Phishing website identification method and device
A technology of phishing websites and identification methods, which is applied in the field of communication, can solve the problems of not being able to be included in time and not be detected, and achieve the effect of high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
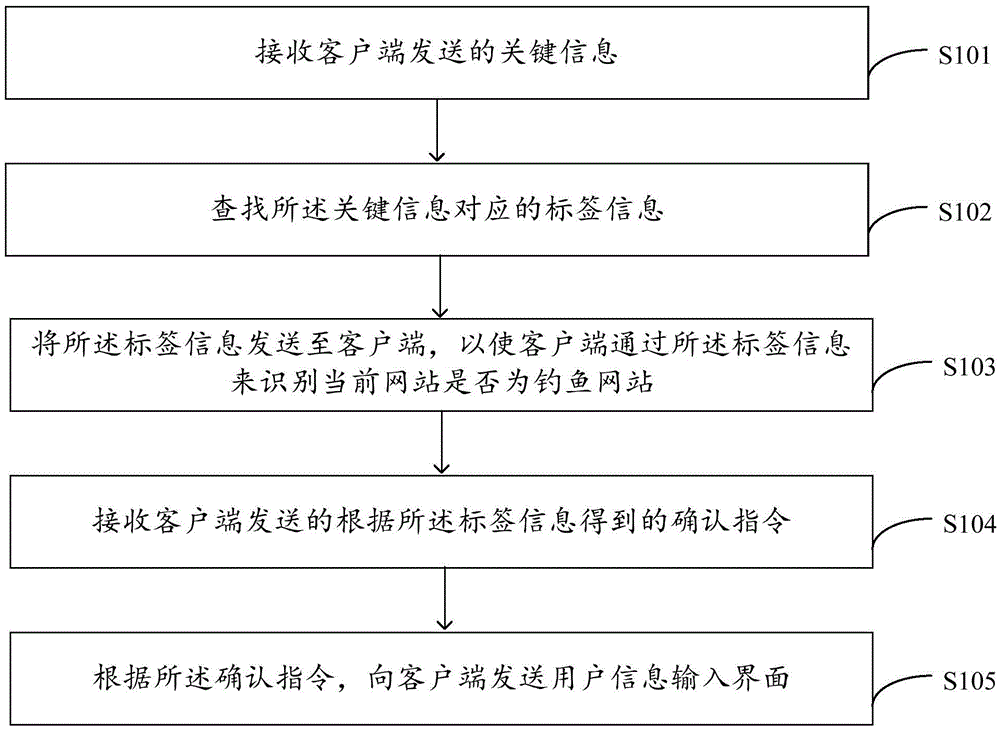
[0044] see figure 1 , shows the method for identifying a phishing website provided by an embodiment of the present invention.
[0045] The method for identifying a phishing website is applied to a server, and specifically includes the following steps:
[0046] In step S101, receive key information sent by the client;
[0047] In step S102, search for tag information corresponding to the key information;
[0048] In the embodiment of the present invention, before the step of receiving the key information sent by the client, the following step is further included: establishing a correspondence table between key information and tag information in advance.
[0049] Then, the step of searching for the tag information corresponding to the key information specifically includes: searching for the tag information corresponding to the key information in the correspondence table.
[0050] In step S103, the tag information is sent to the client, so that the client can identify whether ...
Embodiment 2
[0057] see figure 2 , shows the method for identifying a phishing website provided by an embodiment of the present invention.
[0058] The method for identifying a phishing website is applied to a server, and specifically includes the following steps:
[0059] In step S201, the user name information sent by the client is received;
[0060] In step S202, search for tag information corresponding to the user name information;
[0061] In the embodiment of the present invention, before the step of receiving the user name information sent by the client, the following step is further included: establishing a correspondence table between user name information and tag information in advance.
[0062] Then, the step of searching for the label information corresponding to the user name information specifically includes: searching for the label information corresponding to the user name information in the correspondence table.
[0063] In step S203, the tag information is sent to the...
Embodiment 3
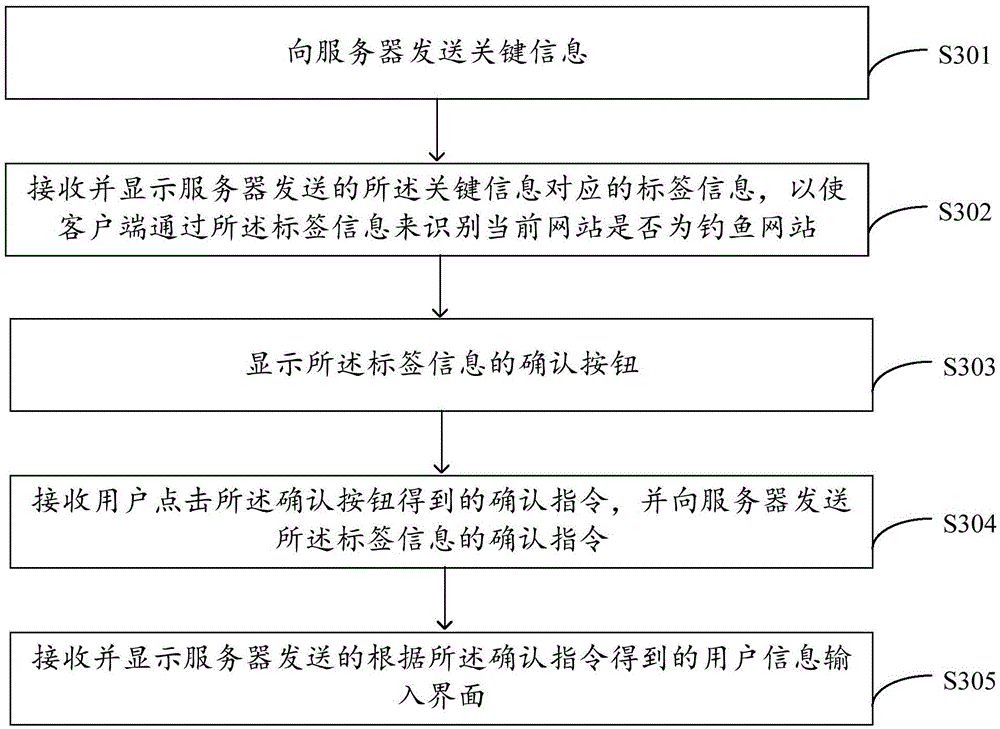
[0069] see image 3 , shows the method for identifying a phishing website provided by an embodiment of the present invention.
[0070] The method for identifying a phishing website is applied in a client browser, and specifically includes the following steps:
[0071] In step S301, send key information to the server;
[0072] In step S302, receiving and displaying the label information corresponding to the key information sent by the server, so that the client can identify whether the current website is a phishing website through the label information;
[0073] In step S303, a confirmation button of the label information is displayed;
[0074] In step S304, receiving a confirmation instruction obtained by the user clicking the confirmation button, and sending the confirmation instruction of the tag information to the server;
[0075] In step S305, the user information input interface obtained according to the confirmation instruction sent by the server is received and displ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com