Screen unlocking method and screen unlocking apparatus
A screen unlocking and unlocking technology, applied in the field of communication, can solve the problem of poor security of touch screen terminals, and achieve the effect of enhancing security and protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
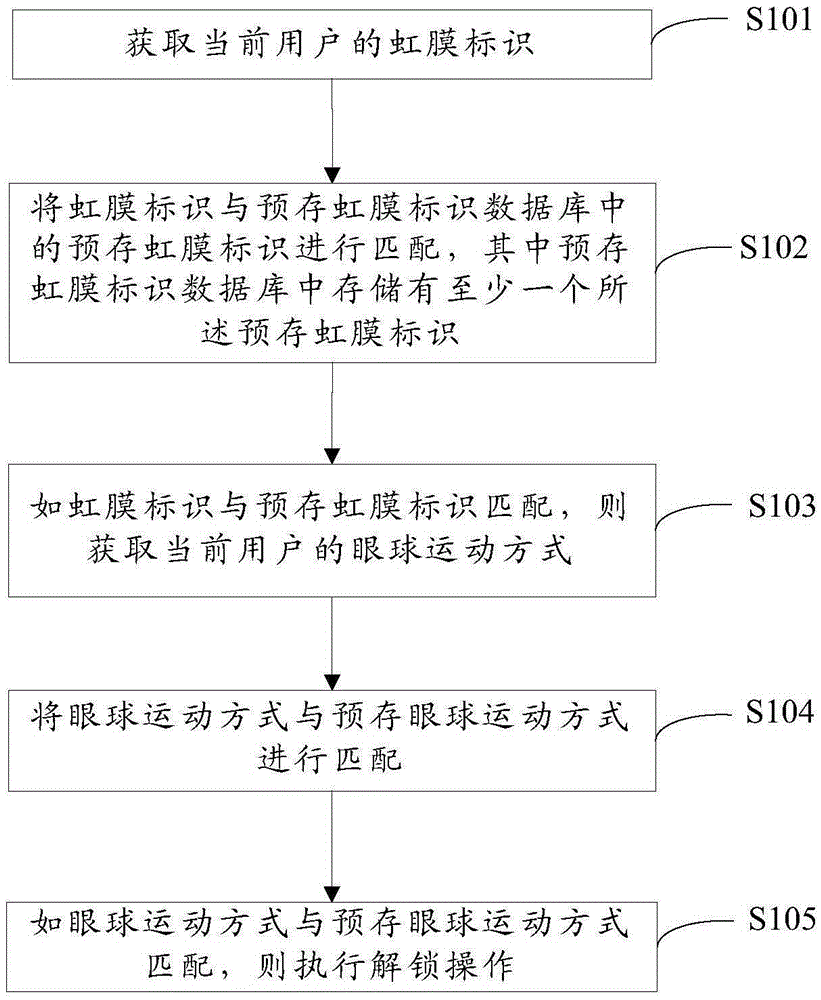
[0033] see figure 1 , figure 1 It is a schematic flowchart of the first preferred embodiment of the screen unlocking method of the present invention. This method is used to unlock the terminal. The terminal can be a mobile phone, a tablet, a personal computer, a notebook computer, etc., an intelligent mobile device with a touch screen, a storage unit, a microprocessor installed, and computing capabilities. Specific limits. The specific steps of the screen unlocking method include:
[0034] Step S101, obtaining the iris ID of the current user;
[0035] Step S102, matching the iris ID with the pre-stored iris ID in the pre-stored iris ID database, wherein at least one pre-stored iris ID is stored in the pre-stored iris ID database;
[0036] Step S103, if the iris ID matches the pre-stored iris ID, obtain the current user's eye movement pattern;
[0037] Step S104, matching the eye movement pattern with the pre-stored eye movement pattern; and
[0038] Step S105, if the eye...
no. 2 example
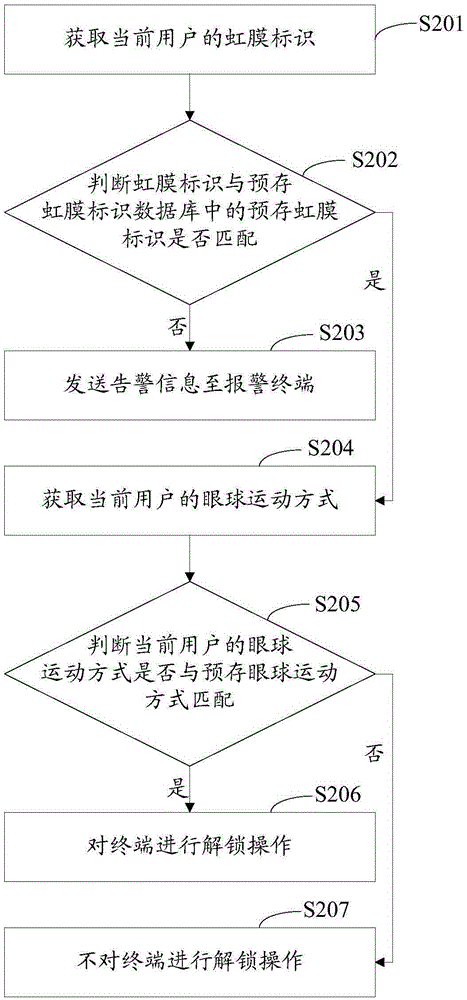
[0055] see figure 2 , figure 2 It is a schematic flowchart of the second preferred embodiment of the screen unlocking method of the present invention. This method is used to unlock the terminal. The terminal can be a mobile phone, a tablet, a personal computer, a notebook computer, etc., an intelligent mobile device with a touch screen, a storage unit, a microprocessor installed, and computing capabilities. Specific limits. The specific steps of the screen unlocking method include:
[0056] Step S201, obtaining the iris ID of the current user;
[0057] Step S202, judging whether the iris ID matches the pre-stored iris ID in the pre-stored iris ID database, wherein at least one pre-stored iris ID is stored in the pre-stored iris ID database;
[0058] Step S203, if the iris ID does not match the pre-stored iris ID in the pre-stored iris ID database, then send an alarm message to the alarm terminal;
[0059] Step S204, if the iris ID matches the pre-stored iris ID in the p...
no. 3 example
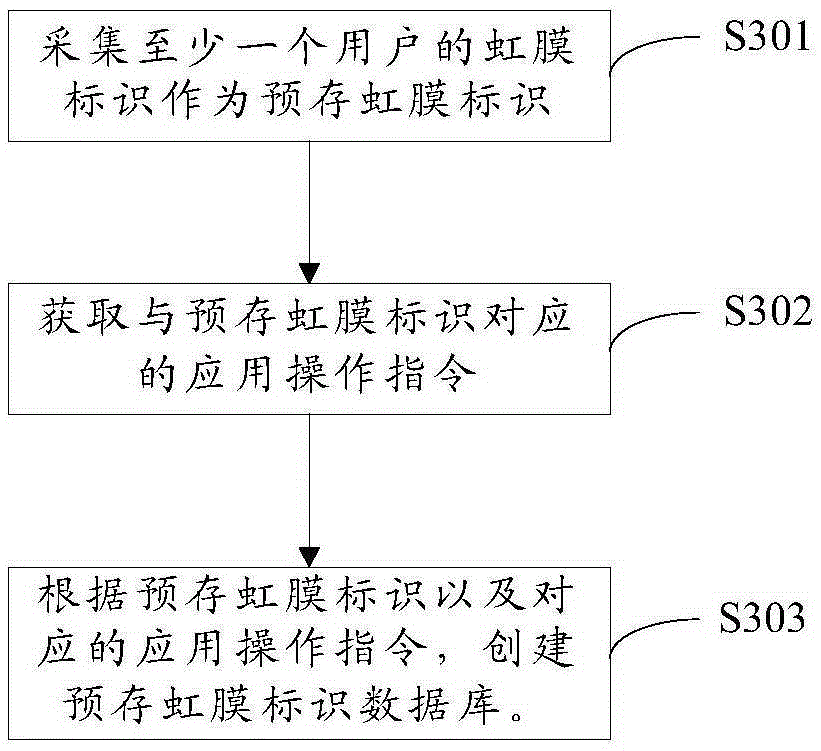
[0099] see Figure 5 , Figure 5is a schematic structural diagram of the first preferred embodiment of the screen unlocking device of the present invention. The screen unlocking device of this preferred embodiment can be implemented using the first embodiment of the screen unlocking method described above. The device is used to unlock the terminal. The terminal can be a mobile phone, a tablet, a personal computer, a notebook computer, etc., an intelligent mobile device with a touch screen, a storage unit, a microprocessor, and computing capabilities. Specific limits.
[0100] The screen unlocking device 50 includes an iris acquisition module 501 , an iris matching module 502 , an eye movement pattern acquisition module 503 , an eye movement pattern matching module 504 and an unlocking module 505 .
[0101] The iris acquisition module 501 is used to obtain the iris identification of the current user; the iris matching module 502 is used to match the iris identification with ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com