Security management method and system based on face identification
A face recognition and management method technology, applied in the field of face recognition-based security management methods and systems, can solve problems such as unavoidable photo deception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
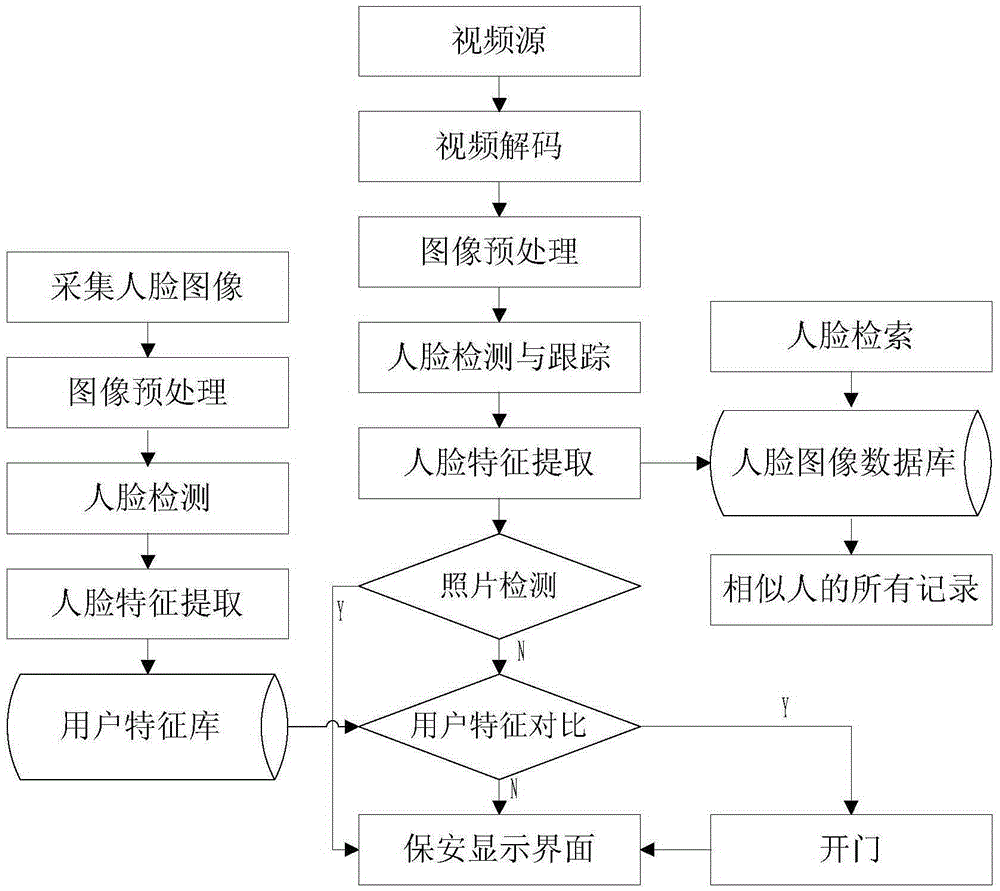
[0021] In a basic embodiment, a security management method based on face recognition is provided, the method includes the following steps:
[0022] S100. Establish a user feature library: collect user information of legal users who are allowed to pass through the access control, the user information includes face images; extract the face features of the face images, and save the face features and the user information to user signature database;
[0023] S200. Extracting the image data of the video frame: obtaining the real-time video of the camera within the security management range, decoding the video, and extracting the image data of the video frame;
[0024] S300. Detecting and extracting facial features: performing face positioning on the image data of the video frame extracted in step S200, and extracting facial features using a deep learning method;
[0025] The facial features include inter-class changes and intra-class changes, the inter-class changes refer to the di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com