An identity authentication method in the quantum key application process
A quantum key and identity authentication technology, which is applied in the field of identity authentication in the quantum key application process, can solve the problems that the quantum state cannot be accurately measured, and the quantum state cannot be copied, so as to reduce the difficulty and strongly resist replay attacks , Improve the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below in conjunction with the accompanying drawings and examples, but the protection scope of the present invention is not limited thereto.
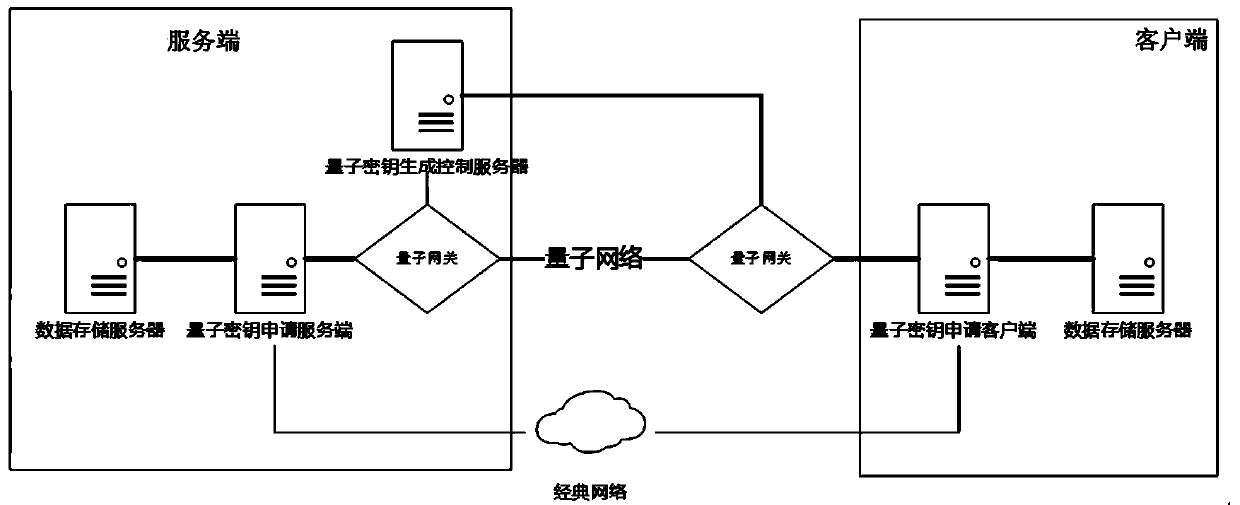
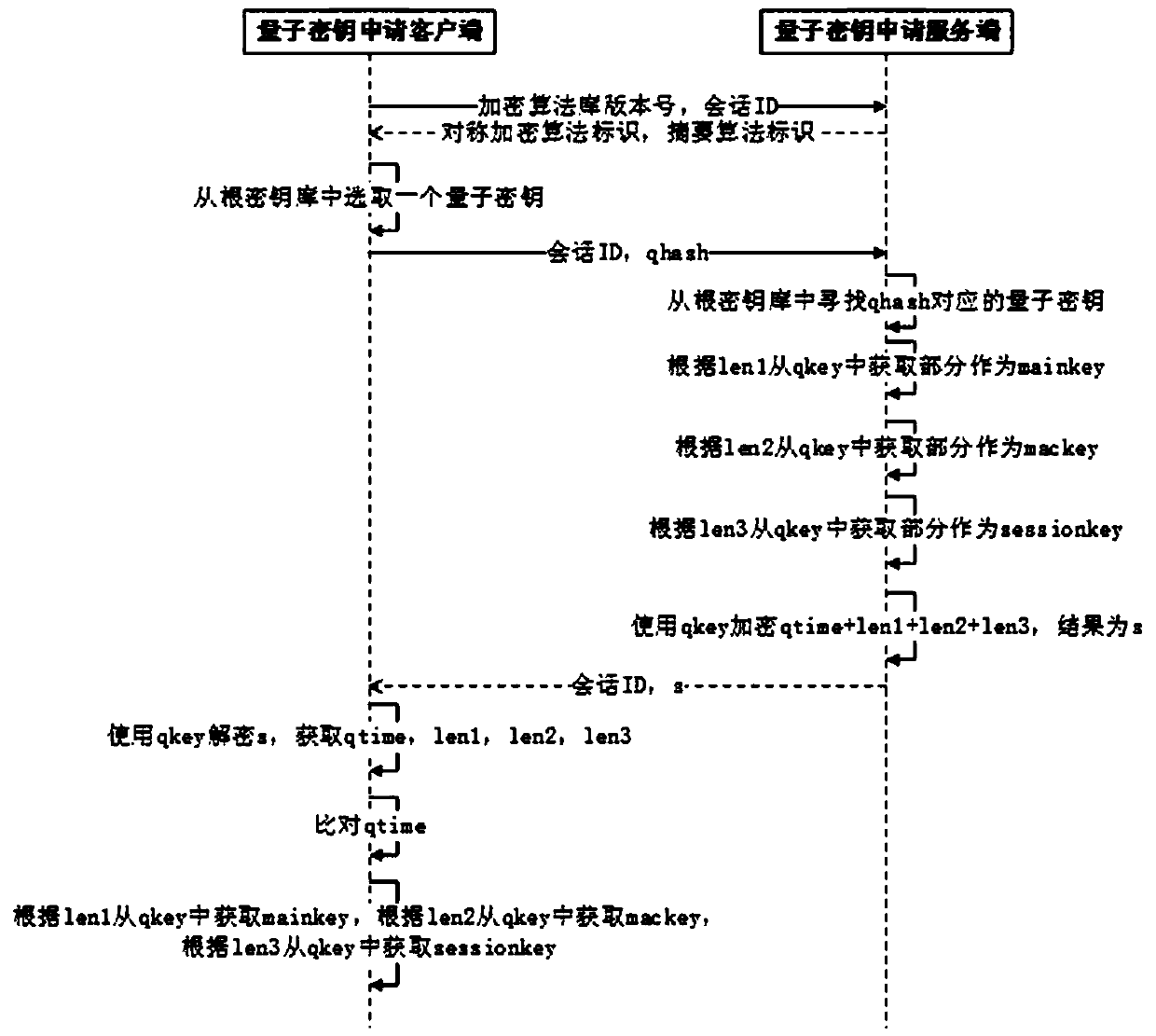
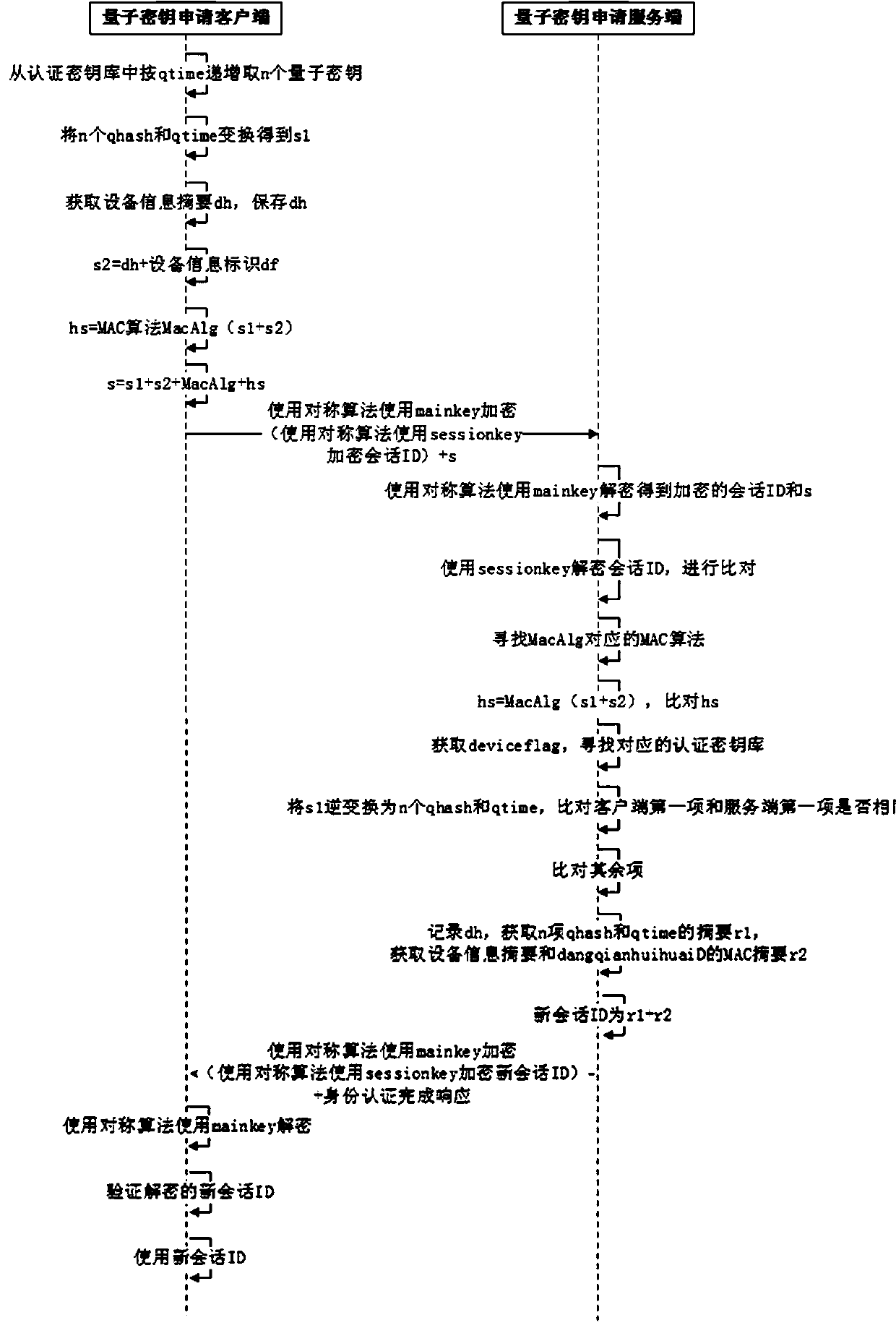
[0030] refer to Figure 1-4 , the present invention a kind of identity authentication method in quantum key application process, comprises the following steps:
[0031] S1. Quantum network deployment stage; the present invention includes a client, a server, and a quantum network connecting the two. The quantum network includes two channels, namely, a quantum channel and a classical channel. The quantum channel is used to distribute quantum keys , the classical channel is used to transmit classical information other than quantum keys. The client and server have their own quantum gateways, encryption algorithm libraries, and hash algorithm libraries. The server also has a data storage server. At the beginning, the operation is carried out by trusted staff as follows: the c...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap