Data transmission method and data transmission device
A data transmission method and data frame technology, which are applied in the network field, can solve the problems of unfavorable construction of a super-strong military communication network, military communication network can not take into account confidential communication and network self-healing ability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
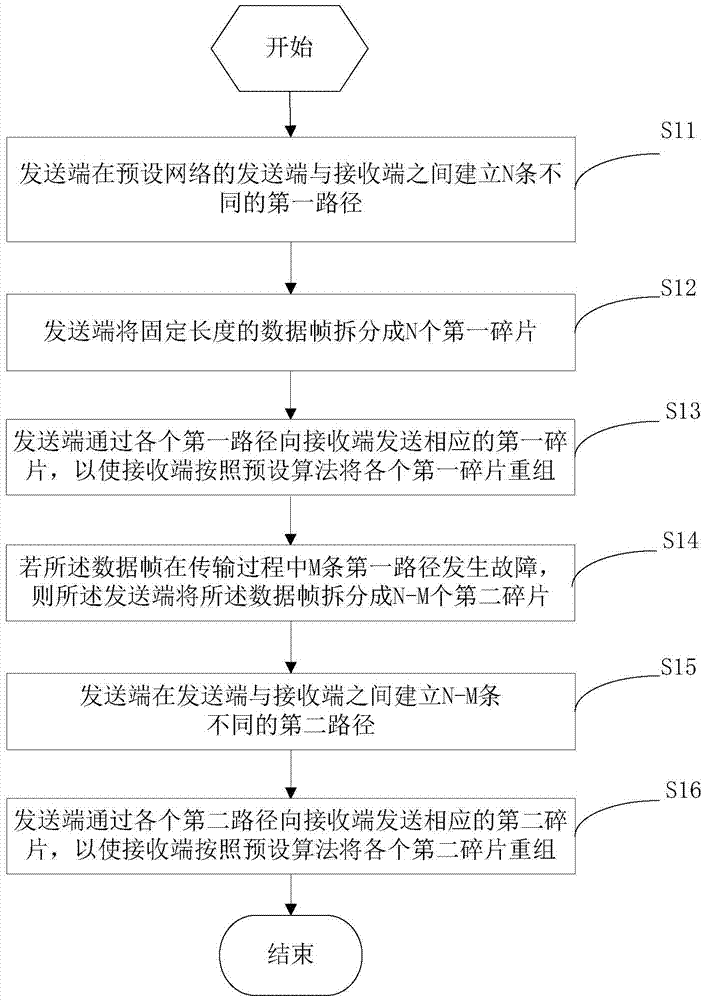
[0046] See figure 1 , which shows a flow chart of the data transmission method provided by this application, which may include the following steps:
[0047] Step S11: The transmitting end establishes N different first paths between the transmitting end and the receiving end in the preset network.
[0048] Wherein, the N is an integer greater than 1.
[0049] Step S12: The sender splits the fixed-length data frame into N first fragments, each of the first fragments corresponds to one of the first paths, and the first paths corresponding to the first fragments are different from each other.
[0050] In this embodiment, the length of the i-th first fragment is The L is the length of the data frame, the P(i) is a random number generated by a preset key according to a preset algorithm, the P(i) is greater than 0 and less than 1, the
[0051] In this embodiment, the preset key and preset algorithm are not limited, as long as application layer encryption is applicable.
[0052...
Embodiment 2
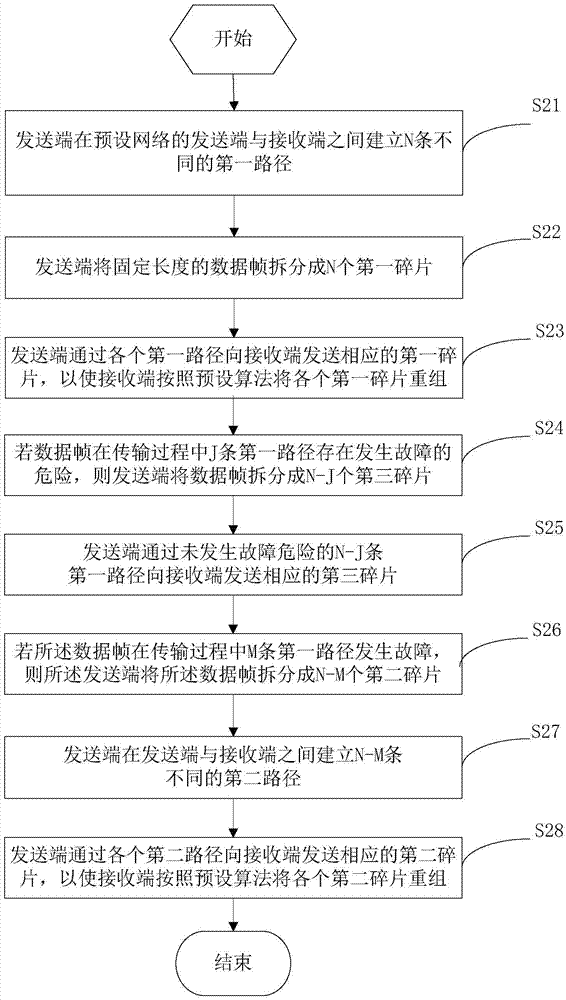
[0073] In this embodiment, in figure 1 On the basis of the data transmission method shown, another data transmission method is extended, please refer to figure 2 , which can include the following steps:
[0074] Step S21: The transmitting end establishes N different first paths between the transmitting end and the receiving end of the preset network.
[0075] Wherein, the N is an integer greater than 1.
[0076] Step S22: The transmitting end splits the fixed-length data frame into N first fragments, each of the first fragments corresponds to one of the first paths, and the first paths corresponding to the first fragments are different from each other.
[0077] In this embodiment, the length of the i-th first fragment is The L is the length of the data frame, the P(i) is a random number generated by a preset key according to a preset algorithm, the P(i) is greater than 0 and less than 1, the
[0078] Step S23: The transmitting end sends the corresponding first fragment...
Embodiment 4
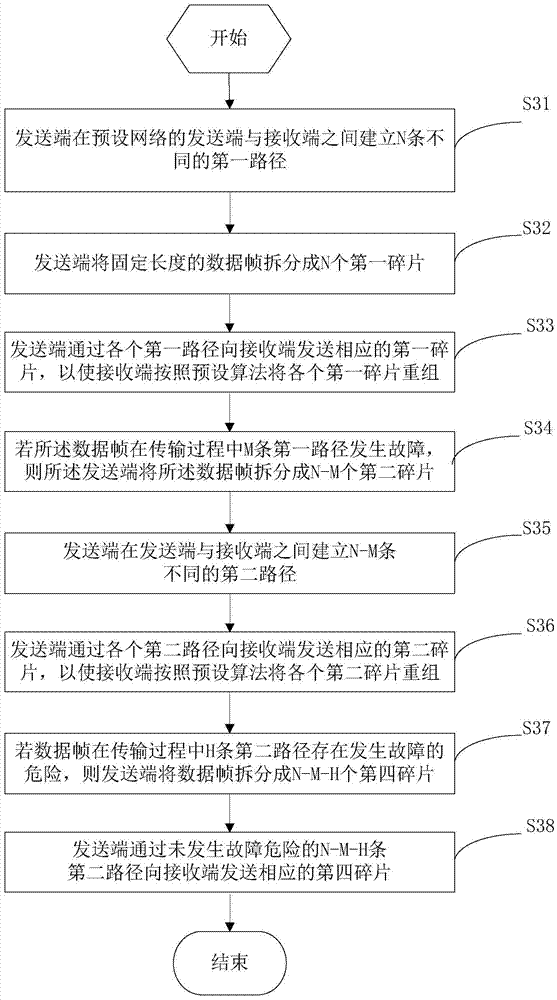
[0107] and figure 1 Corresponding to the data transmission method shown, this embodiment provides a schematic diagram of a logical structure of a data transmission device. Please refer to Figure 4 , the data transmission apparatus includes: a first establishing unit 41 , a first splitting unit 42 , a first sending unit 43 , a second splitting unit 44 , a second establishing unit 45 and a second sending unit 46 .
[0108] The first establishing unit 41 is configured to establish N different first paths between the sending end and the receiving end of the preset network.
[0109] The N is an integer greater than 1.
[0110] The first splitting unit 42 is configured to split the fixed-length data frame into N first fragments, each of which corresponds to one of the first paths, and the first paths corresponding to each of the first fragments are different from each other. , the length of the i-th first fragment is The L is the length of the data frame, the P(i) is a random n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com