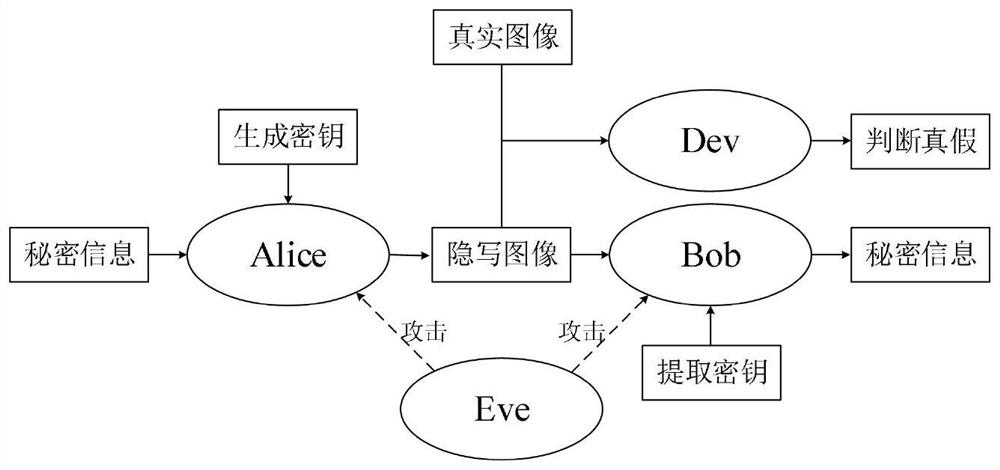
[0057] In this example, see figure 1 , a secure embedding-free steganography method based on generative adversarial networks, is applied in a network environment composed of a sender, a receiver, a discriminator and a third party, and proceeds as follows:
[0058] Step 1. Use the openssl tool to generate a key pair, including: generate the key en_key and extract the key de_key;
[0059] Step 2. The third party distributes the generated key en_key to the generator, and distributes the extraction key de_key to the extractor;
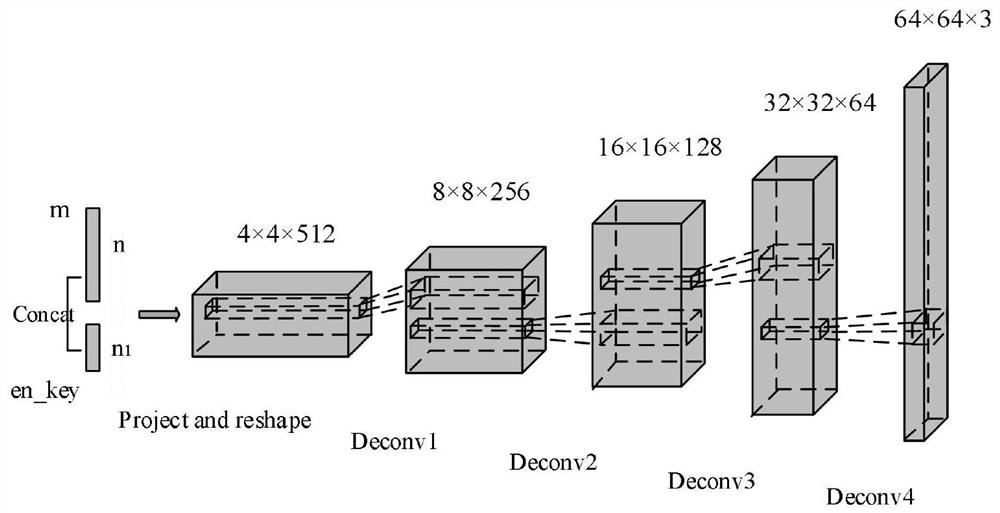
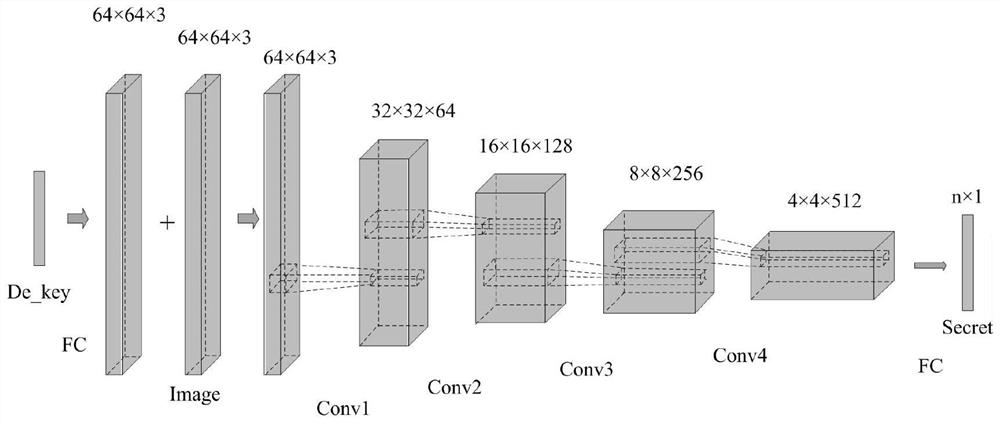
[0060] Step 3. Train a GAN-based secure embedding-free steganographic model:
[0061] Step 3.1, obtain a real image set and use it as a pre-training data set w;
[0062] In a specific embodiment, the image data set FFHQ is used as the pre-training data set. The dataset contains 70,000 128×128×3 high-definition face images, and these photos have strong diversity, including age, accessories (glasses, hats), etc.
[0063] Step 3.2, let the safe embedding-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com