Entity authentication method and device based on pre-shared key
A pre-shared key and entity technology, applied in the field of network security, can solve problems such as the inability to determine who the other party is, security risks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
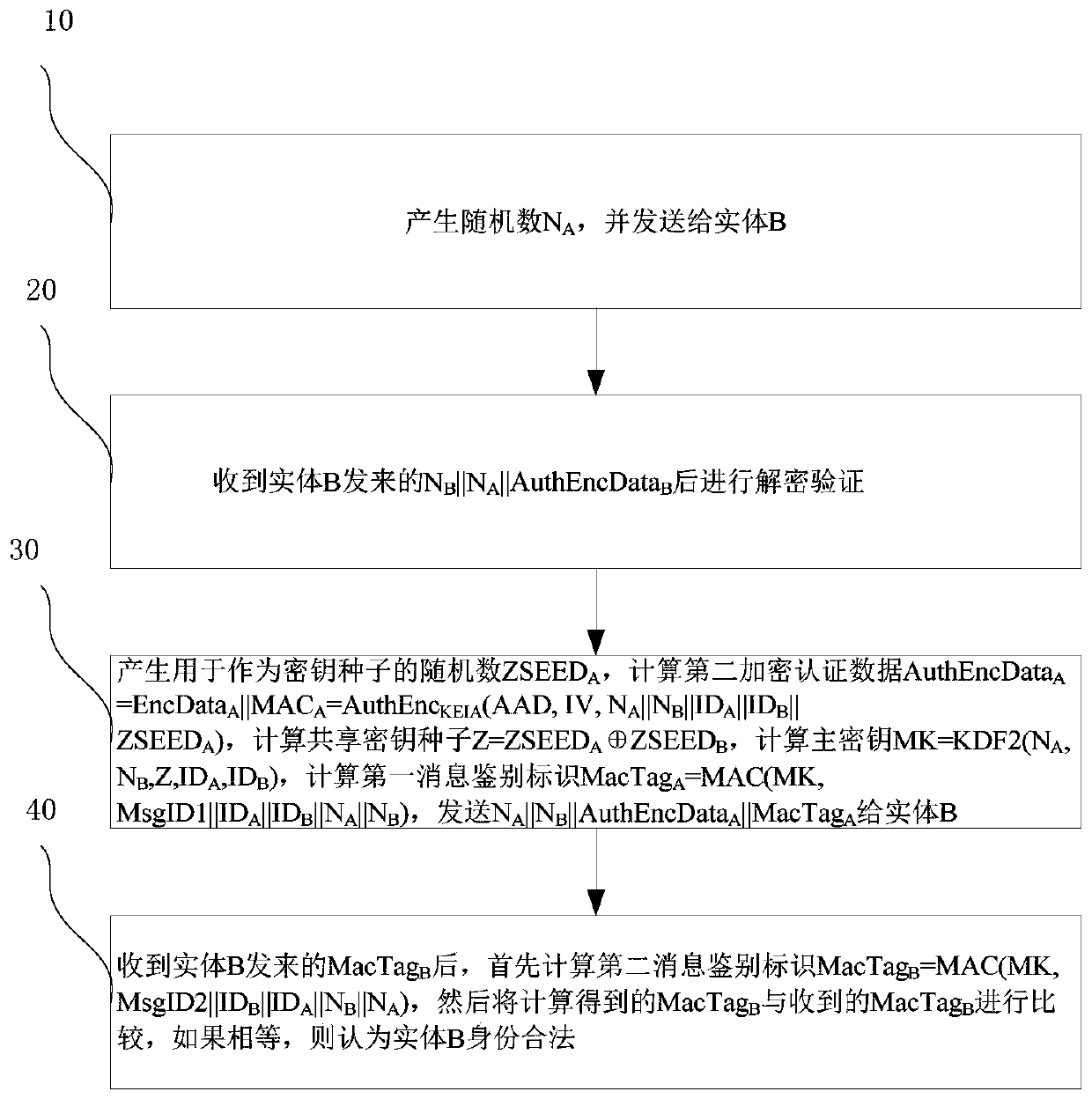
[0045] See figure 1 , the present invention provides an entity authentication method based on a pre-shared key. When the method is implemented, entity A and entity B have shared a pre-shared key (Pre-Shared key, PSK) and know each other's identity , the identity of entity A is ID A , the identity of entity B is ID B , the method includes the following steps:
[0046] Step 1. Entity A generates random number N A , and send to Entity B.
[0047] Step 2. Entity B receives N A After that, generate a random number N B and the random number ZSEED used to seed the key B , calculate the key MKA||KEIA=KDF1(N A ,N B ,PSK,ID A ,ID B ), calculate the first encrypted authentication data AuthEncData B =EncData B ||MAC B =AuthEnc KEIA (AAD,IV,N B ||N A ||ID B ||ID A ||ZSEED B ), Entity B sends N B ||N A ||AuthEncData B to entity A, where AuthEncData B Include EncData B and MAC B , generate by KEIA calculation; MKA is an authentication key, KEIA is a message encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com