Data processing method and terminal
A data processing and terminal technology, applied in the field of data security, can solve problems such as system crashes, security risks, technology leakage, etc., and achieve the effect of preventing misoperation and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
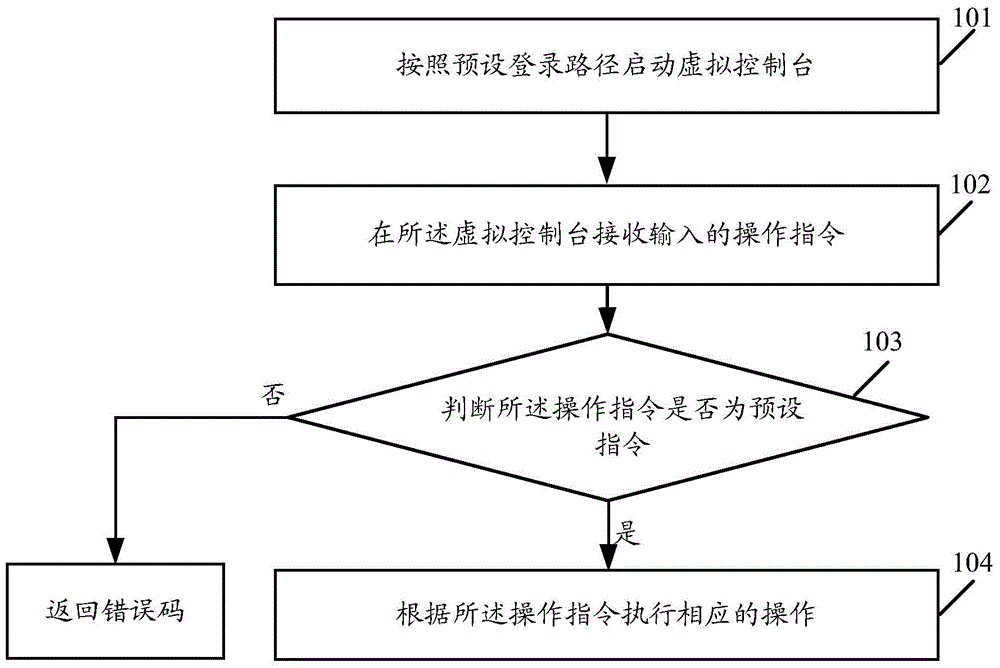
[0142] As a possible implementation manner, the preset login path includes:
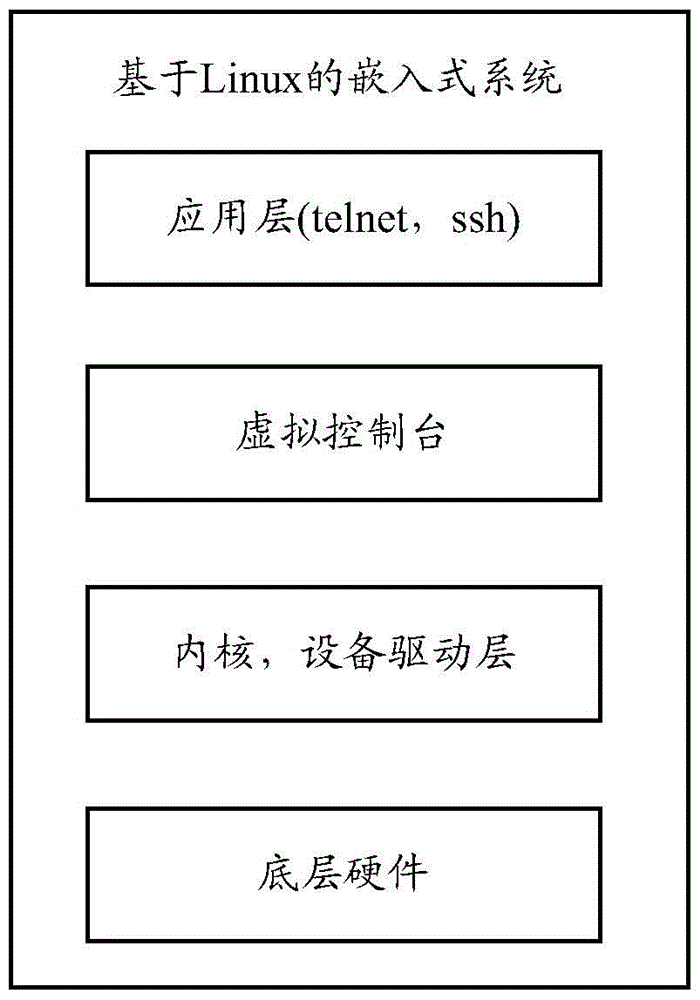
[0143] In the source code of the operating system of the terminal, replace the line code ttyS0::respawn:- / bin / sh in the script file / etc / inittab with ttyS0::respawn: / sbin / virtualconsole-LttyS0115200vt100;
[0144] and / or,
[0145] In the / etc / passwd configuration file, replace the line containing the root character with root:x:0:0:root: / root: / sbin / virtualconsole.
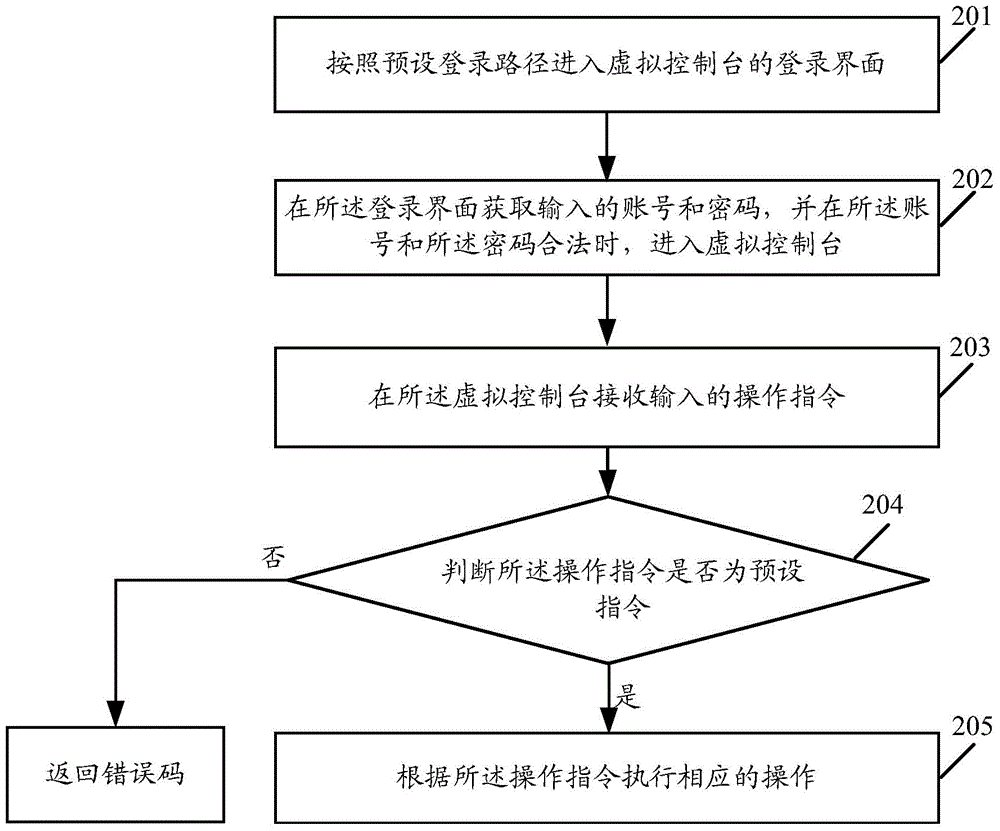
[0146] Optionally, the processor 3000 starts the virtual console according to a preset login path, including:
[0147] Follow the preset login path to enter the login interface of the virtual console;
[0148] Obtain the input account number and password on the login interface, and enter the virtual console when the account number and the password are valid.
[0149] Optionally, after the processor 3000 determines whether the operation instruction is a preset instruction, it is further specifically used to:
[0150] If not, an error ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com